What to Do If My Instagram Account Gets Hacked

Key Takeaways
- Check for unusual logins, profile changes, and unexpected messages
- Reset your password from the official site or app
- Enable two-step verification and review active sessions
- Remove unknown connected apps and extensions
- Real-time link protection can help block phishing pages used in takeovers
If your Instagram account was hacked, the most important thing is to stay calm and act quickly. The faster you move, the better your chances of getting your account back and stopping the hacker from doing more damage. Start by trying to log in. If you still have access, change your password right away and check for anything that looks strange. This could be messages you didn’t send, photos you didn’t post, or settings that were altered. If you can’t log in, don’t worry. Instagram has ways to help you recover your account, and we’ll guide you through all of it in this article.
Instagram hacks are pretty common these days. Hackers usually get in through phishing scams, weak passwords, or leaks from other websites. Once they’re in, they can steal your identity, scam your followers, or get access to your personal info. The good news is that with the right steps and tools like Guardio, which helps block online threats, you can take back control of your account and protect it from future hacks. In this guide, you’ll learn how to spot if your account was hacked, how to recover it, how hackers usually get in, and how to keep your Instagram safe moving forward.
How to Recognize the Signs of a Hacked Instagram Account
Spotting a hack early can save your account and protect your personal information. Here are the most common signs that something isn’t quite right with your Instagram account:
Unexpected Logouts or Changed Credentials

If you’re suddenly logged out of your Instagram account for no reason, it could be a red flag. Hackers often change your password or email right after gaining access, so you can’t log back in. If you try to reset your password and find that your recovery email or phone number no longer works, someone may have already taken over your account.
Posts or Messages I Didn’t Send
Unusual activity is a strong sign that your account was hacked. Check for messages you didn’t send, strange posts on your feed or Stories, or followers saying they got weird DMs from you. Hackers often send out scam links or fake offers using your profile to trick your friends or followers into clicking dangerous links.
Security Alerts from Instagram or Meta
Security warnings should never be ignored. If Instagram or Meta sends you alerts like “Your email was changed” or “Suspicious login detected,” pay attention. These are signs that someone is trying to get into your account or has already succeeded. Check your login activity under Instagram settings to see if there are unfamiliar devices or locations listed.
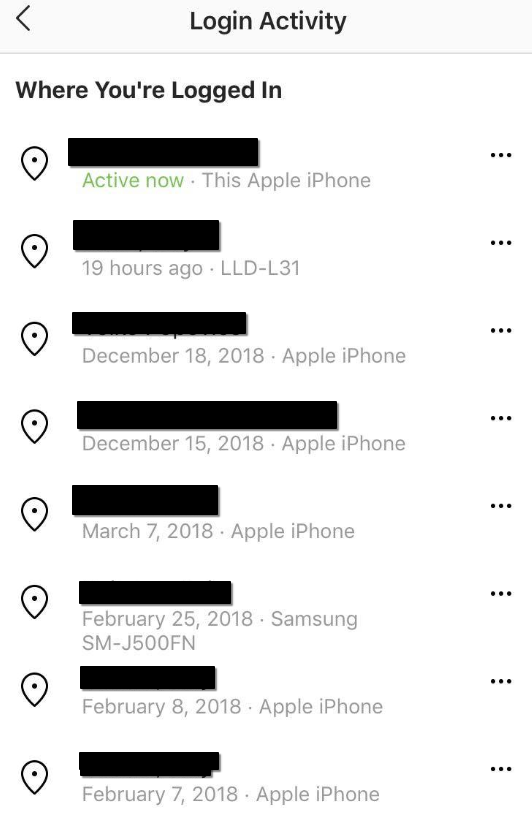
Linked Email or Phone Number Changed
If your recovery info is no longer yours, act fast. Hackers often switch out the linked email and phone number as soon as they get in. That way, you can’t receive password reset links. If you notice these changes and didn’t make them yourself, your account may already be compromised.
Immediate Steps to Take After Getting Hacked on Instagram
If you realize your Instagram account has been hacked, don’t panic. Act fast to secure your account and prevent further damage. Here are the steps you should take:
- Log in via Username or Email: Start by attempting to log in with your username or email. If you’re still able to access your account, change your password immediately. Once you've updated your password, make sure to log out of all devices to forcefully disconnect any unauthorized users who might still be signed in. If not, proceed to the next steps to recover it.
- Request a Login Link from Instagram: If you're locked out, go to Instagram’s login page and click on “Forgot password?”

Instagram will send a login link to your email or phone number, allowing you to regain access. Always request login links directly from Instagram via the official app or website, not from messages or emails, to avoid falling for phishing scams.
- Request a Security Code or Support from Instagram: If you no longer have access to the linked email or phone number, request a security code sent to your original recovery contact. Instagram often prioritizes recovery requests submitted from previously used devices or IPs. If that’s unavailable, Instagram has an option for additional support via their Help Center. To improve your chances of recovery, submit the request from a device or location you’ve used to access Instagram before because the platform often gives higher priority to familiar login environments.
- Report the Account as Hacked to Instagram: If you can’t get back in, report your account as hacked to Instagram through the Help Center.
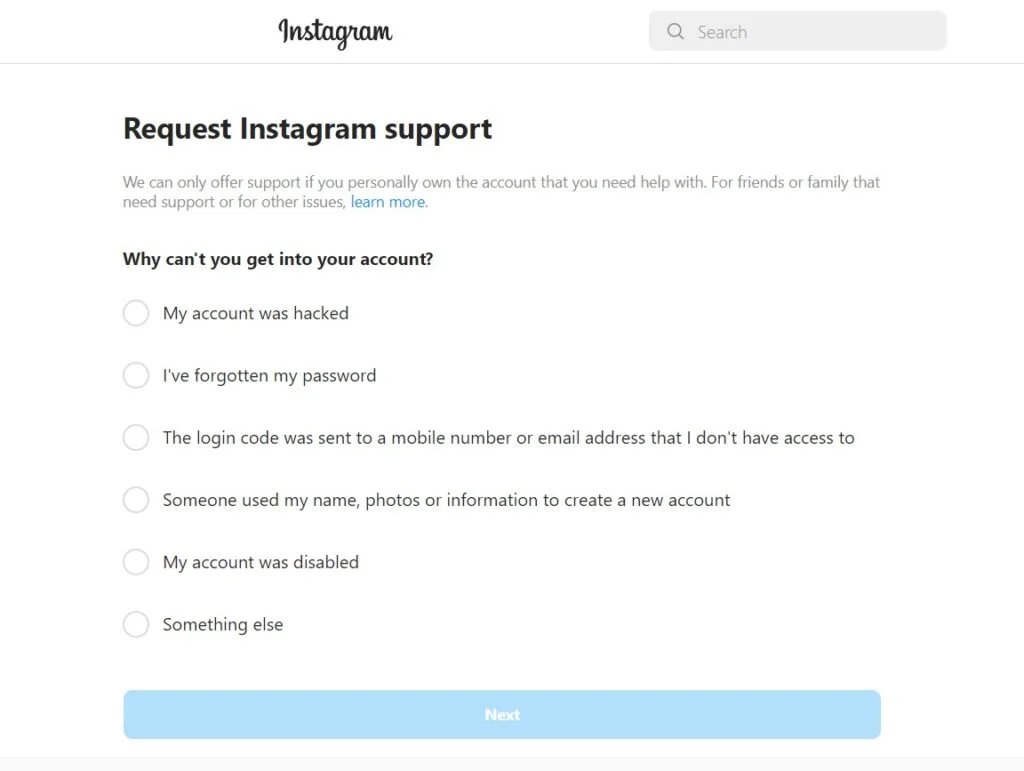
Instagram offers an option to let them know your account was compromised, and they’ll guide you through the recovery process.
- Reclaim Access Using a Verified Device: Instagram may ask you to reclaim access using a device you’ve previously logged in to. If you have access to any trusted device, use it to reset your password or receive the verification code.
- Verify Identity: If Instagram suspects the account was hacked, they may ask you to verify your identity by submitting a photo of yourself or providing additional details. This is usually done to ensure that the account belongs to you.
- Change Instagram Password: Once you’ve regained access, change your password to something strong and unique. Avoid reusing passwords from other accounts. Enable two-factor authentication for an extra layer of protection.
How to Recover a Hacked Instagram Account If I Can't Log In
If you’re unable to log in to your Instagram account after it’s been hacked, don’t worry. There are steps you can take to recover it. Follow the instructions below to regain control of your account:
Submit an Identity Verification Request
If you’re locked out, Instagram will often ask for proof that you are the account owner. You’ll need to submit an identity verification request, which may involve a photo of you holding a code provided by Instagram. This helps Instagram confirm that it’s truly your account.
Follow Instagram’s Video Selfie Verification

For further security, Instagram may request that you complete a video selfie. This process involves recording a short video of yourself, which helps Instagram compare your face with the one on your account’s profile picture. It's a way to prove your identity if you can't access your recovery email or phone number.
Wait Times and Follow-Up Tips
The recovery process can take time, so it’s important to understand what to expect and how long to potentially wait. Instagram support may take anywhere from 24 hours to several days to review your case. If you’ve provided identity documentation, like a government ID, it could take 3-7 business days to receive a response.
During this waiting period, it’s very important to avoid taking any unnecessary actions that could delay your recovery. Do not submit multiple recovery requests, as this can trigger spam detection and push your case further down the queue. Instead, allow at least 48 to 72 hours for Instagram to respond before trying again. Use this time to regularly check your inbox (including the spam or junk folder) for any updates from their support team.
It's also important to be cautious about third-party services that promise to speed up the recovery process. Many of these services are scams, and using them can jeopardize your security further. If you haven’t received a response from Instagram after 7 days, you can submit a new recovery request or follow up on the original ticket. When doing so, make sure to attach any additional evidence you have, like screenshots or emails, to help Instagram process your request faster.
How Hackers Typically Access Instagram Accounts
Hackers use clever tricks and common vulnerabilities to gain control of Instagram accounts. Understanding these methods is the first step toward protecting yourself:
| Method | How It Works | What You Can Do |
|---|---|---|
| Phishing Emails and Fake Login Pages | You get an email or message pretending to be from Instagram, often under the pretense of a copyright violation or some urgent account issue. The page may look real but can steal your login info. | Always check the sender's email and the website URL. Guardio blocks fake login pages and warns you in real-time. |
| Malicious Browser Extensions or Apps | Some apps or extensions ask for access to your Instagram account, then misuse it in the background. | Only install tools from trusted sources. Remove anything that feels shady or unnecessary. |
| Leaked Credentials from Past Breaches | Hackers use stolen usernames and passwords from other sites to try logging into Instagram. | Use a unique password for Instagram. Guardio alerts you if your info is found in a data leak. |
| Public Wi-Fi and Unsecured Networks | On open Wi-Fi, hackers can intercept data if the connection isn’t encrypted properly. | Avoid logging in on public Wi-Fi. If you must, use a VPN to secure your connection. |
Scammers often prey on fear. A fake email saying you've violated Instagram's copyright rules may prompt you to panic-click a login link.

These phishing emails look legit, but direct you to fake pages that can steal your password. Guardio blocks these before they even reach you.
How to Secure My Instagram Account after Recovery
Once you recover your account, taking the right steps can help you avoid another hack. Here’s what to do next:
- Enable Two-Factor Authentication (2FA): Turn on 2FA in your Instagram settings. It adds an extra step to logins by sending a code to your phone or authentication app, even if someone has your password.

- Use a Strong, Unique Password: Choose a password that’s long, random, and not used anywhere else. Avoid names, birthdays, or common words. Use a password manager if needed.
- Regularly Review Linked Devices and Apps: Check your login activity in Instagram settings and remove any devices you don’t recognize. Also, go through third-party apps linked to your account and revoke access to anything suspicious.
- Avoid Clicking Suspicious DMs or Emails: Be careful with links sent through messages or emails. Hackers often impersonate Instagram or your friends to trick you into clicking phishing links.
{{component-tips}}

What to Do If My Personal Information Was Compromised
If your Instagram account was hacked, there’s a chance the attacker also got access to personal information like your email, phone number, or reused passwords. Acting fast can help you prevent more serious problems like identity theft or further account takeovers.
Check for Reuse of Passwords on Other Platforms
If you’ve used the same password on other apps or websites, those accounts might be at risk too.
Go through your important accounts (like email, banking, or shopping sites) and change any reused passwords. Use strong, unique ones, ideally with a password manager, so you don’t have to remember them all.
Monitor Your Email and Social Media for Unusual Activity
Hackers often try to dig deeper after getting access to one account. Watch for login alerts, password reset emails you didn’t request, or messages sent from your social accounts that you didn’t write. If anything seems off, act quickly: update passwords, enable two-factor authentication, and check for unfamiliar devices.
Consider Identity Theft Protection Tools
Protecting your personal information before it gets misused is just as important as recovering it. If your name, email, or phone number has been exposed, it’s wise to use tools that actively guard against future threats, and not just respond after damage is done.
Tools such as Guardio can help stop attacks before they happen. It blocks fake Instagram login pages (phishing sites), flags scam links sent through DMs or emails, and alerts you when your info appears in a data leak. On iOS, it can even filter scammy SMS messages that pretend to be from Instagram or Meta, stopping them before they even hit your inbox.
These tools act like a digital bodyguard, quietly working in the background to keep you and your accounts safe.
Set Up Guardio Alerts for Future Threats
Guardio’s Critical Security Alerts provide real-time notifications to detect and prevent financial scams, ensuring immediate intervention when suspicious activities are detected. These alerts are particularly useful when immediate threats, such as phishing attacks or unauthorized access attempts, are detected in real-time.
Here’s how to turn it on:
1. Go to Your Guardio Dashboard: Log in to your Guardio account and head to your main dashboard. You’ll see a setup checklist to guide you through important features.
2. Find “Critical Security Alerts”: Click the drop-down menu next to the checklist, then look for the option labeled “Critical Security Alerts.”

3. Click “Set Up” and Follow the Prompts: Press the “Set Up” button and complete the simple steps shown. You’ll be asked to add your phone number for instant voice alerts.
4. Verify with a Test Call: Guardio will place a quick test call to make sure everything is working properly.
5. Save Guardio as a Contact on Your Phone: Add Guardio to your contacts so when a real alert comes in, you know it’s legit and not just another spam call.
How Guardio Can Help Prevent My Instagram from Getting Hacked Again
Guardio works quietly in the background to keep your digital life safer, especially from the types of tricks hackers use to break into accounts like Instagram.
- Real-Time Phishing Protection in Your Browser
Guardio instantly detects and blocks fake login pages pretending to be Instagram or Meta. These phishing sites often look almost identical to the real thing, tricking users into typing their username and password. Guardio warns you before you even land on the page, keeping your account and info safe. - Alerts for Leaked Credentials and Data Breaches
If your email, username, or password shows up in a data leak, Guardio lets you know right away. You’ll get alerts when your personal information appears in known breaches so you can take action fast by changing your login details before hackers use them. - Blocking Malicious Websites Before You Click
Hackers often send scam links through Instagram DMs or emails. Guardio checks links before you open them. If the website is dangerous or linked to malware, phishing, or fake giveaways, Guardio blocks the page and explains why, helping you avoid falling into such traps. - Scanning for Risky Extensions or Add-ons
Some malicious browser extensions can hijack your Instagram account or steal your data silently. Guardio scans your browser on the desktop for harmful add-ons and helps you remove them before they cause damage. If you primarily access Instagram from a desktop browser, it’s worth running a scan regularly to stay protected. - Fixing Weak Spots in Your Digital Security
Guardio identifies vulnerabilities in your digital footprint, like weak or reused passwords, or accounts without two-factor authentication. It gives you clear, actionable steps to strengthen these areas so you’re not just reacting to threats, but actively staying ahead of them.
Conclusion
Getting your Instagram account hacked can feel overwhelming, but knowing what to look for, how to respond quickly, and how to protect your information can make all the difference. Whether it’s spotting unusual activity, recovering your account, or locking things down afterward, every step counts.
Tools like Guardio play a key role in staying one step ahead of hackers. By blocking phishing pages, warning you about leaked credentials, and scanning for threats in real time, Guardio helps you prevent the problem before it even starts. Read the latest 2025 Guardio review to know more.
Combining Guardio with good online practices like enabling two-factor authentication, using strong passwords, and avoiding suspicious links gives you the best chance at keeping your Instagram (and other accounts) safe in the long run.
{{component-cta-custom}}FAQs
What should I do first if my Instagram was taken over?
Try Instagram account recovery right away and secure the email account tied to Instagram. If you can sign in, change your password and enable two-factor authentication immediately.
What if someone changed my Instagram email or phone number?
Use Instagram recovery options and look for the security email that alerts you about the change. You may be able to reverse it from that message. If not, follow the in-app verification steps to prove ownership.
How can I reduce the chance it happens again?
Use a strong unique password, enable two-factor authentication, and remove any third-party apps you do not trust. Be cautious with links in DMs and emails that ask you to log in.
What should I do first after I regain access?
Change your password, enable two-step verification, review active sessions, and remove unknown connected apps.
How do account takeovers usually happen?
Common causes include phishing links, reused passwords from older breaches, and risky extensions or apps that capture logins.
Should I contact support right away?
If you cannot regain access quickly, contact support through the official help center. Avoid support links from messages.








