Different types of hackers
Nowadays, the term "hacker" is used frequently, but it encompasses a broad range of individuals with different motivations and methods. Understanding the various types of hackers and their activities can help demystify the often misunderstood world of hacking.
Hackers
A hacker is someone skilled in computer systems, networks, and programming who uses this knowledge to solve problems. Like superheroes or villains, hackers can use their skills for both good and bad purposes.
Hacking
Hacking refers to the act of breaking into computer systems, networks, or software. While it often has a negative connotation, hacking can be ethical or malicious depending on the hacker's intentions.
Hacktivism
Hacktivism is the use of hacking to promote political or social agendas. Hacktivists attack systems to bring attention to their causes, such as exposing corruption or advocating for human rights. A notable example is the group Anonymous, which launched attacks on the Church of Scientology, supported the Occupy Wall Street movement by taking down websites and leaking sensitive information, and targeted Russian websites after the invasion of Ukraine in response to political tensions.
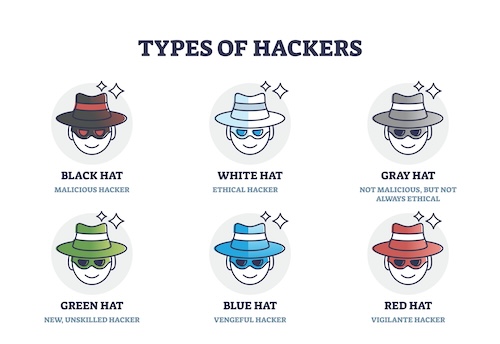
White hat hacker
White hat hackers, also known as ethical hackers, use their skills to improve security. They are often employed by companies to find and fix security vulnerabilities before malicious hackers can exploit them. For instance, in 2021, a white hat hacker named Santiago Lopez became the first hacker to earn $1 million through HackerOne's bug bounty program by identifying security vulnerabilities in major companies like Twitter and Verizon.
Black hat hacker
Black hat hackers are the "bad guys" of the hacking world. They exploit vulnerabilities for personal gain, such as stealing credit card information, spreading malware, or causing disruptions. An infamous example is the 2017 Equifax breach, where black hat hackers exploited a vulnerability to steal the personal information of 147 million people, including Social Security numbers, birth dates, and addresses.
Grey hat hacker
Grey hat hackers fall somewhere between white hats and black hats. They might break into systems without permission, but instead of causing harm, they report vulnerabilities to the owners—sometimes expecting a reward. In 2016, a grey hat hacker known as "Peace" hacked LinkedIn and sold over 100 million user credentials on the dark web. Although this act was illegal, it exposed significant security flaws that LinkedIn then worked to fix.
Green hat hacker
Green hat hackers are newcomers to the hacking world. They are eager to learn and often seek out the guidance of more experienced hackers. They are not as skilled but are motivated to improve their knowledge. Think of them as apprentices in the hacking community, participating in forums and learning from tutorials.
Blue hat hacker
Blue hat hackers are typically outside security experts invited by companies to test their systems for vulnerabilities before a product launch. They are not regular employees but are brought in to find and fix security issues. Microsoft, for example, organizes the BlueHat conference, where security professionals and hackers are invited to discuss vulnerabilities and security threats to improve their products.
Red hat hacker
Red hat hackers, also known as vigilante hackers, take a more aggressive stance against black hat hackers. Instead of just reporting malicious activity, they go on the offensive, hacking into the hackers' systems to shut them down. They act as a kind of digital vigilante, fighting fire with fire. A real-world example is the group of anonymous hackers who targeted and took down the DarkSide ransomware group's infrastructure after the Colonial Pipeline attack in 2021.
While exploring the colorful world of hackers, there's one thing that's totally clear — protecting your personal and professional data from malicious attacks is more important than ever. Whether it's black hat hackers looking to exploit vulnerabilities for personal gain or grey hat hackers exposing flaws without permission, the threats are real and constantly evolving. This is where comprehensive cybersecurity solutions like Guardio come into play. Guardio not only protects your devices from malware and phishing attempts but also offers proactive protection by scanning for vulnerabilities and keeping your information secure.
Guardio's advanced features ensure that you're always a step ahead of cybercriminals. With real-time threat detection, automatic blocking of dangerous websites, and alerts about potential breaches, Guardio acts as your digital bodyguard. It even helps you manage and protect your social media accounts, preventing unauthorized access and safeguarding your online presence. With over 1.5 million satisfied users, Guardio is your trusted ally in maintaining a safe and secure digital life. Don't wait for a breach to happen—try Guardio's 7-day free trial today and experience the peace of mind that comes with top-notch cybersecurity.
It's worth every penny I pay. Guardio cleaned up problems that I put up with for years. And I love the fact that I can email and get a response almost immediately with a solution
Lawana Crosiar
FacebookBest site security I have found.
Steve Popz May
TrustpilotAlways on the ball
Always on the ball, keeping me secure, day and night!
Allen J. Exelby
Trustpilot