What is Pharming? Signs, Types & Protection Tips

Key Takeaways
- Start with the official account security and activity pages
- Use strong unique passwords and two-step verification
- Be cautious with links that ask you to sign in
- Monitor for unusual charges or login alerts
- Real-time link protection helps block lookalike pages that steal credentials
Pharming is a type of cyberattack that redirects users from legitimate websites to fraudulent ones without their knowledge. Pharming manipulates web traffic behind the scenes, making it more dangerous and harder to detect. This attack often targets the Domain Name System (DNS) or a device’s host files, rerouting users even when they enter the correct website address. The goal is to steal sensitive information such as login credentials, banking details, or personal data.
With technology evolving rapidly, cybercriminals are finding new ways to make these attacks harder to spot. They increasingly use generative AI to create smarter and more personalized scams, making it even more difficult for users to detect a threat. That’s why understanding pharming and knowing how to protect yourself has never been more important. In this guide, we’ll explain how pharming works, what signs to watch out for, and the steps you can take to stay safe online.
{{component-cta-default}}
What is Pharming?
Pharming is an online scam where you're secretly sent to a fake website even if you typed in the right web address. It happens when hackers mess with your internet settings or your device so that when you try to visit a trusted site (like your bank), you're sent to a fake version that looks exactly the same. The fake site is designed to steal your personal information, like passwords or credit card numbers.
What makes pharming scary is that you might not notice anything wrong. Everything can look normal, but your data may be silently transmitted to attackers.
Pharming vs. Phishing
Pharming and phishing sound similar, but they are different. This is how:
| Feature | Phishing | Pharming |
|---|---|---|
| Method | Tricks the user with fake emails or messages | Secretly redirects the user to a fake website |
| User Action Needed? | Yes, the user must click a link or open a message | No, redirection happens automatically |
| How It Works | Uses social engineering and fake communication | Changes system or network settings to reroute traffic |
| Visible to Users? | Often includes signs like suspicious links or poor grammar | Usually invisible - everything looks normal |
| Target | Individual users | Systems (like DNS or host files), sometimes whole networks |
| Example | A fake email from “your bank” asking you to log in | Typing in your bank’s URL but landing on a fake version |
Phishing tries to fool you directly, while pharming changes the route you’re visiting without you knowing.
What is Pharming Malware?
Pharming malware modifies device or network settings to reroute website access. It can enter your computer or router and quietly change the settings that control where websites take you.
Once this malware is on your device, it can quietly send you to fake websites without you even realizing it. You might think you’re logging into your email or bank, but you're actually giving your information to criminals. This kind of malware can come from fake downloads, shady browser extensions, or even apps that seem harmless. It often runs in the background, so you don’t even know it’s there until something goes wrong.
How Pharming Works
Pharming tricks users into visiting fake websites by tampering with how internet traffic is directed. Here’s how it typically happens:
- Attackers compromise DNS servers: These are like internet address books that translate website names into actual locations. By hacking a DNS server, attackers can reroute many users to fake websites even when they type in the correct web address.
- They manipulate the host file on your device: This file controls where your computer thinks certain websites live. If malware changes it, your device may send you to a malicious site instead of the real one.
- They use malware to redirect traffic: Some malicious programs sit on your device or browser and quietly change where you go online. These threats can silently redirect you, suppress browser security warnings, or present realistic fake login pages designed to capture your credentials.
All of these methods work behind the scenes, making pharming hard to notice until your data is already compromised.
Types of Pharming Attacks
Pharming attacks can happen in a few different ways, depending on what the attacker targets. Below are the three most common types:
DNS-Level Redirection
This type of attack targets the DNS infrastructure itself, which is often at the level of internet service providers (ISPs) or large public DNS services. When attackers gain access to a DNS server, they can poison its records, causing thousands (or even millions) of users to unknowingly visit fake websites.
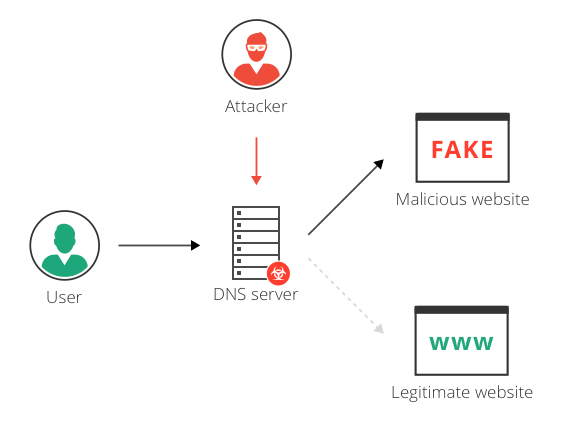
DNS-level pharming is especially dangerous because it operates without user involvement and can compromise entire networks simultaneously. It’s commonly used in state-sponsored cyber-espionage or large-scale credential harvesting.
In 2019, the U.S. Department of Homeland Security warned of widespread DNS hijacking campaigns affecting government and commercial domains across multiple countries, redirecting users to attacker-controlled sites without any malware on their devices.
Host File Tampering on End-User Devices
In this variant, the attacker targets individual devices, usually through malware that silently alters the host file. The host file overrides DNS lookups locally, so even if a DNS server is clean, the victim’s device points to the attacker’s site.
This is a low-scale but highly personalized attack, often used in targeted phishing campaigns against executives, activists, or specific company employees. It’s also favored in spyware deployments.
Script-Based or Malware-Enabled Attacks
These attacks involve browser-level manipulation. Malicious browser extensions, injected scripts, or trojans monitor user activity and redirect only specific types of traffic, such as logins to bank websites, crypto wallets, or government sites.
These attacks are more selective and data-driven. They often operate only under specific conditions (e.g., when a user visits certain URLs), making them harder to detect and replicate during investigation.
Warning Signs of Pharming
While pharming attacks are designed to be stealthy, a few subtle clues can give them away. Here are three key warning signs to watch for:
1. Lookalike or Suspicious Login Pages
If a login page looks slightly off, maybe the logo isn’t as sharp, the fonts look unusual, or the layout feels unfamiliar, then it could be a fake. Pharming sites often mimic real websites but miss small design details. If something feels "not quite right," it’s worth double-checking.
2. Unusual URLs or Spelling Errors in Links
Even when you type a web address correctly, pharming can silently redirect you. But a careful look at the URL might reveal small anomalies like extra characters, unusual subdomains (like login.yourbank.safe-check.com), or slight misspellings (like paypa1.com). These subtle changes are signs you're not on the real site.
3. Lack of HTTPS or Security Certificate Warnings
Legitimate websites use HTTPS (look for the padlock icon). If a login page shows a “Not Secure” warning, or if your browser alerts you about a certificate issue, it’s a red flag. Some pharming sites may skip proper encryption or use expired or mismatched certificates to save effort by leaving behind clear signals of danger.
{{component-tips}}
Real-World Pharming Examples
Pharming attacks don’t just exist in theory, but they’ve happened on a large scale, affecting everyday users and entire networks. Below are two notable examples that show how pharming works in real life.
ISP-Level Attacks Targeting Home Users
In a sophisticated operation known as “StormBamboo”, hackers intercepted and manipulated DNS queries at the ISP level, and even users relying on public DNS services like Google or Cloudflare were affected. This bypassing of trusted providers highlights how advanced DNS-level pharming campaigns can be.
This kind of attack is dangerous because it’s completely invisible to users. The web address appears correct, the site looks normal, and no warning is shown. Victims often don’t realize they’ve been tricked until unauthorized transactions start showing up.
Router Exploits Leading to Mass Redirects
Attackers in Brazil exploited vulnerabilities in consumer routers such as TP-Link and Asus using CSRF-themed exploit kits (GhostDNS, Novidade, SonarDNS). These silently changed router DNS settings, redirecting all network-connected devices to fake banking or e-commerce sites. Avast reported over 180,000 routers hijacked between Feb-May 2019.
Router-based attacks can scale quickly, affecting entire households or small offices. Even if your personal device is secure, a compromised router means all connected traffic is vulnerable, making this one of the most effective and overlooked attack vectors in home networks.
Consequences of Pharming
Pharming attacks often go undetected until real damage is done. Here are three serious consequences that can result from a successful pharming incident:
1. Financial Theft and Unauthorized Transactions
Once a user enters their login details into a spoofed site, especially banking or payment platforms, attackers can immediately gain access to accounts. This often leads to direct financial loss through unauthorized transfers, credit card fraud, or purchases made without the victim’s knowledge.
Unlike some scams that just attempt to collect data, pharming often leads to instant monetary loss, especially when tied to banking or cryptocurrency wallets.
2. Credential Harvesting and Identity Theft
Pharming sites mimic login pages of email services, cloud tools, or corporate portals to collect usernames, passwords, and sometimes even multi-factor authentication codes. This data can be sold on dark web marketplaces or used for identity theft and account takeovers across multiple services.
A single successful pharming attempt can compromise multiple parts of a victim’s digital life, especially if they reuse passwords or don't use two-factor authentication.
3. Long-Term Reputational Damage
Organizations targeted by pharming, especially those whose domains are spoofed, may face loss of customer trust, regulatory scrutiny, and damage to brand reputation. Users who fall victim may also suffer long-term consequences like frozen accounts, legal issues, or lowered credit scores.
Pharming doesn’t just cause one-time loss, but it can have lasting ripple effects on trust, privacy, and digital safety for both individuals and organizations.
How Pharming is Evolving with AI
With the rise of AI, pharming attacks are becoming smarter, more targeted, and nearly impossible to detect with the naked eye.
One thing we know for sure about 2025:
Guardio (@GuardioSecurity) January 7, 2025
Scammers will keep getting better at using AI tools.
As Karin, VP Product at Guardio, told @ABC11_WTVDABC11, AI is only making scammers' jobs easier, with scams becoming nearly impossible to spot with the human eye. pic.twitter.com/VzSfqGMvM8
Pharming tactics have evolved from simple redirects to AI-driven deception, making them faster, scalable, and dangerously convincing.
1. AI-Generated Fake Login Pages
Modern AI models can generate highly realistic fake websites that mirror legitimate login pages almost perfectly down to font spacing, button animations, and even loading sequences. These replicas are built at scale and tailored to specific brands, making them much harder to distinguish from the real sites.
Earlier pharming sites often had obvious design flaws or outdated layouts. Now, AI tools like generative web design engines can clone modern UIs in seconds, drastically increasing the success rate of these attacks.
2. Personalized Redirects Using Leaked Data
With access to leaked personal data from breaches or the dark web, AI algorithms can craft tailored redirection attacks. For example, users may be shown a fake page referencing their actual bank, location, or recent online activity, making the deception feel more believable.
Personalized targeting increases trust. A user is far more likely to enter their details when the fake page appears highly relevant to them. AI can automate this level of precision on a large scale.
3. Smarter Social Engineering Techniques
AI chatbots and language models can now generate phishing messages or browser alerts with human-like fluency. These are used alongside pharming redirects to convince users to “verify account activity,” “reset passwords,” or “approve urgent payments,” adding an extra layer of manipulation.
With AI handling the scriptwriting and tone adjustment, even savvy users can fall for these messages, especially when paired with a fake but convincing site generated seconds earlier.
How to Stay Protected From Pharming
Staying ahead of pharming doesn't require advanced tech skills; just using relevant tools and following practical habits can close the gaps that attackers will look to exploit.
| Protection Strategy | Why It Matters |
|---|---|
| Use Anti-Malware and Real-Time Protection Tools | Detects and blocks malicious redirects, host file tampering, and fake login attempts in real time. |
| Choose Secure DNS Providers and Encrypted Connections | Trusted DNS services (like Cloudflare or Google DNS) reduce the risk of DNS hijacking. DNS over HTTPS (DoH) encrypts queries. |
| Keep Devices and Software Patched | Security updates fix known vulnerabilities in operating systems, routers, and browsers exploited by pharming. |
| Always Check URLs and Security Certificates | Verifying the domain name and HTTPS padlock helps spot fake websites before entering sensitive information. |
| Enable Two-Factor Authentication (2FA) | Even if credentials are phished, 2FA provides an extra layer that stops attackers from logging in. |
These steps don’t just protect against pharming, but they help secure your digital life across devices, platforms, and networks.
What to Do After a Pharming Attack
If you’ve fallen victim to a pharming attack or even suspect you have, then quick action is critical. Here are the first things you should do to limit damage and start recovering:
1. Secure Your Network and Change Passwords
Immediately disconnect from the internet and check your router settings, especially DNS configurations, to ensure nothing has been tampered with. Then, using a trusted network, change the passwords to your affected accounts, starting with email, banking, and any accounts reusing the same credentials. Avoid using the same password across platforms, and always opt for a password manager going forward.
2. Run Full Device and Browser Security Scans
Use a trusted anti-malware tool to perform deep scans of your system.
Run a free security scan to check if your data was involved: https://t.co/4UXdN3nx8B
Guardio (@GuardioSecurity) August 22, 2024
Some pharming attacks involve malware that alters local files (like your device’s host file), installs malicious browser extensions, or captures data through background scripts. Clear all cache, disable unfamiliar plugins, and reset settings to default if needed.
3. Report the Incident to Relevant Platforms and Providers
If your login credentials were stolen, notify the platform (e.g., your bank, email provider, or workplace IT team) as soon as possible. Most major services offer support channels for compromised accounts. Also, consider reporting the phishing/pharming site to browser security tools
How Guardio Helps Prevent Pharming
Guardio is built to actively protect users from deceptive attacks like pharming by stopping threats before they can do harm. Here’s how it works across different threat layers:
1. Real-Time Website Blocking and Phishing Protection
Guardio automatically blocks access to fake or malicious websites, including those created through DNS hijacking or URL spoofing. This prevents users from landing on cloned login pages even if the redirect happens silently in the background.
2. Alerts for Suspicious Redirects or Deceptive Website Behavior
If a page you’re visiting behaves suspiciously, like auto-redirecting, loading third-party tracking scripts, or mimicking legitimate brands, Guardio flags it instantly. You’ll get a real-time warning, giving you the chance to exit before entering any sensitive data. It acts as a second layer of defense when DNS-level or device-level protections fail.
3. Protection Against Malicious Extensions and Scripts
Many pharming attempts are delivered through infected browser extensions or injected scripts. Guardio scans your browser environment for unsafe add-ons, automatically removing threats that can hijack your browsing sessions or alter DNS settings.
4. Identity Monitoring and Threat Detection
If your credentials are exposed due to a pharming attack, Guardio’s identity monitoring alerts you when your email or personal information appears in data breaches or suspicious activity is detected. This helps you act quickly to secure compromised accounts and prevent further misuse.
Conclusion
Pharming is a silent but serious cyber threat that’s growing more advanced, especially as attackers adopt AI tools to improve their tactics. Unlike traditional phishing, pharming doesn’t always rely on user interaction. It can quietly redirect even cautious users to fake sites, compromising their data and financial security without any obvious warning.
That’s why awareness, layered protection, and modern security tools like Guardio are more important than ever. From using secure DNS providers to recognizing subtle signs of deception, staying informed is your first line of defense.
Cyber threats may evolve, but so can your ability to stay ahead. A few smart choices can make the difference between being a target and being prepared.
{{component-cta-default}}
{{component-cta-custom}}FAQs
Can pharming happen on public Wi-Fi?
It can. Public networks can increase exposure to certain attacks, especially if you are not using secure DNS settings. Using HTTPS and keeping devices updated helps, but additional protection can reduce risk further.
How can I tell I am on a fake version of a real site?
Look for subtle URL differences, missing HTTPS indicators, and login pages that feel slightly off. If in doubt, close the page and type the site address yourself or use a saved bookmark.
Does changing DNS settings help prevent pharming?
Using a reputable DNS provider can help, but it is not a complete solution. Keeping your router updated, using HTTPS, and avoiding risky links are still important.








