Apple ID Scams: How to Identify, Avoid Them & Stay Protected

Key Takeaways
- Urgency and pressure are common scam tactics
- Verify the sender and URL by using official channels
- Never share passwords or one-time codes through messages
- If you clicked, change passwords and review account activity
- Real-time warnings can help stop lookalike sites before you enter details
Keeping your Apple ID secure is critical as it grants access to your iPhone, iCloud photos, apps, and even payment information. Because of this, it’s a frequent target for cybercriminals who continuously develop sophisticated tactics to exploit unsuspecting users.
These scammers often pose as Apple support, sending convincing fake emails, text messages, or even making phone calls. Their goal is to trick you into revealing sensitive details like passwords or credit card information. If successful, the consequences can be severe: unauthorized purchases, data breaches, or complete loss of access to your Apple account and devices.
This guide walks you through the common scams, how to recognize them, and the best steps to protect your Apple ID and personal data. Staying secure means staying informed; knowing what to look for and using Apple’s built-in protections, like two-factor authentication.
{{component-cta-custom}}
What Are Apple ID Scams?
Apple ID scams are deceptive schemes designed to trick users into revealing their login credentials, personal data, or financial information. These attacks often impersonate official Apple communications to gain unauthorized access to user accounts and the services linked to them. These scams are designed to gain unauthorized access to an individual's Apple account and the vast amount of data and services linked to it, including iCloud, App Store purchases, payment methods, and device access.
Scammers employ various sophisticated tactics to achieve their goal, often by impersonating Apple, a trusted app, or a service. Their primary objective is to steal your Apple ID username and password, which can then be used for fraudulent activities such as making unauthorized purchases, locking users out of their own devices, accessing private photos and documents, or even stealing identity information.
These scams leverage social engineering techniques, playing on users’ trust, fear, or urgency to manipulate them into taking actions that compromise their security.
Types of Apple ID Scams
Apple ID scams come in various forms, each designed to trick users into compromising their account security:
1. Phishing Emails and Messages
These scams use fake emails or texts that look just like they're from Apple. They often warn about a problem with your account and ask you to click a link. This link takes you to a fake website where they try to steal your Apple ID and password.
Can you tell which URL leads to the real Apple site?
Guardio (@GuardioSecurity) March 20, 2024
Take a closer look at this tweet. At first glance, both URLs appear identical, but one uses a capital “I” to mimic a lowercase “L,” a subtle trick often used in phishing attempts to fool users.
2. Fake Apple Support Calls
You may receive a call from someone posing as an Apple Support representative, claiming there’s a serious issue with your account or device. Their objective is to trick you into revealing your Apple ID credentials, installing malicious software, or paying for fraudulent support services.
3. Suspicious Pop-Ups and Alerts
These are messages that pop up while you're online, pretending to be from Apple. They say your device is infected or your Apple ID needs fixing. These pop-ups try to lure you into clicking a link, downloading malicious software, or calling a fake support number - all actions that can compromise your security.
4. Account Recovery Scams
If you're trying to get back into your Apple ID, scammers might pretend to be Apple's recovery team. They'll ask for personal info or codes to take over your account themselves.
5. Fake Subscription Renewal Notices
You get emails or texts saying an Apple subscription (like for Music or iCloud) is renewing, often for a significant sum of money. They'll include a link to cancel or manage it, but it could be a trick to steal your Apple ID or card details.
6. Fake Payment Requests
You might see fake bills for things you didn't buy from the App Store. These messages push you to click a link to 'cancel' or 'report' the purchase. This link goes to a fake site aiming to steal your Apple ID or payment info.
7. Fake Account Verification Requests
These messages tell you to 'verify' or 'update' your Apple ID right away, saying it will be locked if you don't. The link in these messages goes to a fake login page where your details are stolen.
How to Detect Apple ID Scams
Knowing the common tricks scammers use is the first step. Here's how to spot an Apple ID scam and keep your account safe:
| Detection Method | What to Look For / How to Detect |
|---|---|
| Check Email Sender and URLs | Unfamiliar or slightly off email addresses (e.g., not apple.com); hover over links to see the actual website address - it should be an official Apple domain. |
| Look for Urgency or Threatening Language | Phrases demanding immediate action or threatening account suspension/closure if you don't respond right away. |
| Avoid Clicking Suspicious Links | Never click links in unexpected or questionable messages. Instead, go directly to Apple's official website by typing the address yourself. |
| Verify Suspicious Requests with Apple | If you're unsure, contact Apple Support directly through their official website or phone number to confirm any requests. |
| Check for Poor Grammar and Spelling Errors | Obvious typos, grammatical mistakes, or awkward sentences in messages - official communications are usually error-free. |
| Look out for Alerts about Password or Account Changes | Unexpected notifications about changes to your Apple ID, password, or security settings that you didn't make. |
| Monitor for Unfamiliar Devices or App Downloads | Check your Apple ID settings (appleid.apple.com) for any devices or apps connected to your account that you don't recognize. |
| Be Cautious if Your Apple ID is Locked or Suspended | Scammers often send fake alerts about locked accounts; always verify by trying to sign in directly at appleid.apple.com. |
| Investigate Alerts about Sign-ins from Unknown Locations | Notifications that your Apple ID has been used to sign in from a location you weren't in. |
Real Examples of Apple ID Scams
Understanding the common traits of scam attempts can help you recognize them. Scammers go to great lengths to mimic legitimate Apple communications.
Phishing Emails and SMS
This text message falsely claims that the recipient’s Apple ID will expire that day and urges them to tap a shortened link to avoid data loss.
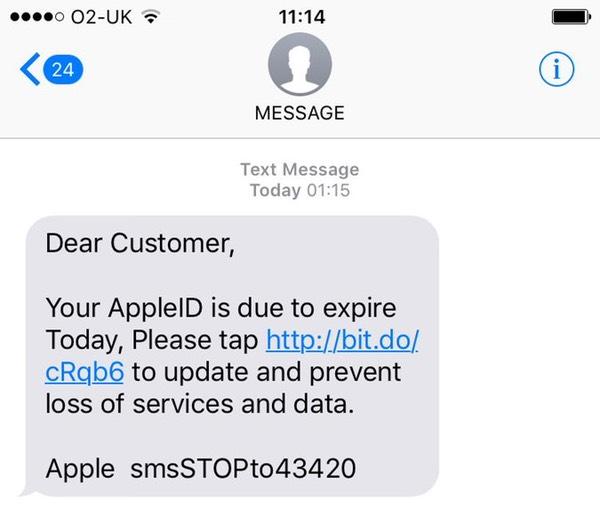
Why it's a scam:
- Apple never sends expiration notices via SMS.
- The URL uses a URL shortener (bit.do) to obscure its true destination.
- Language plays on urgency and potential data loss to provoke action.
Sample Spoofed Apple Login Pages
This is a prime example of a spoofed Apple login page designed to steal Apple ID credentials by mimicking a legitimate Apple Pay interface.
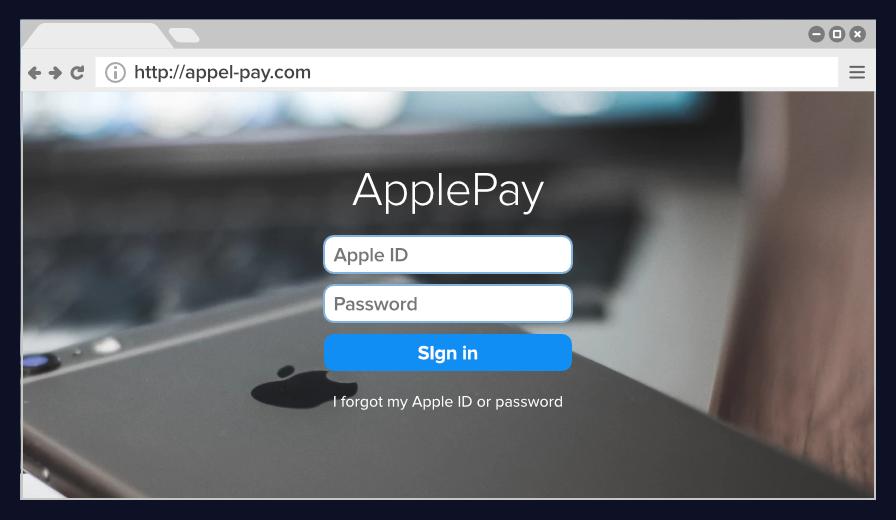
Key Indicators of a Scam:
- Suspicious URL: The web address http://appel-pay.com is a misspelled variation of Apple’s official domain. It uses “appel” instead of “apple,” a common phishing tactic known as typosquatting.
- No HTTPS Encryption: The page uses http:// rather than the secure https://. A real Apple login page would always be encrypted and display a valid certificate.
- Brand Misuse: The page attempts to blend Apple’s branding (font, color, background) with unofficial elements like a low-resolution background image and incorrect formatting.
- Credential Harvesting Form: The page asks users to input their Apple ID and password directly, which are then captured by scammers.
Voice Call Transcripts from Fake Support Scams
In more aggressive scams, users receive unsolicited calls from individuals claiming to be Apple Support agents. These scammers may spoof Apple’s official support number and use scare tactics to gain remote access to the user’s device or Apple ID.
Transcript Excerpt:
- Caller: “This is Jason from Apple Security. We’ve detected a breach on your iCloud account. We need to verify your identity and run a security scan. Are you near your device right now?”
- User: “Yes.”
- Caller: “Please go to your settings and enable remote support so I can remove the malware before it spreads.”
Red Flags:
- Apple never asks users to install remote access tools.
- Genuine Apple representatives never initiate unsolicited calls asking for credentials or verification codes.
Steps to Take After an Apple ID Scam
If you suspect you’ve fallen victim to an Apple ID scam, whether through a phishing email, spoofed website, or fraudulent phone call, then immediate action is crucial. Swift steps can help contain the damage, secure your data, and prevent further misuse.
1. Change Your Apple ID Password Immediately
Your first step should be to reset your Apple ID password. This cuts off the scammer’s access to your account and prevents unauthorized activity.
- Visit https://account.apple.com directly.
- Choose “Forgot Apple ID or password?” if you’re locked out.
- Create a strong, unique password you haven't used elsewhere.
2. Remove Unauthorized Devices from Your Account
Once logged in, check which devices are signed into your Apple ID. If you see any unfamiliar devices:
- Go to Settings > [Your Name] > Devices on an iPhone or iPad, or log in at account.apple.com.
- Select the suspicious device and choose Remove from account.
- This immediately revokes access from that device.
3. Enable Two-Factor Authentication (2FA)
If you haven't already, enable 2FA for your Apple ID. This adds a critical layer of security by requiring a verification code sent to a trusted device each time your Apple ID is used on a new device.
- Go to Settings > [Your Name] > Password & Security > Turn On Two-Factor Authentication.
4. Report the Scam to Apple and Relevant Authorities
Apple encourages reporting fraudulent messages and phishing attempts:
- Forward scam emails to: reportphishing@apple.com
- Report suspicious messages received via iMessage to: imessage.spam@apple.com
- Visit Apple’s official support page for more help.
5. Contact Your Bank Immediately
If you've entered payment information or suspect financial details have been compromised:
- Call your bank or credit card provider and report the incident.
- Monitor your account for unauthorized charges.
- Consider placing a fraud alert or freezing your credit, if necessary.
6. Report to Consumer Protection Agencies
To contribute to scam prevention efforts and assist with broader investigations:
- In the U.S., file a report with the Federal Trade Commission (FTC) via ReportFraud.ftc.gov.
- In other regions, contact national cybercrime units or consumer protection organizations such as Action Fraud UK.
{{component-tips}}
How to Prevent Apple ID Scams and Keep Your Apple Account Secure
Preventing Apple ID scams begins with proactive digital hygiene and awareness. By taking a few key precautions, you can dramatically reduce your risk of falling victim to fraudulent attacks and keep your Apple ecosystem secure.
1. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a one-time verification code sent to a trusted device whenever your Apple ID is accessed on a new device or browser.
- Go to Settings > [Your Name] > Password & Security
- Select Turn On Two-Factor Authentication
This makes it nearly impossible for hackers to access your account without physical access to your trusted devices.
2. Use Unique, Strong Passwords
Create a password that is long, complex, and not reused across other accounts. A secure Apple ID password should ideally:
- Be at least 12 characters.
- Combine letters (upper and lowercase), numbers, and symbols.
- Avoid predictable patterns like birthdates or simple words.
Use a reputable password manager to generate and store secure credentials.
3. Keep Apple ID Settings Updated
Make sure your contact information, recovery email, and trusted phone numbers are always current.
- Visit account.apple.com and log in.
- Review and update Account and Security settings.
- Ensure recovery options are correct in case of a lockout.
4. Update Devices and Software Regularly
Apple releases frequent security patches to fix known vulnerabilities. Outdated software is a common entry point for cybercriminals.
- Enable automatic updates in Settings > General > Software Update
- Keep all apps and the operating system up to date across your Apple devices
5. Avoid Sharing Apple ID Details Online
Never share your Apple ID credentials through email, text, or on any website other than Apple’s official domains.
- Be especially wary of unsolicited messages or pop-ups asking for login details
- Apple will never request your password, verification codes, or 2FA codes via email or phone
6. Periodically Audit Your Passwords
If you’ve reused your Apple ID password elsewhere or if it’s been exposed in a breach, then change it immediately.
- Use Apple’s built-in Security Recommendations in Settings > Passwords
- Alternatively, use services like Have I Been Pwned to check for compromised credentials.
7. Review Apple Device Login History
Check which devices are signed into your Apple ID to spot unauthorized access early.
- Go to Settings > [Your Name] on iOS, or visit appleid.apple.com.
- Review all listed devices.
- Remove any devices you don't recognize or no longer use.
Tools and Features to Help Detect Apple ID Scams
Modern cybersecurity threats, including Apple ID scams, often rely on deception and speed to succeed. A growing number of tools and built-in features are designed to detect these threats before they reach you or alert you the moment something looks suspicious. Leveraging these technologies can significantly enhance your defenses.
Real-Time Phishing Protection
Most modern browsers, including Safari, Chrome, and Firefox, now come with real-time phishing protection built-in. These systems automatically scan websites as you visit them and compare the domain against known phishing databases. If a site is flagged as deceptive or known to impersonate services like Apple, you’ll receive an immediate warning advising you not to proceed.
Apple’s own Mail app also performs automatic link scanning to flag suspicious URLs embedded in emails, which can stop you from clicking into fake Apple login pages or credential-stealing forms.
Catch Suspicious Links Before You Click
Apple ID phishing attacks often begin with a single malicious link, hidden in emails, text messages, or suspicious websites. These links can lead to fake login pages, inject harmful scripts, or silently redirect users through a chain of deceptive domains.
Guardio’s online protection includes real-time link scanning as part of its multi-layered defense system. Whether the link appears in your inbox, on social media, or on a site you visit, Guardio inspects it for signs of malicious intent, including dangerous scripts, spoofed domains, and suspicious redirect patterns commonly used in Apple ID scams.
But the threat goes far beyond iCloud or device access. A compromised Apple ID can open the door to a wide range of connected services, such as financial apps, subscriptions, email accounts, and communication tools.
Guardio helps you see the bigger picture. Beyond blocking malicious links, it gives you visibility into which connected accounts could be at risk if your Apple credentials are exposed, helping users take proactive steps to secure their entire digital footprint.
Browser-Based Warning Alerts
Browsers and mobile operating systems often display warning messages when a site lacks proper encryption or poses a potential risk. For instance, if a spoofed Apple ID login page is hosted without HTTPS encryption, you’ll likely see a “Not Secure” warning in the address bar. These alerts are critical cues that the page is untrustworthy and should be avoided.
Additionally, modern browsers flag deceptive sites using heuristics, like mismatched domains, login fields on insecure pages, or certificate errors, further reducing the chance of a successful phishing attempt.
Identity Monitoring For Apple-Related Data Leaks
Some premium security services now offer identity monitoring, which scans dark web marketplaces and data breach repositories for mentions of your Apple ID email address or associated personal information. If your credentials have been exposed in a known breach, you’ll receive an alert giving you the opportunity to reset your Apple ID password before it can be exploited.
Identity monitoring tools are especially valuable for early warning in cases where scammers buy leaked email-password combos and use them to launch automated login attempts on Apple’s servers.
How Guardio Protects You from Apple ID Scams
Guardio goes beyond basic threat detection because it offers proactive, real-time protection while guiding you through recovery and long-term security. Its strength lies not just in blocking Apple ID scams, but in helping you understand what to fix, why it matters, and what to do next if your data is compromised.
Detects Phishing Websites and Suspicious Links
Guardio continuously monitors the websites you visit and the links you interact with. If it detects a spoofed Apple login page, such as a fake iCloud or Apple Pay portal, it instantly blocks access and flags it as a phishing threat. This prevents you from entering sensitive credentials into malicious forms. If you did interact with a phishing site, it helps you identify whether the compromised Apple ID is reused across other services like Gmail or banking apps, and recommends securing those accounts too.
Warns You About Scam Emails and Texts
Phishing often starts in your inbox or messaging app. Guardio detects scam indicators in emails and texts, such as spoofed Apple support messages or fake password alerts, by analyzing link behavior and threat patterns, without needing to access private content. When identified, these messages are flagged with detailed warnings so you know exactly why they’re dangerous. Crucially, Guardio then offers actionable alerts and recommendations for post-threat recovery, including:
- Spotting other accounts that may have been accessed using your Apple ID
- Reviewing devices that may be at risk
- Updating or unlinking connected services to prevent further damage
Blocks Fake Sites in Real-Time
Scammers are constantly launching fake Apple-related sites to trick users. Guardio intercepts these threats the moment they appear. It uses advanced detection techniques to block sites that impersonate Apple’s branding or domain structure, even before they’re widely reported.
Alerts You to Data Leaks Linked to Your Apple ID Email
If your Apple ID email is ever found in a data breach, whether through an unrelated service or a direct Apple-related leak, Guardio sends an immediate alert. You’ll be told what data was exposed and when, so you can take informed action right away.
Conclusion
Apple ID scams are evolving, targeting users through phishing, fake support calls, and spoofed login pages. Use strong passwords, enable two-factor authentication, and stay updated. Tools like Guardio add a critical layer of protection by blocking threats in real time, alerting you to data leaks, and guiding you through recovery. It helps identify weak spots and secure connected accounts, ensuring you're not just alerted but prepared.
Apple ID controls access to personal data and devices, so proactive protection is essential. Don’t wait for a breach and secure your Apple ID today.
{{component-cta-custom}}
FAQs
Does Apple ever ask for your Apple ID password?
Apple will not ask for your password by email, text, or unsolicited calls. If a message asks you to confirm credentials, treat it as suspicious and sign in through appleid.apple.com or your device settings instead.
What should I do if I entered my Apple ID on a fake site?
Change your Apple ID password immediately, review your trusted devices, and enable two-factor authentication if it is not already on. Also check for unfamiliar sign-ins and update any accounts that reuse the same password.
How can I verify an Apple security alert?
Do not click the alert. Open Settings on your iPhone or iPad and review your Apple ID and security notifications there. For email, open the official Apple site in a new tab and check account status directly.








