X Account Hacked? Here’s What to Do

Key Takeaways
- Check for unusual logins, profile changes, and unexpected messages
- Reset your password from the official site or app
- Enable two-step verification and review active sessions
- Remove unknown connected apps and extensions
- Real-time link protection can help block phishing pages used in takeovers
X account hacked? The moment you realize something’s wrong, act fast to regain control. Start by trying to log in and reset your password immediately. Next, check your email for any alerts or messages from X about suspicious activity or login attempts.
If you can’t log in, gather key details like your username, the email or phone number linked to the account, and any recent changes, and submit a recovery request to X Support. While waiting, keep an eye out for unusual posts or DMs sent from your account. Let your followers know not to click on any suspicious links.
Once you’re back in, secure your account by enabling two-factor authentication and updating your password to something strong and unique, and review connected apps. These quick steps can stop hackers in their tracks and help keep your account safe long-term.
X account hacks are more common than you think, as thousands of users fall victim every day. Hackers use tactics like phishing emails, weak or reused passwords, malware, and even data leaks to break into accounts. Some go after everyday users, while others target influencers and verified profiles. No one is immune, but it is possible to take steps to fight back.
This guide will walk you through exactly what to do if your X account is compromised - from spotting the early warning signs to recovering access and locking it down for good. Acting quickly and following a few simple steps can make all the difference in protecting your online identity.
{{component-cta-custom}}
How Do X Accounts Get Hacked: Common Methods
Even with security features in place, X accounts are frequently targeted by hackers using a variety of methods. BBC presenter Nick Robinson recently had his verified X account compromised and used to promote a cryptocurrency scam. Below are the most common ways attackers gain access and what makes each tactic so effective.
Phishing Scams
Phishing is the most common and effective method hackers employ to trick users into giving up their X account credentials.
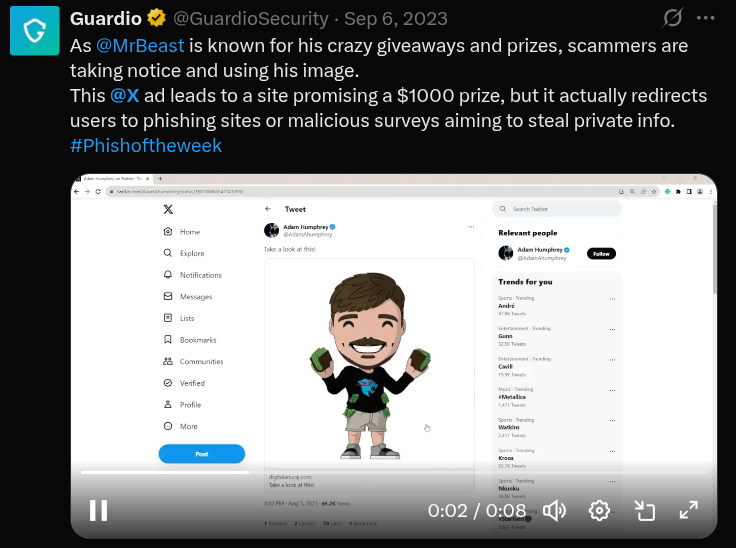
Phishing attacks often come in the form of fake emails, DMs, or websites that mimic the X login page. These messages typically claim there’s an urgent issue like a policy violation or suspicious login and prompt users to “verify” their account. Once credentials are entered on a fake page, hackers immediately gain access. Some phishing kits even simulate 2FA screens to steal verification codes in real-time.
Weak or Reused Passwords
A weak or reused password makes it easier for attackers to brute-force or guess your login details. Many users still rely on common passwords or reuse the same login across multiple sites. Hackers exploit this by using credential stuffing, which is a method where previously leaked username-password combinations from other sites are tested on X accounts. Tools used by attackers can attempt thousands of logins per minute, making reused passwords a major vulnerability.
Data Leaks on the Dark Web
Data breaches on unrelated platforms can expose personal details that are later used to hijack your X account. When a website suffers a breach, user emails and passwords are often sold on the dark web. If a user’s X account shares the same credentials, attackers can access it easily. Leaks may also contain personal data like phone numbers or backup email addresses, which hackers use to impersonate users during account recovery attempts.
Malware and Spyware Infections
Malware silently running in the background can steal saved passwords, capture keystrokes, or even hijack browser sessions. Malicious software often comes bundled with free downloads, pirated content, or rogue browser extensions. Once installed, it can log every key you type (including passwords), take screenshots, or even bypass 2FA if a session token is stolen. Many victims don’t realize they’re infected until their accounts start behaving suspiciously.
Man-in-the-Middle Attacks
Man-in-the-middle (MitM) attacks intercept your connection to steal login data, especially over unsecured networks. When using public Wi-Fi (like in airports or cafés), attackers can insert themselves between your device and the internet. By spoofing legitimate login pages or capturing unencrypted traffic, they can extract credentials or authentication tokens. Even encrypted connections can be at risk if a user clicks “accept” on a fake security certificate.
Vulnerabilities in Third-Party Apps
Granting access to unknown or poorly built third-party apps can expose your X account to serious security flaws. Many apps and browser extensions request permission to “Read and Post on your behalf” via X's API. If these apps are malicious or poorly maintained, they can be exploited to take over your account. Attackers may also create fake productivity tools or follower-boosting services to trick users into granting access. Once permissions are in place, the app doesn’t need your password to post or message others.
Lack of Two-Factor Authentication (2FA)
Without 2FA, all a hacker needs is your password, and that’s often easier to get. Two-factor authentication adds an extra layer of protection by requiring a second step to log in (like a code from your phone). Yet many users skip it, assuming a strong password is enough. Even when 2FA is enabled, hackers may try to trick you into revealing codes through phishing or SIM-swap scams.
Rebranding of Twitter to X
The rebranding of Twitter to X created fresh opportunities for scammers, who quickly adapted by launching lookalike accounts and impersonation scams under the new identity. According to Guardio’s report on X rebrand scams, many users were caught off guard by fake customer support pages, phishing DMs, and impersonated announcements pretending to come from X’s new official channels.
Recognizing Signs of a Hacked X Account
Hackers rarely leave obvious traces, but there are key indicators that your X account may have been compromised. Here’s what to look for:
- Unexpected Posts or Messages
If your account is sending tweets, replies, or DMs you didn’t write, it’s likely someone else has access. These messages often contain spam, suspicious links, or crypto scams. Even if the content seems harmless, any unexplained activity should be treated as a red flag.
- Login Alerts from Unknown Locations
X sends security notifications when your account is accessed from a new device or location. If you receive an alert for a login you don’t recognize, especially from a different country or city, then it’s a strong sign someone else has access to your account.
- Inability to Access Your Account
Being locked out of your account, especially if your password no longer works, may mean the attacker has already changed your credentials. This is a serious sign of a full account takeover and should be addressed immediately using the account recovery process.
- Altered Account Information
Check for changes to your email address, username, display name, bio, or phone number. Hackers often update these details to lock you out or make the account harder to recover. Even small edits, like a removed recovery option, can indicate tampering.
- Notifications About Password Changes You Didn't Initiate
If you receive an email or text from X about a password change you didn’t request, assume someone else triggered it. These alerts are time-sensitive, so the faster you respond, the better your chances of regaining control.
Spotting even one of these signs early can help prevent further damage and speed up recovery.
4 Immediate Steps to Recover Your X Account
Getting hacked is stressful, but quick action can help you regain control before further damage is done. Follow these four essential steps as soon as you notice suspicious activity.
1. Attempting to Log In and Reset Passwords
Start by checking if you can still access your account. If you're able to log in, immediately change your password to something strong and unique.
Go to Settings → Your Account → Change your password.
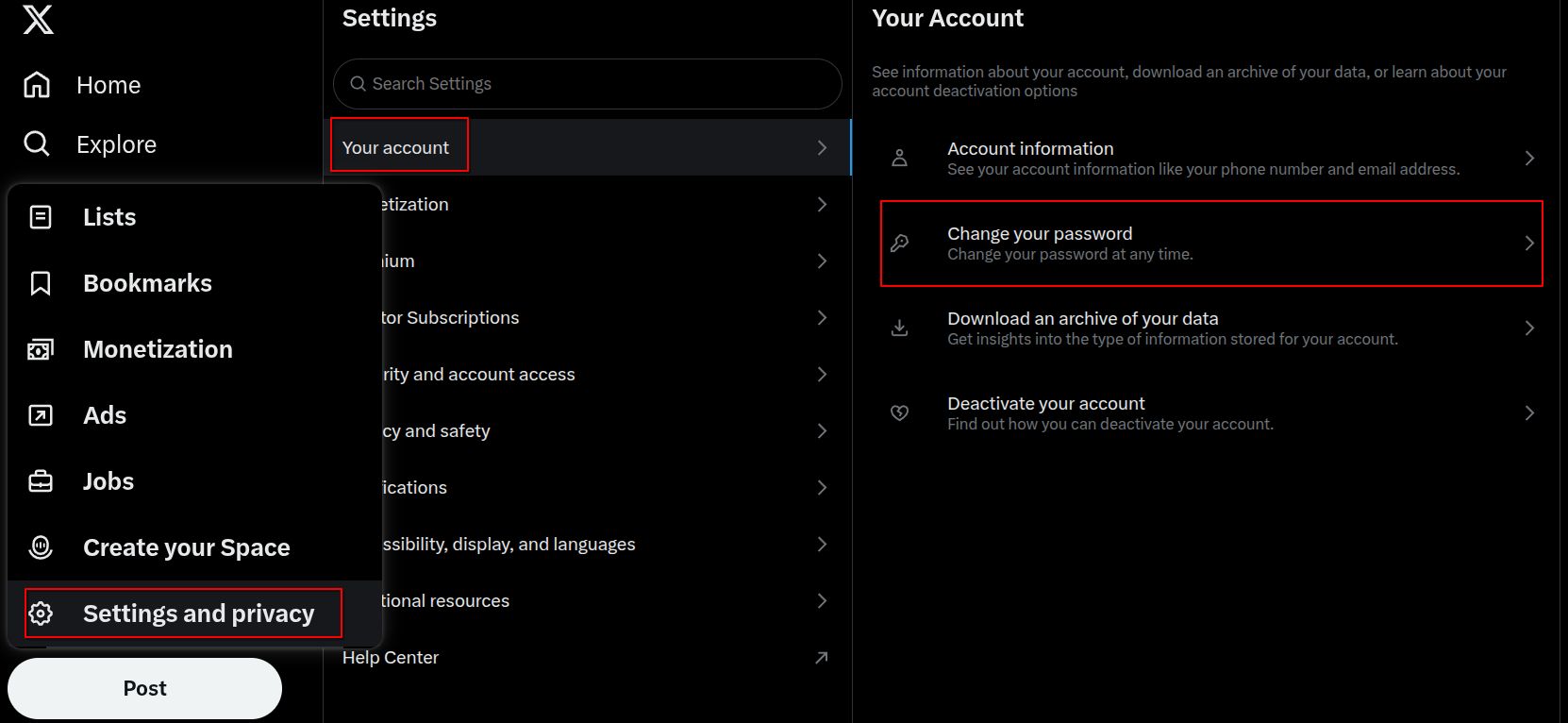
If you're locked out, use the Forgot Password link on the login page to trigger a password reset email or SMS. If this doesn’t work, it may mean the hacker has already altered your recovery details.
2. Gathering Necessary Information for Account Recovery
Before contacting X Support, collect all relevant information to help prove account ownership. This includes:
- The email address or phone number linked to your account
- The exact @username (handle)
- A screenshot of your profile, if possible
- Details about recent activity (e.g., last login, known devices)
Having this data ready speeds up the verification process with support.
3. Submitting Recovery Forms to X Support
If you can’t reset your password, go to the official X Help Center and file an account recovery request. Be specific about what happened, for example, mention if the account was hacked, if recovery info was changed, or if there was suspicious posting activity. The more accurate the report, the faster the chances of it being resolved.
4. Monitoring for Follow-Up Communications
After submitting the recovery request, regularly check your email (including the spam/junk folder) for any updates from X Support. They may ask for further proof of identity or notify you of a status update. Recovery time depends on how badly your account was compromised and whether recovery details are still intact. Below is a table summarizing typical scenarios and timelines:
| Recovery Scenario | Estimated Timeframe | Notes |
|---|---|---|
| Password reset with email/SMS access | Within minutes to 1 hour | Fastest method if no changes were made to recovery info. |
| Account compromised, but still logged in | 1-2 hours | Change password and revoke access to suspicious apps immediately. |
| Lost access to email or phone | 1-3 days | Requires identity verification and alternate recovery proof. |
| Submitted recovery form to X Support | 3-7 business days | Response times vary. Keep checking spam folders and be patient. |
| High-profile or verified account recovery | Up to 2 weeks or more | Often escalated but may involve manual review for security reasons. |
| Reported impersonation or phishing-related hack | 5-10 days | May require additional verification and incident details. |
Be patient and do not submit multiple tickets, as that can delay your case. In the meantime, avoid engaging with the hacked account, and alert your followers if it’s being used to spread scams.
Why Acting Quickly Matters After a Hack
Time is critical after a hack. Delaying action even by a few hours can make recovery much harder and increase the potential damage. Here’s why immediate steps are essential:
- Hackers Can Lock You Out Completely: Once inside your account, attackers often change your password, recovery email, and phone number. This prevents you from using standard recovery tools and forces you into a lengthy support process. The faster you act, the more likely you are to regain access before they secure control.
- Sensitive Messages and Photos May Be Leaked: If your account contains private DMs or media, hackers can view, screenshot, or even post them publicly. Even deleted content may still be visible through the account archive. A quick response limits exposure and reduces the chance of personal or reputational damage.
- Scammers May Use Your Identity to Target Others: A compromised X account is often used to trick your followers, especially if you’re a public figure or run a brand. Attackers may send phishing links, fake crypto giveaways, or impersonation messages that appear to come from you, damaging your credibility and putting others at risk.
- Linked Apps and Services Could Also Be Compromised: Many users connect their X account to other apps and platforms (like scheduling tools, ad accounts, or email systems). Hackers can exploit these integrations to expand their reach or access even more of your data. For example, the wallet integration with X could compromise the security of your account.
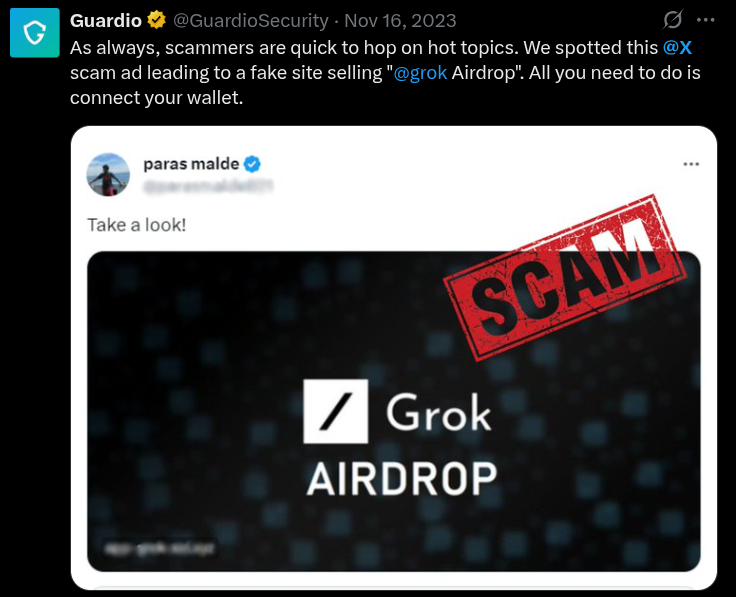
Taking immediate steps can significantly mitigate the impact, protect your network, and support a smoother recovery process.
{{component-tips}}
Best Practices to Secure Your X Account
Once your account is recovered - or even better, before it's ever compromised - adopting strong security habits can drastically reduce your risk of future hacks. These best practices offer long-term protection with minimal effort:
Enabling Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a second verification step beyond your password, typically a one-time code sent via SMS or generated by an authentication app. To enable it:
Go to Settings -> Security and Account Access -> Security -> Two-Factor Authentication.
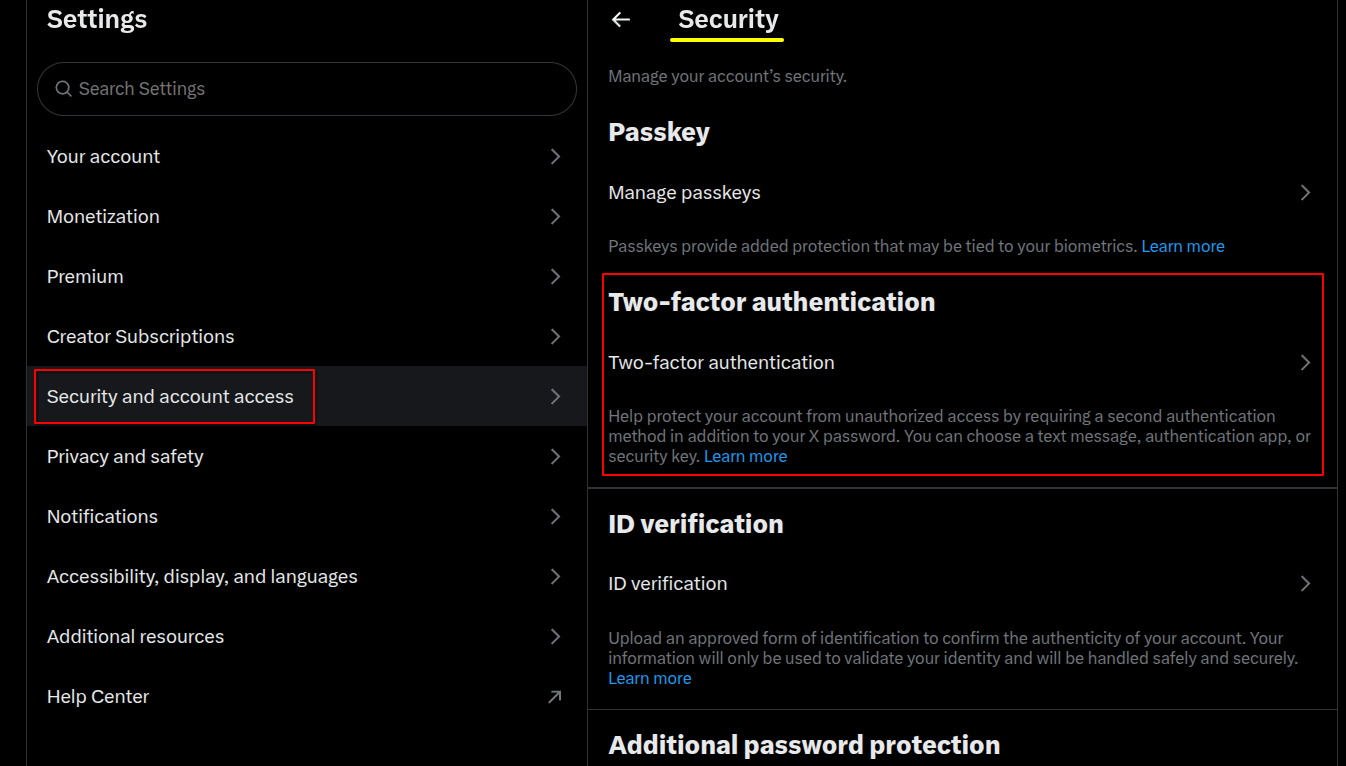
App-based 2FA (like Authy or Google Authenticator) is recommended over SMS for stronger protection.
Creating Strong, Unique Passwords
Your password is your first line of defense. Avoid using names, birthdays, or dictionary words. Instead, use a password manager to generate and store complex, unique passwords for every account. A strong password should be at least 12 characters long, combining uppercase, lowercase, numbers, and special symbols.
Avoiding Suspicious Links and Emails
Phishing remains a top method for account takeovers. Be cautious when clicking on links in DMs, emails, or tweets, especially those urging urgent action or asking for credentials. Legitimate services like X will never ask you to verify your login through unofficial pages or direct messages.
Regularly Reviewing App Permissions
Over time, you may grant third-party apps access to your X account. Some of these apps may become outdated or compromised, making them a hidden risk. Audit them regularly:
Go to Settings → Security and Account Access → Apps and Sessions → Connected Apps
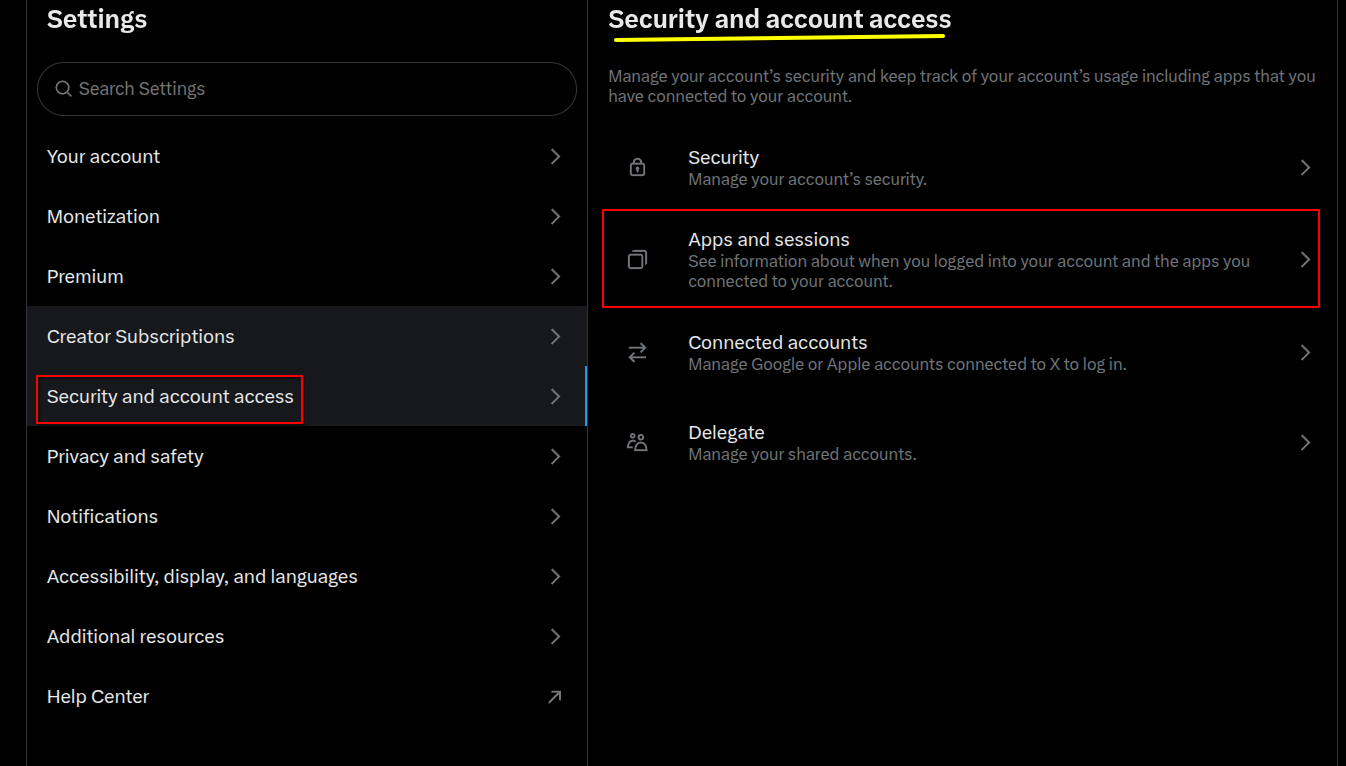
Revoke any integrations you no longer use or recognize.
Practicing Safe Browsing Habits
Browser-based attacks like malicious extensions or drive-by downloads can compromise your entire device, including social media logins. Always keep your browser and antivirus tools updated, avoid sketchy websites, and use browser extensions from trusted developers only.
How Guardio Enhances Your Account Security
Guardio is a security solution designed to proactively protect users from a wide range of online threats. By integrating real-time monitoring and threat prevention directly into your browser, Guardio offers an additional layer of defense against cyberattacks targeting your X account and other digital assets.
Blocking Malicious Websites and Phishing Attempts
Guardio actively scans websites you visit, blocking access to malicious sites and phishing pages that attempt to steal your credentials or personal information. This real-time protection helps prevent accidental exposure to harmful content while browsing.

Scanning for Harmful or Hijacking Browser Extensions
Malicious browser extensions can compromise your security by hijacking search results, injecting ads, or tracking your activity. Guardio detects and neutralizes such extensions, ensuring your browser remains secure and functions as intended.
Monitoring the Dark Web for Leaked Email Credentials
Guardio monitors the dark web for any instances of your email addresses or phone numbers appearing in data breaches.
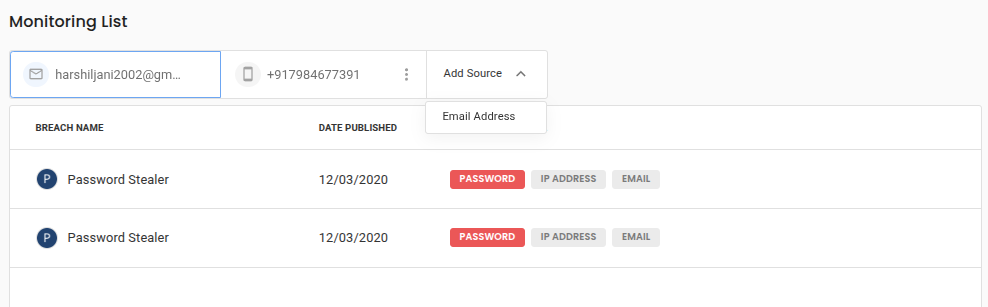
If a leak is detected, Guardio not only alerts you immediately but also helps you change exposed passwords and activate 2FA to prevent identity theft.
Providing Real-Time Alerts About Data Breaches and Threats
In the event of a data breach or emerging threat, Guardio delivers real-time alerts to keep you informed. These notifications enable you to respond promptly, mitigating potential damage from compromised accounts or personal information.
Alerting You to Suspicious Browser Activity That Could Lead to Account Compromise
Guardio monitors your browser for unusual activity, such as unauthorized access attempts or changes to settings that could indicate a security threat. By detecting these anomalies early, Guardio helps prevent potential account compromises.
Guidance on Securing Accounts After a Breach
When Guardio detects that your credentials have been leaked or exposed, it doesn’t just alert you, it also walks you through the next steps. You’ll receive clear recommendations on changing your password, selecting a stronger one if needed, and enabling two-factor authentication (2FA) for better protection. Guardio makes it simple to act on alerts, so you can strengthen your account security right away.
Conclusion
Having your X account hacked can be frustrating. Most hacks happen due to weak passwords, phishing scams, or missing two-factor authentication. Recognizing these risks and spotting early warning signs like unexpected posts or login alerts can help you respond quickly.
Simple habits like enabling 2FA, creating strong passwords, and regularly checking app permissions go a long way in securing your account. Additionally, tools like Guardio provide valuable support by blocking malicious websites, detecting harmful browser extensions, monitoring the dark web for leaked credentials, and sending real-time alerts about suspicious activity.
By combining these best practices with Guardio’s proactive security features, including alerts, password guidance, and 2FA setup support, you can significantly reduce the risk of your X account being compromised and keep your online presence safe and secure.
FAQs
How can I tell if my X account was taken over?
Common signs include posts you did not create, DMs you did not send, profile changes, or unexpected login alerts. If you see these, change your password and review active sessions quickly.
What should I do right after I regain access?
Change your password, enable two-factor authentication, review connected apps, and log out of other sessions. Also check your email account security if it is tied to X.
How do most social account takeovers happen?
Many start with phishing links or reused passwords from older breaches. Using unique passwords and two-factor authentication, and being cautious with login links, lowers the risk.
What should I do first after I regain access?
Change your password, enable two-step verification, review active sessions, and remove unknown connected apps.
How do account takeovers usually happen?
Common causes include phishing links, reused passwords from older breaches, and risky extensions or apps that capture logins.
Should I contact support right away?
If you cannot regain access quickly, contact support through the official help center. Avoid support links from messages.








