How to Spot DocuSign Scams? Strategies & Examples

Key Takeaways
- Start with the safest fix: official settings and known-good steps
- Remove or disable suspicious extensions and downloads
- Avoid logging in from links; go to the official site directly
- If you entered details, change your password and enable two-step verification
- Real-time link protection helps reduce exposure to lookalike sites
Start by looking for the red flags: unexpected emails asking you to sign documents, vague sender names, suspicious links, or attachments that don’t quite match the context. These are all signs of phishing attempts impersonating DocuSign, which is one of the most trusted names in electronic signatures.
Cybercriminals exploit this trust by creating emails that closely mimic real DocuSign communications. Their goal is to steal your login credentials, install malware, or trick you into authorizing fraudulent transactions.
In this guide, we’ll show you exactly how to recognize these scams, walk through real-world examples, and outline specific steps to help you protect yourself. Whether you use DocuSign for business or personal matters, spotting the signs early can save you from serious data loss or financial harm.
{{component-cta-custom}}
What Are DocuSign Scams?
DocuSign scams are fraudulent attempts where cybercriminals impersonate the legitimate DocuSign platform to deceive users. These scams typically involve phishing emails that appear to be official DocuSign communications, urging recipients to open documents, click on links, or provide personal information.
The primary goal of these scams is to steal sensitive data such as login credentials and financial information, or install malware on the victim’s device. Attackers often create convincing fake emails or websites that mimic DocuSign’s branding, making it challenging for users to distinguish between genuine and fraudulent messages.
Because DocuSign is widely used for signing contracts, agreements, and other important documents, scammers exploit this trust to increase the likelihood that recipients will interact with their malicious content. Understanding what these scams look like is critical for avoiding potential harm.
How to Spot a DocuSign Scam
Scam emails can closely resemble official DocuSign messages, making them difficult to identify at first glance. However, there are a few consistent signs that can help you recognize suspicious communication. The table below outlines some key characteristics to be aware of:
| Indicator | What to Observe | Why It Matters |
|---|---|---|
| Unfamiliar Senders or Unexpected Requests | Messages from unknown contacts or those asking you to sign a document you weren’t expecting | Genuine DocuSign emails typically come from known senders and follow a specific context |
| Suspicious or Misleading Links | Hyperlinks that lead to unrelated or misspelled domains when hovered over | These often point to phishing sites created to steal login credentials |
| Generic Greetings and Language Errors | Use of terms like “Dear Customer,” along with spelling or grammatical mistakes | Legitimate messages generally address you by name and maintain professional language quality |
| Fake Email Domains and Impersonated Logos | Sender addresses from misleading domains and logos that appear distorted or outdated | Scammers attempt to mimic branding, but inconsistencies can reveal the message’s true origin |
| Unexpected Attachments or QR Codes | Includes PDFs, ZIP files, or QR codes without explanation or context | DocuSign does not require users to download files or scan codes to access documents |
Fake DocuSign Scam Email Examples
DocuSign scam emails often appear legitimate at first glance, using official-looking logos, familiar layouts, and urgent language. However, upon closer inspection, subtle inconsistencies reveal their true intent. Below are three realistic examples that demonstrate how these scams typically appear.
Example 1: Generic Phishing Attempt
Subject: Please Sign the Attached Document Immediately
From: DocuSign Services [docusign-secure@noticesignmail.com]
Body:
Hello,
A document has been sent to you for electronic signature. Please review and sign as soon as possible.
Document Title: Invoice_45678.pdf
Note: This document will expire in 24 hours.
Thank you for using DocuSign.
Do not reply to this email.
Red Flags:
- The sender address is not an official DocuSign domain
- Urgent call to action with expiration pressure
- Vague language and no personalization
Example 2: Malware Attachment
Subject: Payroll Update - Immediate Action Required
From: DocuSign HR Department [docusign@secure-update.net]
Body:
Dear Employee,
Please find the updated payroll report attached. This needs to be reviewed and signed before the end of day.
Attachment: Payroll_Update_August.zip
Thank you,
HR Team
Red Flags:
- Includes a .zip attachment (DocuSign never sends attachments via email)
- Uses urgency and authority tone to prompt immediate action
- No specific name or department details
Example 3: Credential Harvesting
Subject: Your DocuSign Account Has Been Suspended
From: DocuSign Security Team [account-alert@docusign-login.com]
Body:
Dear Customer,
We noticed unusual activity on your DocuSign account. To avoid service interruption, please verify your identity.
[Verify Account Now]
Failure to act within 12 hours will result in permanent suspension.
Sincerely,
DocuSign Account Security Team
Red Flags:
- Fake security alert with fear-based language
- Link to a fake login page designed to steal credentials
- Generic greeting (“Dear Customer”) and no account-specific details
Common Tricks Scammers Use in DocuSign Phishing
Scammers rely on psychological manipulation to increase the chances of a successful attack. These tactics are often subtle, making the phishing email seem trustworthy or time-sensitive. Below are some of the most common strategies used in DocuSign-related phishing scams:
Impersonation of Reputable Companies
Many scam emails falsely claim to represent well-known businesses like banks, telecom providers, HR departments, or even legal firms. These names are used to create a sense of legitimacy and trust, increasing the likelihood that the recipient will interact with the message.
Example:
“Your bank requires a signature on the new account terms via DocuSign.”
Urgent or Threatening Language
Scammers often apply pressure by including phrases like “urgent,” “immediate action required,” or “your account will be suspended.” This sense of urgency is designed to push recipients to act without verifying the email’s authenticity.
Example:
“Your access to DocuSign will be revoked within 12 hours unless you verify your credentials.”
Too-Good-To-Be-True Offers
Some phishing messages promise rewards, bonuses, or other benefits that require a signature to claim. These tactics are especially common in fake job offers or prize claims.
Example:
“Sign the attached form to receive your $500 DocuSign reward.”
Fake Invoices, Job Offers, or Tech Support Claims
Fraudulent emails may include phony invoices, employment documents, or IT support forms. These messages often urge the user to review or sign a document to resolve an issue or complete a transaction.
Example:
“Please sign the attached invoice to process your payment. Delays may incur penalties.”
How to Protect Yourself from DocuSign Scams
Avoiding DocuSign scams starts with awareness and a few basic security habits. While scammers continue to evolve their tactics, users can significantly reduce risk by following proven safety practices. Here are some essential precautions:
Never Click on Suspicious Links or Open Random Attachments
If you receive an unexpected email asking you to review or sign a document, avoid clicking any links or opening attachments unless you're absolutely sure it's legitimate. DocuSign never sends executable files or ZIP archives via email.
Always Verify Through DocuSign’s Official Website
Instead of clicking links within an email, go directly to www.docusign.com and log in from there. If a real document is waiting for your signature, it will appear in your secure account.
Use a Browser Extension or Security Tool
In a world where it’s getting harder to tell what’s real and what’s fake, scams are thriving - and the damage is real. That’s why raising awareness and using the right tools to stay protected is more important than ever.
Guardio (@GuardioSecurity) May 28, 2025
Trusted browser security tools like Guardio can automatically block phishing pages, scan URLs in real-time, and detect impersonation attempts before you click. This extra layer of protection can stop threats that might otherwise go unnoticed.
Watch for Red Flags Like Urgency or Requests for Login Info
Legitimate DocuSign emails will never pressure you with extreme urgency or ask for login credentials via email. Phrases like “your account will be suspended” or “sign in to unlock funds” are red flags and should be treated with caution.
{{component-tips}}
What DocuSign Will Never Ask You To Do
Understanding what legitimate DocuSign communications will never request helps you quickly identify potential scams and avoid falling victim to phishing attempts.
- Open PDF Attachments to Access Documents: Legitimate DocuSign emails do not require you to download or open PDF attachments directly from the email. All documents are accessed securely through their platform.
- Enter Login Credentials to View a Document: DocuSign will never ask you to provide your username or password via email or links outside their official site.
- Scan QR Codes as a Requirement: QR codes are not used by DocuSign as a mandatory step for document access or signing. Be cautious if you receive such requests.
- Register an Account to Sign a Document: You do not need to create or register a DocuSign account to view or sign a document sent to you.
What to Do If You Receive a Suspicious DocuSign Email
If you receive an email that appears to be from DocuSign but raises doubts, taking prompt and appropriate action is essential to protect your information and help stop scammers.
- Report the Scam to DocuSign: Check DocuSign’s official incident reporting guide or use the in-app “Report Abuse” feature to notify them about any suspicious emails or activity.
- Forward Suspicious Emails to spam@docusign.com: This helps DocuSign investigate and block future phishing attempts.
Hey Nick, thanks for bringing this to our attention. All valid and legitimate DocuSign envelopes will come from “@docusign.net” and start with “https." Please share with us at spam@docusign.com so that we can investigate!
Docusign (@Docusign) July 18, 2023
- Report to the FTC and Your Email Provider: Filing reports with the Federal Trade Commission (FTC) and your email provider helps track and reduce phishing scams.
- Block and Delete the Message Permanently: To prevent accidental interaction, block the sender and remove the email from your inbox.
What to Do If You Fell for a DocuSign Scam
Falling victim to a DocuSign scam can expose your personal and financial information to cybercriminals. Acting quickly and decisively can help minimize the damage and protect your identity.
Contact Banks or Card Issuers Immediately
Notify your bank, credit card companies, or financial institutions about the potential breach. They can monitor your accounts for suspicious activity, freeze compromised cards, and help prevent unauthorized transactions.
Use IdentityTheft.gov for Sensitive Info Exposure
If your personal information has been compromised, report the incident to IdentityTheft.gov. This official government site provides step-by-step recovery plans and resources to help you regain control of your identity.
Run Anti-Malware Scans and Seek Expert Help if Needed
Perform a thorough scan of your devices using trusted anti-malware software to detect and remove any malicious software installed through the scam. If you notice continued issues, consider consulting cybersecurity professionals for assistance.
Real vs. Fake: How Legit DocuSign Emails Actually Work
Understanding the key characteristics of genuine DocuSign emails can help you distinguish them from fraudulent attempts and avoid falling prey to scams.
| Key Characteristic | Description |
|---|---|
| Emails Contain a “Review Document” Button Only | Legitimate DocuSign emails include a clear call-to-action button labeled “Review Document” that directs you securely to their platform. |
| No Attachments or Credential Requests | Official DocuSign emails do not contain attachments or ask for login credentials via email links; authentication happens only on their secure site. |
| No Forced Account Creation | You are never required to create or register an account to view or sign a document. Signing can be done as a guest if permitted by the sender. |
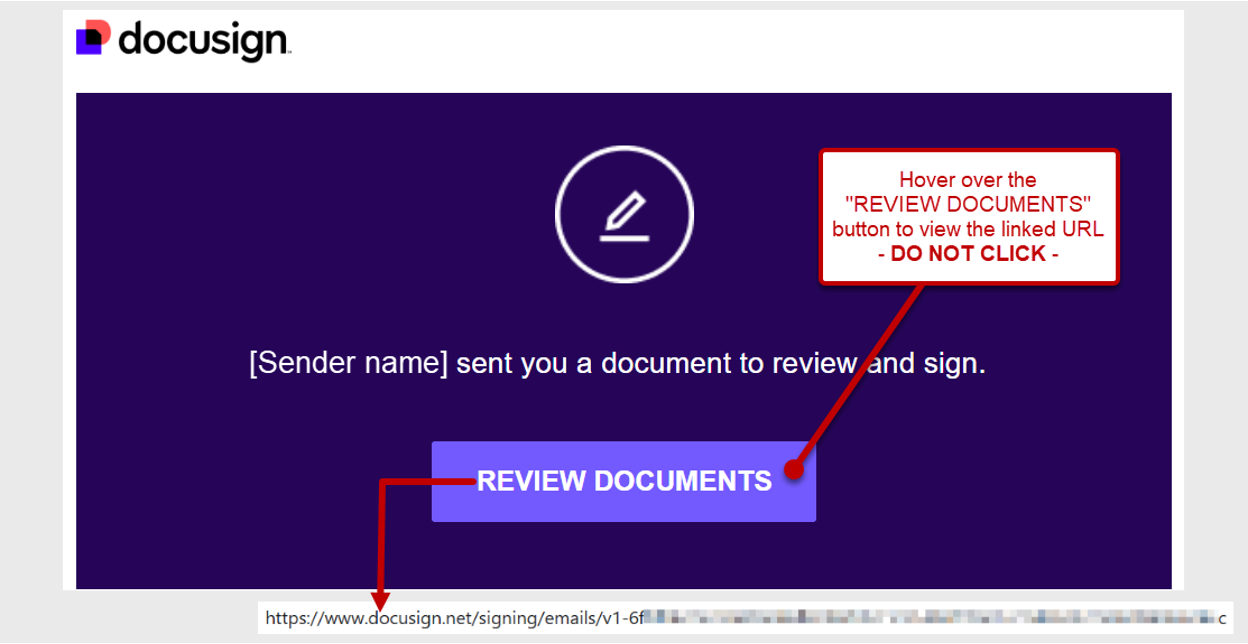
Docusign envelope email notifications will always be sent from @docusign.net domain. All Docusign envelope email notifications will also include a link that directs you to https://www.docusign.net where you can access and review the envelope contents. To ensure an envelope link is legitimate, simply hover over it without clicking, as shown in the image below.
Where and How to Report DocuSign Scams
Reporting DocuSign scams promptly helps protect you and others from phishing attacks and assists DocuSign in taking down fraudulent activities.
- Use DocuSign’s In-App Reporting Tools: If you receive a suspicious email or document within DocuSign, use the platform’s built-in “Report Abuse” or similar feature to notify their security team directly.
- Forward Phishing Attempts to spam@docusign.com: If you receive a suspicious email outside DocuSign’s platform, forward the entire email, including headers, to spam@docusign.com. To include headers, use your email client’s “Forward as Attachment” or “Show Original” feature before forwarding. This helps DocuSign analyze the phishing attempt and block similar emails.
- Submit URLs of Fake DocuSign Sites: If you come across a website pretending to be DocuSign but with a suspicious URL, report it along with any relevant screenshots. DocuSign’s security team can then work to take down these fraudulent sites or notify relevant authorities.
How Guardio Protects You from DocuSign Scams
Guardio is a complete security tool designed to safeguard users from phishing scams, including those targeting DocuSign users. It provides multiple layers of protection to help detect and block malicious activity before it can cause harm.
- Real-Time Link Scanning for Malicious URLs: Guardio continuously scans links in emails and websites as you browse, identifying and warning you about potentially harmful URLs before you click them.
- Blocking Known Phishing Pages Automatically: Guardio maintains an updated database of phishing sites and automatically blocks access to any pages identified as part of phishing or scam campaigns.
- Alerting Users About Impersonation or Scam Indicators: The tool detects suspicious signs like fake logos, unusual domain names, and other scam indicators, alerting you immediately to help you avoid falling for impersonation attempts.
- Removing Malicious Extensions or Browser Hijackers: Guardio also scans your browser for harmful extensions or hijackers that could compromise your security, removing them to maintain a safe browsing environment.
Conclusion
DocuSign scams are a growing threat that exploits the trust users place in this widely used digital signature platform. By understanding the common signs of phishing emails, recognizing what legitimate DocuSign communications look like, and knowing how to respond to suspicious messages, users can significantly reduce their risk of falling victim.
Taking proactive steps such as verifying emails through official channels, reporting scams promptly, and using security tools like Guardio can provide an added layer of protection. Staying informed and vigilant is essential to safely navigate digital communications and protect your sensitive information.
{{component-cta-custom}}
FAQs
How can I verify a DocuSign email is legitimate?
Check the sender details and where the links go. If you are unsure, do not click the email. Instead, go to DocuSign directly and look for the document in your account, or confirm with the sender using a separate channel.
Can scammers send DocuSign requests?
Yes. Scammers may use real e-sign tools or fake lookalike pages to trick you into signing in or downloading malware. Treat unexpected document requests as suspicious until verified.
What should I do if I opened a suspicious DocuSign link?
Close the page and avoid entering credentials. If you did enter details, change your password and enable two-factor authentication. Then review downloads and remove any unwanted extensions or apps.








