Microsoft Overtakes Facebook as Most Imitated Brand in Q4 2025 Phishing Attacks

Key Takeaways
- Urgency and pressure are common scam tactics
- Verify the sender and URL by using official channels
- Never share passwords or one-time codes through messages
- If you clicked, change passwords and review account activity
- Real-time warnings can help stop lookalike sites before you enter details
Scammers continue using brand trust to bypass your defenses.
Scammers ramped up brand impersonation attacks throughout Q4 2025, timing their campaigns around when people are busiest online, shopping for deals, renewing subscriptions, or looking for jobs. They targeted Microsoft, Facebook, Roblox, and McAfee by launching fake storefronts during Black Friday, sending delivery scams throughout December's package delivery rush, and running job scams as January job hunting picks up.
Attackers weaponize brand recognition, betting that a Microsoft billing alert or Facebook security notification will bypass skepticism when it arrives during year-end account reviews, holiday coordination chaos, or gift card purchase rushes. The sophistication lies not just in visual deception but in strategic timing; scams now arrive at the exact moments when consumers interact most frequently with the brands being impersonated, turning routine digital tasks into vulnerability windows.
With email services, gaming platforms, and social media becoming prime targets, the brands we depend on daily become the masks attackers wear to deceive us.
Top 10 Most Imitated Brands in Q4 2025
Microsoft took the top spot, pushing Facebook out of its Q3 lead as scammers shifted focus to account credentials and year-end subscription renewals. This shift shows how scammers are getting smarter: they pay attention to when people use specific services most, then target those exact brands during peak activity periods.
Q4 2025 Most Imitated Brands:
- Microsoft
- Roblox
- McAfee
- Steam
- AT&T
- Amazon
- Yahoo
- Coinbase
What makes all these brands attractive to scammers? Four things: they have millions of users, people trust them without thinking twice, they hold valuable login credentials and personal information, and people use them more heavily during Q4.
For example, gaming platforms like Steam see heavy traffic during year-end holiday sales. Phone and web service companies (AT&T, Google, Yahoo) get more attention in December when people check their accounts and renew subscriptions. Amazon gets targeted because of holiday shopping, while Coinbase gets hit when people review their crypto investments and prepare for tax season. The top four brands (Microsoft, Facebook, Roblox, McAfee) deserve closer attention because scammers use specific tactics for each one.
What You Need to Know About the Top 4 Brands
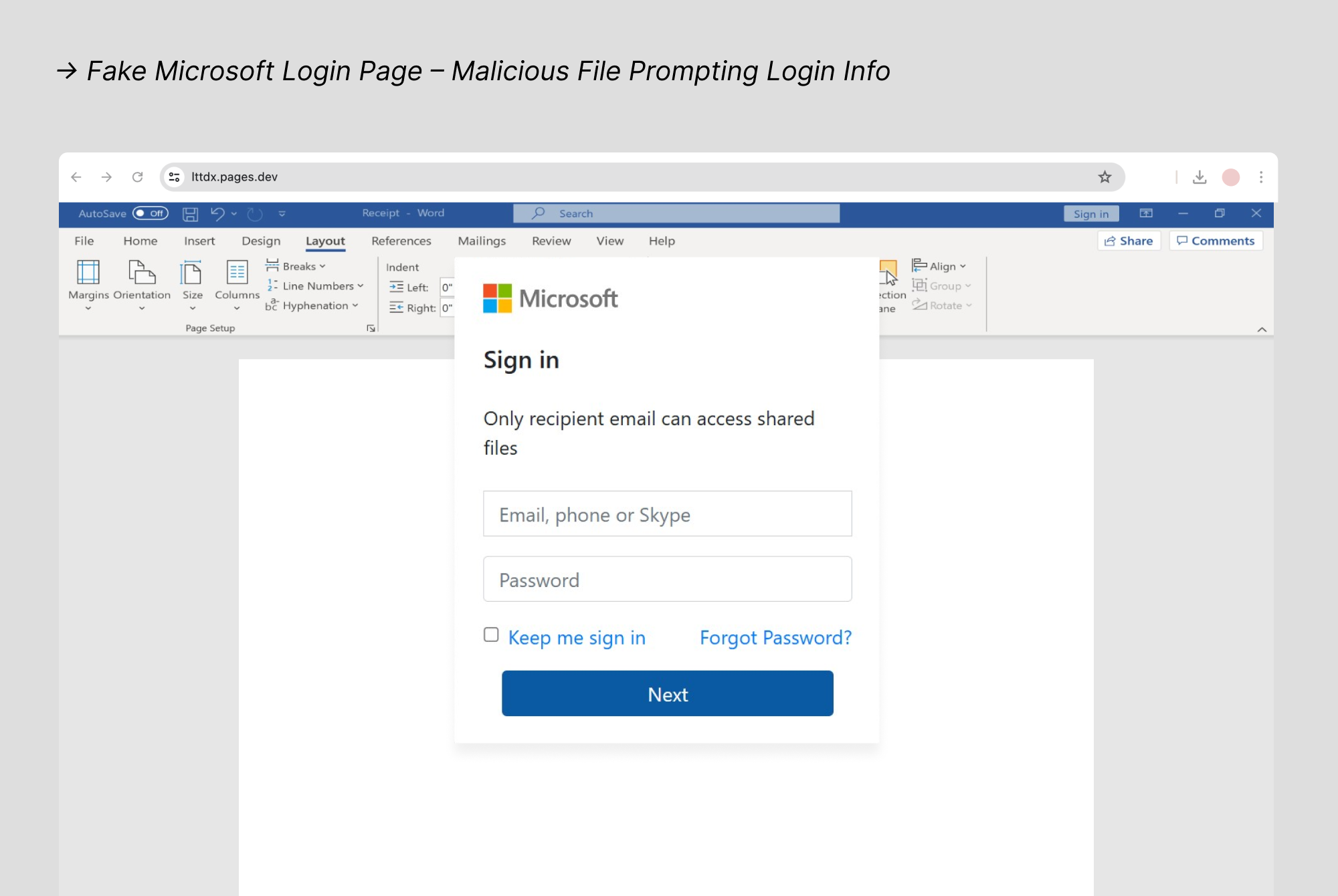
1. Microsoft
Scammers target Microsoft users with fake account security alerts, billing failure notifications, and subscription renewal warnings. These scams mimic legitimate Microsoft communications for Outlook, OneDrive, and Microsoft 365, making them difficult to distinguish from real notices. When users fall for these fake pages, attackers steal login credentials and payment card information.
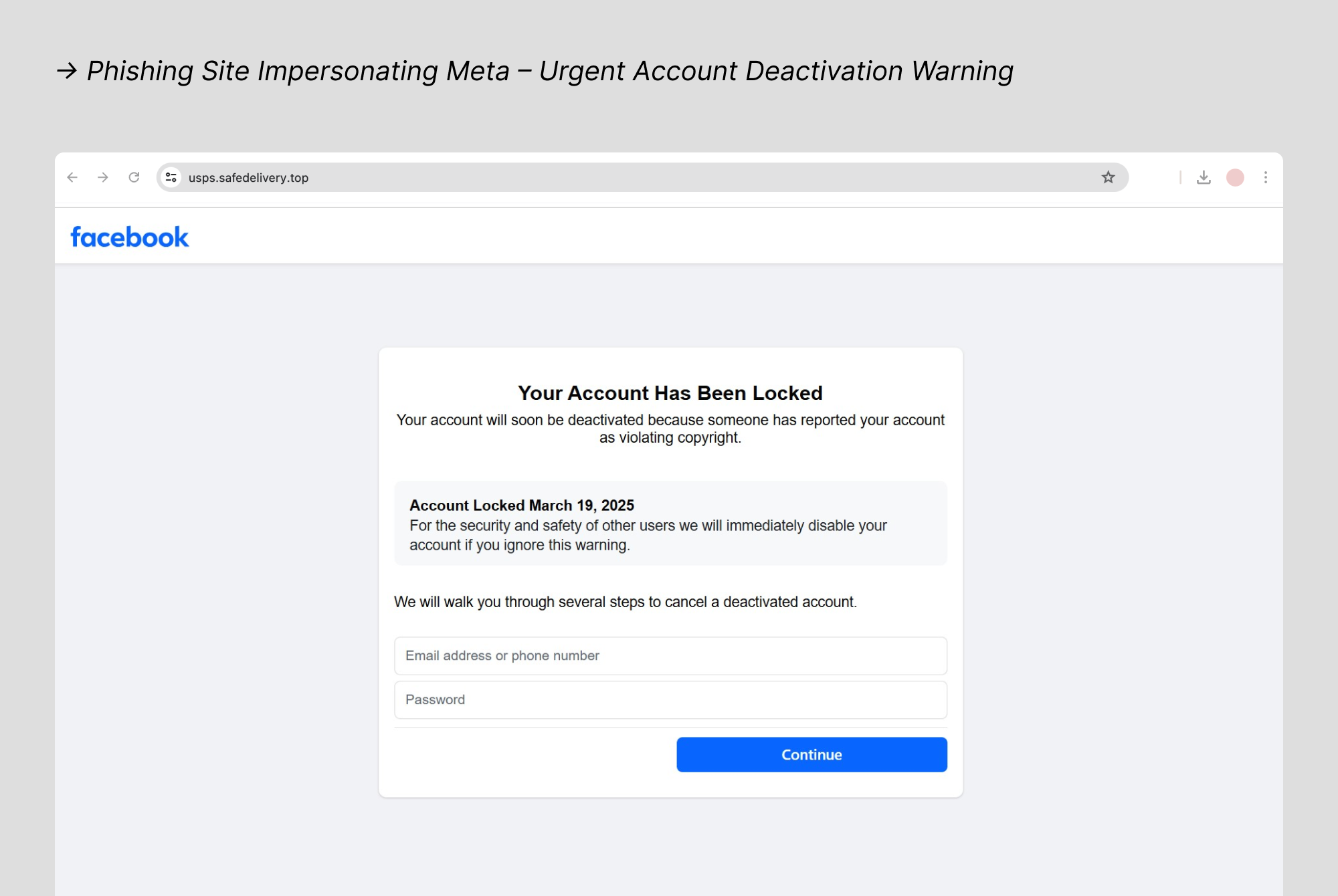
2. Facebook
Scammers send account lockout warnings claiming "suspicious login detected" or "policy violations" to create panic and pressure users into acting quickly. Fake recovery pages steal login credentials, phone numbers, and verification codes. Once compromised, attackers message your entire friend list with money requests, investment scams, and malicious links that exploit trusted relationships.
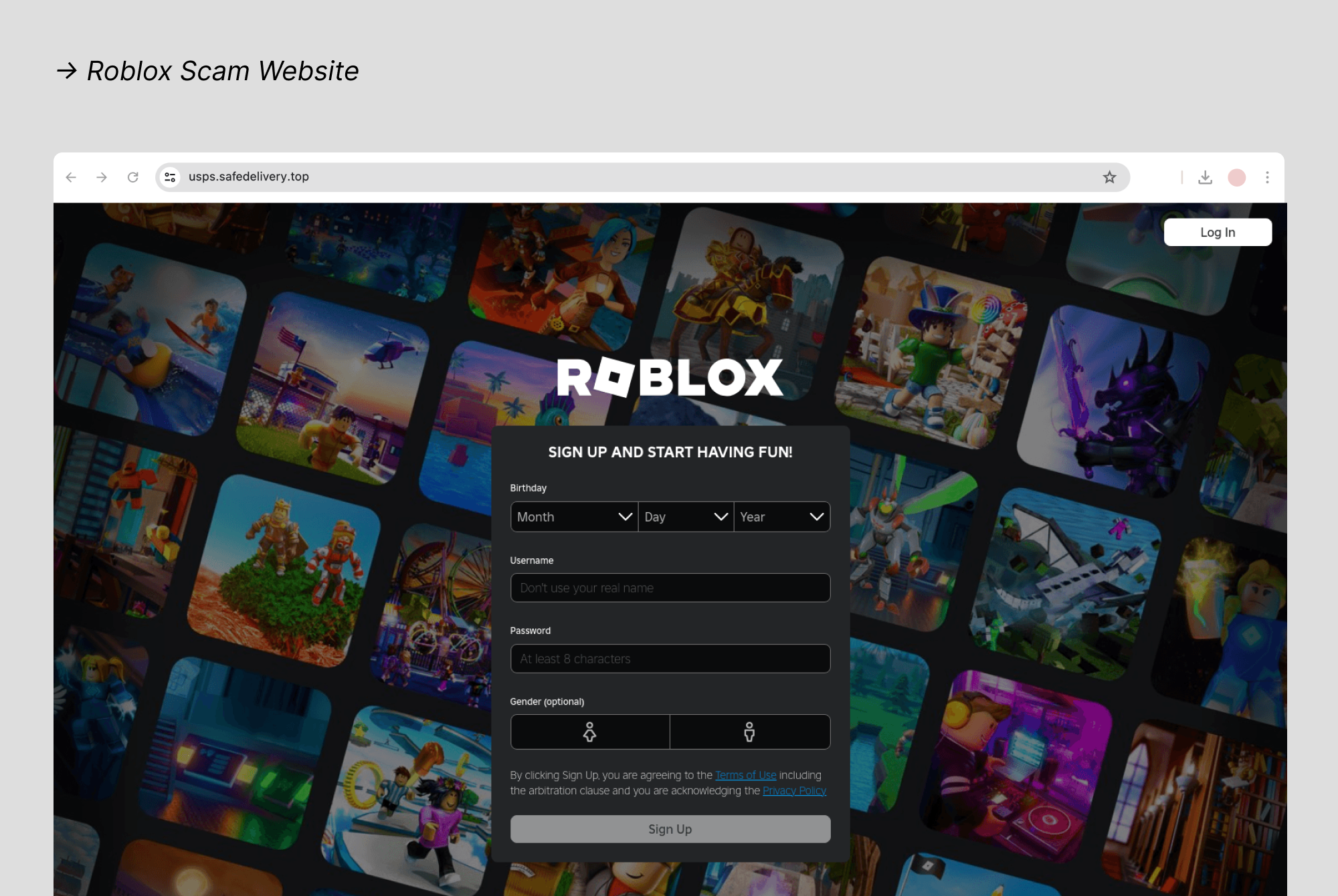
3. Roblox
Scammers target Roblox users with fake "double Robux" promotions, fraudulent redemption sites, and account suspension threats aimed at both children and parents. Kids encounter fake giveaways requiring "verification" that steal passwords, while parents find fake support sites that harvest payment information when trying to purchase or redeem gift cards. The platform's young user base makes these scams particularly effective.
4. McAfee
Scammers impersonate security software by sending fake warnings that "your McAfee subscription expires soon" or "your protection has lapsed" to create urgency. Fake renewal portals either install malware disguised as "security updates" or steal payment information through fraudulent checkout pages. These scams exploit the fact that users trust security software brands and want to maintain protection, making them more likely to click on malicious renewal links.
.png)
Holiday Shopping Scams Are on the Rise
Black Friday and Cyber Monday shopping scams surged to unprecedented levels in 2025, with Guardio research revealing a 30x increase in shopping-related scams and a 500% rise in fraudulent Black Friday campaign emails during November alone. AI has fundamentally changed the threat landscape: 76% of phishing websites now use AI-generated content, allowing scammers to create pixel-perfect clones of legitimate retailers at an industrial scale. These fake sites target major brands, including Amazon, Apple, Walmart, and Costco, exploiting holiday shopping urgency when consumers prioritize speed over verification. The solution: a proactive stance. This Guardio's video guide breaks down the six red flags that expose fake shopping sites and explains how to verify legitimacy before entering payment information.
Expect More Delivery Scams as Packages Arrive
Following the holiday shopping surge, delivery notification scams are expected to intensify throughout December and January as attackers target consumers monitoring multiple shipments. Scammers send text messages and emails impersonating USPS, FedEx, UPS, DHL, and Amazon, claiming delivery failures or address verification issues that require "immediate action." Fake delivery tracking websites and browser extensions now replicate legitimate carrier interfaces with functional tracking number lookups, creating convincing portals that steal login credentials, harvest payment information for fabricated shipping fees, or install malware through "required" package tracking apps. January represents peak vulnerability: when consumers have lost track of how many packages they ordered during holiday sales, fake delivery notifications blend seamlessly into legitimate tracking updates, exploiting the uncertainty of whether you're expecting two packages or five.
Job Scams Evolve Into Sophisticated Credential Theft Operations
Job scams have evolved beyond simple "work from home" spam into sophisticated credential harvesting operations that exploit professional networking platforms. Phishing emails impersonate major brands like Louis Vuitton, Amazon, and hospitality chains, directing recipients to convincing fake career portals that request "quick application via Facebook login."
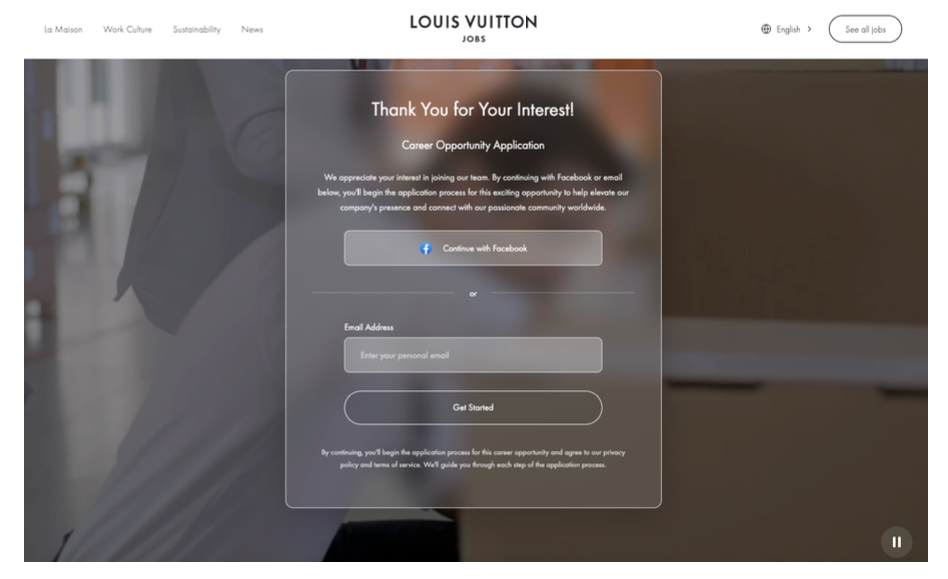
These sites mimic Facebook's official "Continue with Facebook" login page, tricking users into entering their username and password directly into the fake portal. Once compromised, attackers gain access to any accounts linked to Facebook, message friends with cryptocurrency and investment scams, and steal saved payment information from Facebook ad accounts. Scammers also post fake listings on LinkedIn, Indeed, and industry job boards using fake recruiter profiles, timing campaigns around high-unemployment periods to target job seekers most vulnerable to these offers. Guardio's video guide explains how to verify recruiter legitimacy and identify fake job sites before surrendering account access.
Staying Protected Through Every Season
Microsoft claimed the top spot in Q4 as attackers targeted its massive user base with credential theft and billing scams. Meanwhile, shopping scams surged during Black Friday, with delivery scams expected to follow as packages arrive throughout December and January. Job scams rounded out the quarter by exploiting end-of-year hiring activity. These attacks share a common strategy: scammers time attacks for maximum impact when people are distracted, rushed, or expecting notifications from brands they know and trust.
Staying safe requires consistent vigilance. Verify sender authenticity before clicking links, checking for domain misspellings or suspicious extensions. Navigate to official websites independently rather than using links in messages. Enable two-factor authentication on all accounts. Most importantly, pause before acting on urgent messages. Scammers count on people acting fast without thinking.
Manual vigilance works, but only if you catch every threat. Guardio blocks phishing sites, fake shopping portals, and credential theft attempts in real time, before they reach you. If your credentials appear in a data breach, Guardio alerts you immediately so you can secure your accounts. Threats don't stop between quarters, and neither should your protection.
{{component-cta-custom}}FAQs
How can I tell if a microsoft overtakes facebook as most imitated brand in q4 2025 phishing attacks message or page is real?
Start by verifying where the link goes and who sent it. If anything feels rushed or unusual, do not click. Open the official site or app directly and check your account there.
What should I do if I already clicked or entered details?
Close the page, then sign in from the official site to review recent activity. If you entered a password, change it and enable two-step verification. Watch for unusual messages, logins, or transactions.
What is the safest way to verify Microsoft Overtakes Facebook as Most Imitated Brand in Q4 2025 Phishing Attacks?
Use a trusted path: type the site address yourself, use a saved bookmark, or open the service app. Avoid verifying through message links, especially when the message creates urgency.
What is the fastest safe first step for Microsoft Overtakes Facebook as Most Imitated Brand in Q4 2025 Phishing Attacks?
Start by verifying the source using official channels (official website/app) rather than clicking message links. Then follow step-by-step checks.
What are common red flags to watch for?
Urgency, unusual links, and requests for sensitive details are common red flags. When in doubt, verify through a trusted path.
What should I do if I already clicked?
Close the page, change passwords for any account you entered, enable two-step verification, and review recent account activity.








