Is Your Amazon Account Hacked? 6 Red Flags & Recovery Steps

Key Takeaways
- Check for unusual logins, profile changes, and unexpected messages
- Reset your password from the official site or app
- Enable two-step verification and review active sessions
- Remove unknown connected apps and extensions
- Real-time link protection can help block phishing pages used in takeovers
Think your Amazon account is acting strangely? Unexpected orders, odd delivery addresses, or login alerts from unfamiliar locations aren’t random bugs. They’re often signs that your account has been hacked.
With millions of users and stored payment methods, Amazon is a prime target for cybercriminals. From phishing scams to data leaks, attackers use a range of tactics to breach accounts and steal personal data. And once they’re in, the fallout can spread well beyond Amazon, impacting your finances, identity, and digital life.
This guide highlights key warning signs, gives you recovery steps, and shows how to protect yourself with tools like Guardio.
{{component-cta-custom}}
6 Signs Your Amazon Account Has Been Hacked
Amazon hacks more often slip in quietly by making subtle changes that only sharp eyes catch. If your account feels even slightly off, don’t ignore it. Here are six red flags that suggest your Amazon account is hacked:
1. Suspicious Login Alerts or Unknown Devices
If you receive an email or app notification about a login from a location you don’t recognize, especially if it's a country you've never visited, that's a serious red flag. Check your account’s login history and device activity under the Your Devices section.

Any unfamiliar presence could mean someone else is browsing your Amazon on your behalf.
2. Unauthorized Orders or Charges
Did a mystery package arrive at your doorstep? Or worse, was your bank account charged for an item you never ordered? This is one of the clearest signs your account has been compromised.
Go to Your Orders and look for anything you didn’t purchase. Hackers may also cancel your real orders and replace them with their own.
3. Changes to Order or Delivery Details
Sometimes, cybercriminals don’t make new purchases; they hijack existing ones. Watch for changed shipping addresses, updated delivery instructions, or modified order items. This technique allows hackers to piggyback on your legitimate transactions to reroute valuable items to their own locations.
4. New or Unrecognized Payment Methods Added
Head over to Payment Options. If you see credit cards or gift cards you don’t recognize, it’s likely your account was accessed and updated by someone else. Hackers often add temporary or prepaid cards, use them for quick purchases, and vanish before the fraud is noticed.
5. Unfamiliar Product Reviews or Activity Under Your Name
Amazon is also a massive platform for seller accounts and product manipulation. If you see reviews you didn’t write or browsing history you don’t recognize, your account may have been used as a bot or dummy account. This activity is especially common in accounts that have been hacked but not fully exploited.
6. Unfamiliar Shipping Addresses Added
Visit your Address Book. If there are addresses that aren’t yours and it is in another state or country, that’s a red alert. Hackers often add a new address and switch it at checkout. If you don’t check this section regularly, you might miss the fact that your order is being delivered to a stranger.
Key Steps to Recover and Secure a Hacked Amazon Account
If your Amazon account has been compromised, swift and strategic action is your best defense. These six steps can help you regain control and prevent further damage.
| Action | Why It Matters |
|---|---|
| Change Your Password and Secure Your Email | If your email is compromised, hackers can regain access even after a password change. Lock both down immediately. |
| Enable Two-Factor Authentication on Amazon | 2FA adds a barrier hackers can't bypass without physical access to your device. |
| Review and Revoke Unauthorized Devices | Hackers often stay logged in silently, so revoking access cuts off their session instantly. |
| Report Fraudulent Activity to Amazon Support | Amazon’s fraud team can reverse unauthorized purchases and flag your account for added monitoring. |
| Monitor Linked Payment Methods and Orders | Attackers may have added cards or made hidden purchases, so review everything tied to your account. |
| Restore Account Settings After Regaining Access | Don’t overlook changes to your address book, preferences, or notifications, as they can open doors for repeat attacks. |
Securing your Amazon account isn’t just about stopping one breach but about closing every loophole hackers can exploit.
What to Do if You’re Locked Out of Your Amazon Account
Getting locked out of your Amazon account, especially after spotting suspicious activity, can be alarming. Whether it’s due to a hacker changing your password or Amazon temporarily freezing your access for safety, here’s how to take back control quickly and securely:
1. Contact Amazon Support Immediately
Start by heading straight to Amazon’s Customer Support and choosing the option “I can’t log into my account.” Use the live chat or phone callback if available since they’re often faster than email. Clearly explain that you believe your Amazon account is hacked and you're locked out. Don’t wait for things to escalate. Taking early action can help prevent further misuse of your data or bank account.
2. Verify Your Identity and Follow Recovery Steps
Amazon will usually prompt you to verify your identity using your registered email, phone number, or billing information. Have any relevant order details or payment methods ready, especially if your account information was recently changed. Follow the account recovery instructions carefully as this might include receiving a verification code or answering security questions.
3. Monitor Email for Recovery Instructions
After initiating recovery, keep an eye on your inbox (including the spam folder). Amazon may send multiple follow-up emails with status updates, temporary links, or next steps. Don’t click on any lookalike phishing emails pretending to be Amazon and always verify sender details and URLs carefully. Once you're back in, make sure to update your password, enable two-factor authentication, and review account activity immediately.
{{component-tips}}
Common Ways Amazon Accounts Get Hacked
Understanding how your Amazon account can be compromised is the first step to building smarter defenses. Here are the three most common methods attackers use to hijack Amazon accounts:
Phishing Emails and Fake Login Pages
Cybercriminals frequently send deceptive emails that appear to originate from Amazon customer service, prompting users to verify information or resolve account issues. These emails often contain links to counterfeit login pages designed to capture credentials. Once submitted, the attacker gains direct access to the account.
(1/4) These two URLs look identical, but the top one takes you to a fake site while the other directs you to the actual Amazon site. How is this possible?🧵 pic.twitter.com/UZmYEa13Ky
Guardio (@GuardioSecurity) August 21, 2023
To avoid falling victim, always verify the sender’s email domain and avoid clicking suspicious links. Amazon will never request sensitive account information via email.
How Guardio helps: Guardio detects fake Amazon login pages in real-time, warning you before you enter your credentials.
Malware or Malicious Browser Extensions
Some malicious browser extensions or downloaded files may contain spyware or keyloggers capable of tracking your activity, including credentials entered on Amazon. These tools operate in the background, often undetected, and can compromise not just your Amazon account but other online accounts linked through your browser. Regularly review installed extensions, limit unnecessary downloads, and consider using security solutions like Guardio to detect and block malicious scripts or plugins.
Over 1 million people use Guardio to catch threats like these before they cause damage.
Credential Stuffing from Other Data Breaches
One of the most common methods of unauthorized access is through credential stuffing. If you’ve used the same password on another site that experienced a data breach, attackers may attempt to log in to your Amazon account using those exposed credentials. To mitigate this risk, adopt a password manager to generate and store strong, unique passwords across all platforms.
How Hackers Exploit Amazon Accounts
The goal for hackers isn’t always immediate financial gain, but it’s often to extract maximum value with minimal visibility. Below are common ways attackers misuse compromised Amazon accounts:
Reselling Goods Purchased With Stored Cards
With access to saved payment methods, hackers can purchase high-demand products such as electronics or gift cards and quickly resell them on secondary markets. These purchases are often small and spaced out to avoid triggering fraud detection. In some cases, victims only realize what happened after reviewing their monthly bank account statement.
Changing Delivery Addresses to Reship Items
Rather than shipping items to the victim’s registered address, attackers often add new shipping addresses or use drop locations. They may even intercept or reroute existing orders to these new addresses. This tactic allows them to receive goods while keeping the victim unaware until a missing delivery or order alert raises suspicion.
Using Amazon as Entry Point to Other Accounts
Because Amazon accounts are often linked to email addresses, saved payment methods, and other online accounts, a breach can extend beyond Amazon itself. Hackers may use information gathered, such as billing details, login habits, or communication preferences, to access other platforms, leading to broader incidents of identity theft or fraud.
Preventing Future Amazon Account Hacks
Proactive security habits are your best defense against future breaches. Implementing the following practices can significantly reduce the risk of unauthorized access to your Amazon and other online accounts.
| Prevention Tip | Why It Matters |
|---|---|
| Use Strong, Unique Passwords | Reusing the same password across multiple accounts increases vulnerability to credential stuffing. A unique password for Amazon helps isolate and contain threats. |
| Regularly Update Your Login Details | Periodically updating your Amazon password and account recovery settings ensures that stale credentials or old contact information don't become weak points. |
| Avoid Public Wi-Fi for Sensitive Transactions | Public networks are often unencrypted, allowing attackers to intercept login details and account information during checkout or account access. |
| Stay Informed About Phishing and Scam Tactics | Being able to recognize suspicious emails, fake login prompts, or deceptive browser pop-ups is critical for protecting against evolving threats. Awareness is your frontline defense. |
Tools and Resources for Ongoing Account Protection
Even the most vigilant users can fall victim to evolving cyber threats. That’s why using the right tools is just as important as developing secure habits. The following resources can help you maintain long-term protection for your Amazon account and other online accounts:
Password Managers for Unique Credentials
A password manager securely stores and generates strong, unique passwords for each of your accounts.
This eliminates the need to remember multiple logins and drastically reduces the risk of using the same password across platforms. Top options include 1Password, Bitwarden, and Dashlane.
Browser Extensions for Real-Time Phishing Protection
Certain security-focused browser extensions monitor websites in real time and flag suspicious behavior, such as fake login pages or malicious redirects. These tools help prevent phishing attacks by warning you before you enter sensitive information. Guardio provides real-time protection against malicious pop-ups and browser-based exploits through its multi-layered security platform, which includes a browser extension as one key component.
Alerts for Credential Leaks or Dark Web Activity
Many services including Guardio now offer breach monitoring that scans the dark web for your exposed credentials. These tools notify you if your account information appears in known data breaches, allowing you to act quickly. Some password managers and cybersecurity platforms include this feature automatically.
Antivirus and Device Security Software
Robust antivirus software helps protect your devices from malware, spyware, and keyloggers that can silently steal sensitive data, including Amazon login credentials. In addition to traditional antivirus tools, browser-first security solutions like Guardio offer real-time protection against malicious extensions, phishing attempts, and suspicious downloads, addressing threats that traditional antivirus might overlook.
How Guardio Can Help if Your Amazon Account is Hacked
While recovering from an Amazon account breach can be overwhelming, having the right tools in place can reduce the risk and response time dramatically. Guardio is designed to provide real-time, proactive protection against the very tactics hackers use to infiltrate and exploit online accounts. Here’s how Guardio works to keep your Amazon account safe:
- Detects phishing attempts and fake Amazon login pages by scanning sites in real time, preventing credential theft before it happens.
Don’t let your #PrimeDay turn into a crime day. It's easy for scammers to take advantage of big online shopping events. Be on the lookout for sites imitating Amazon, and double-check any special offers or gift cards you come across.👇 pic.twitter.com/CPs5mAyl1b
Guardio (@GuardioSecurity) July 11, 2023
- Blocks malicious browser extensions and hidden scripts that could monitor your activity or inject harmful code into legitimate Amazon pages.
- Alerts you if your Amazon credentials or email appear in data breaches so you can immediately take action to secure your accounts.
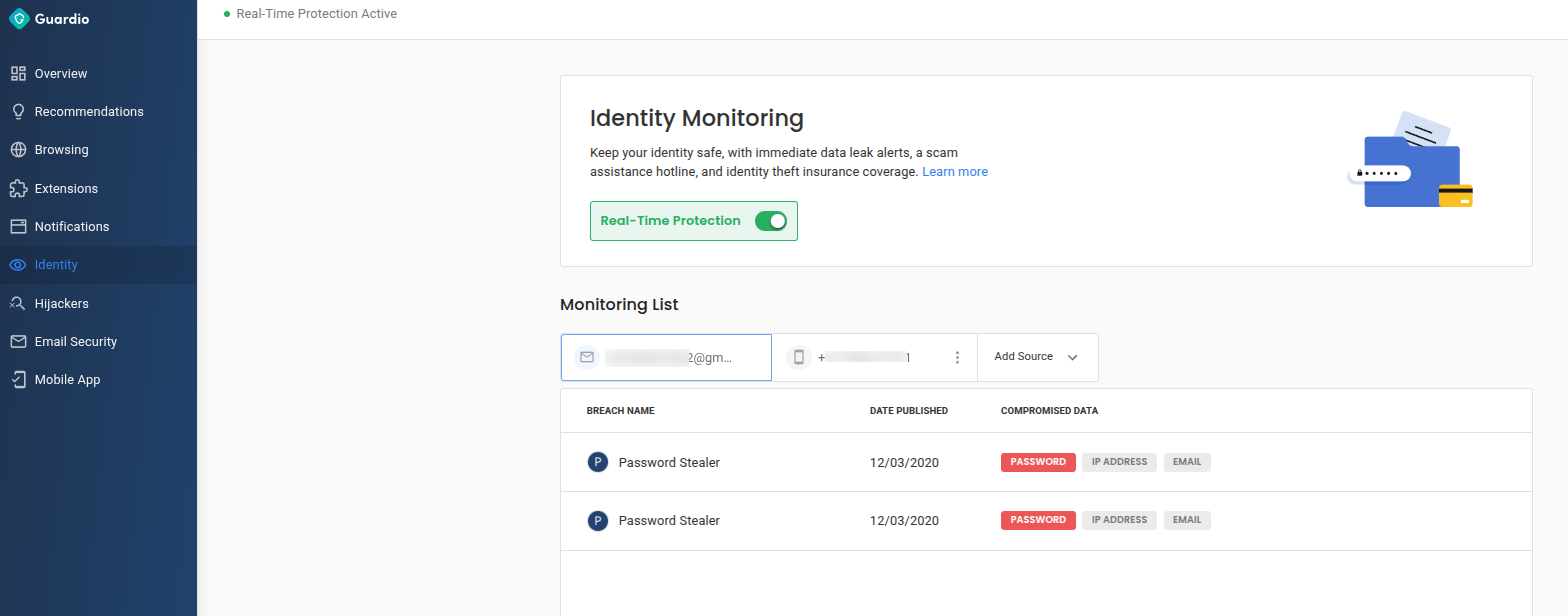
- Provides tools to enhance your overall online security, including breach monitoring, site reputation checks, and unsafe link blocking, all tailored for real-world browsing habits.
Conclusion
Your Amazon account isn’t just a shopping profile but a gateway to your personal data, payment methods, and digital identity. If it’s hacked, the consequences can spill far beyond a few unauthorized orders. Recognizing the red flags early, responding with the right recovery steps, and building long-term digital hygiene are all essential in staying one step ahead.
Threats come through reused passwords, phishing links, or invisible browser traps. That’s why protecting your account isn’t just a one-time fix, but a continuous commitment. Tools like Guardio help tip the balance in your favor by giving you real-time awareness and protection where the threats begin.
{{component-cta-custom}}
FAQs
How can I tell if a amazon account hacked message or page is real?
Start by verifying where the link goes and who sent it. If anything feels rushed or unusual, do not click. Open the official site or app directly and check your account there.
What should I do if I already clicked or entered details?
Close the page, then sign in from the official site to review recent activity. If you entered a password, change it and enable two-step verification. Watch for unusual messages, logins, or transactions.
What is the safest way to verify Is Your Amazon Account Hacked? 6 Red Flags & Recovery Steps?
Use a trusted path: type the site address yourself, use a saved bookmark, or open the service app. Avoid verifying through message links, especially when the message creates urgency.
What should I do first after I regain access?
Change your password, enable two-step verification, review active sessions, and remove unknown connected apps.
How do account takeovers usually happen?
Common causes include phishing links, reused passwords from older breaches, and risky extensions or apps that capture logins.
Should I contact support right away?
If you cannot regain access quickly, contact support through the official help center. Avoid support links from messages.








