It’s ‘Ez-Peasy’ for Scammers: E-ZPass Tops Q2 2025’s Most Imitated Brands in Phishing Scams

Key Takeaways
Scammers are ramping up impersonation tactics using the brands people trust the most.
In Q2 2025, phishing scams continued to grow in scale and creativity. From fake toll violations to cleverly disguised login alerts, scammers are constantly adapting, and AI is now accelerating how quickly and convincingly they can do it.
What’s changed this quarter? The most impersonated brand isn’t a tech giant. It’s E-ZPass, a regional toll service.
This signals a shift in how cybercriminals are operating. They’re leaning into urgency and routine, using familiar-looking messages to pressure people into quick action, now generated and scaled more efficiently thanks to AI. At the same time, big names like Microsoft, Steam, and Facebook remain top targets, especially in credential theft and account takeovers.
Let’s take a look at the most-imitated brands this quarter and the latest phishing tactics making the rounds.
{{component-cta-custom}}
The Top 10 Most-Impersonated Brands in Q2 2025
- E-ZPass
- Microsoft
- Steam
- Facebook
- Roblox
- Coinbase
- Netflix
- American Express
- Telegram
- Australian Government
New entries this quarter include Coinbase, American Express, Telegram, and the Australian Government.
Why These Brands Are Being Targeted
This quarter’s top three impersonated brands, E-ZPass, Microsoft, and Steam, reflect a growing trend in scam design. Scammers are combining urgency, emotional pressure, and trust to get people to act without thinking.
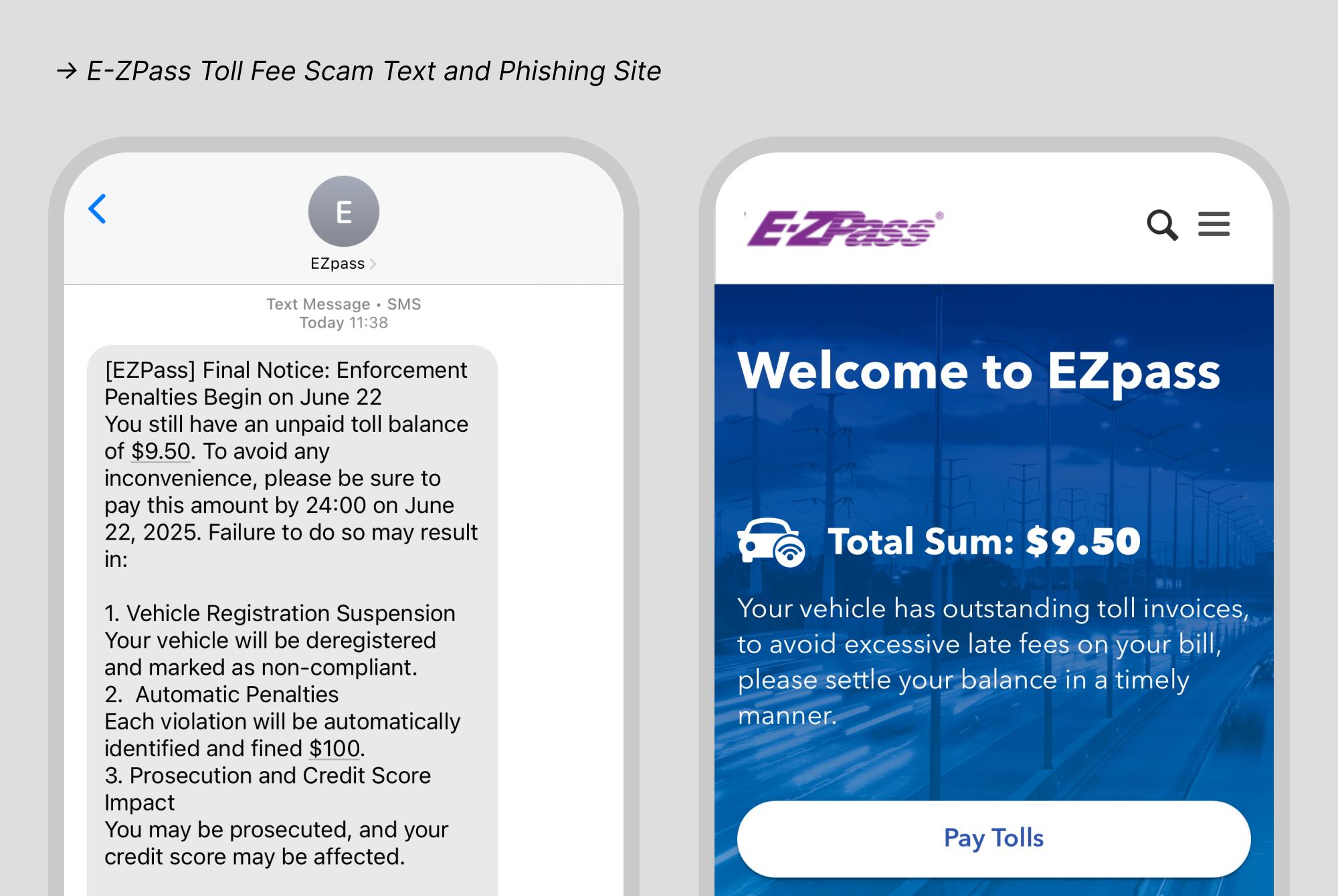
- E-ZPass: Phishing scams impersonating E-ZPass typically claim the recipient missed a toll payment or owes a fine. These messages often include state-specific branding and URLs that closely resemble real toll agency websites. With the help of AI, scammers are able to generate localized versions of these messages across different U.S. states, making them feel official and relevant to each recipient.
Because toll payments are common and often automated, recipients are likely to believe the notice is legitimate and act quickly to avoid penalties. The simplicity and routine nature of the message, paired with a sense of urgency, make this scam especially effective.
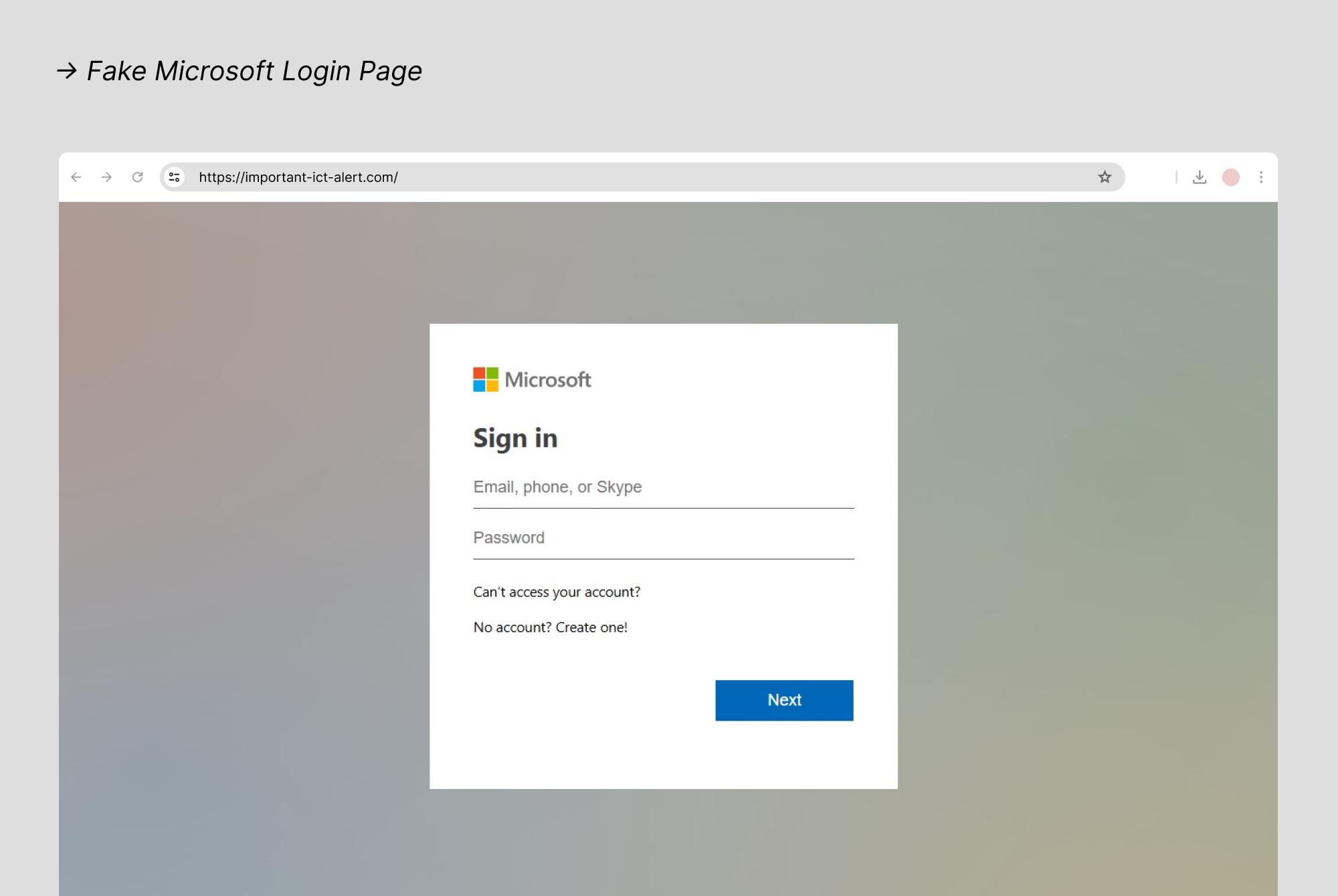
- Microsoft: Microsoft remains one of the most impersonated brands globally, especially in credential theft campaigns. Scammers send emails that look like legitimate security alerts, such as login attempts from unknown devices or password reset prompts. These emails often mimic Microsoft’s branding with precision.
Once a user clicks the link and enters their credentials, attackers can gain access to Outlook, OneDrive, Teams, and even enterprise accounts, unlocking a wide range of personal and professional data. Given how deeply integrated Microsoft accounts are into people’s daily lives, they’re a high-value target.
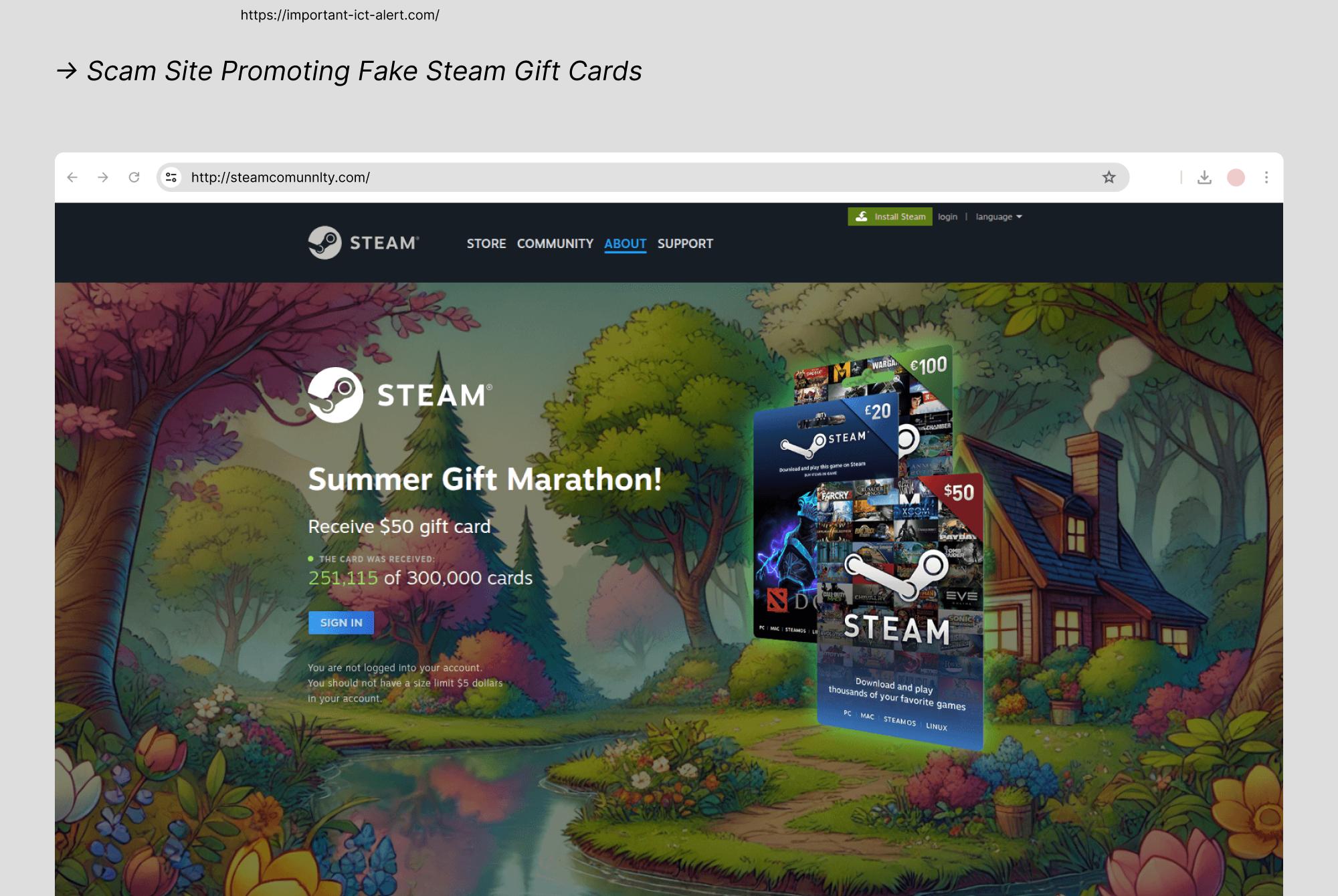
- Steam: Popular with younger users, Steam has become a frequent target for phishing scams that play on urgency and excitement. Attackers often pose as bots, friends, or giveaway accounts, offering free games, discount codes, or trade offers that require immediate action. These messages feel casual and legitimate, especially when they come through gaming forums or chat apps like Discord.
Victims are directed to fake login pages that closely mimic Steam’s interface. Once credentials are entered, scammers can steal access to game libraries, virtual assets, and even linked payment methods. The emotional nature of these scamswhether it’s fear of missing out or reacting quickly to a “support issue”makes them highly effective.
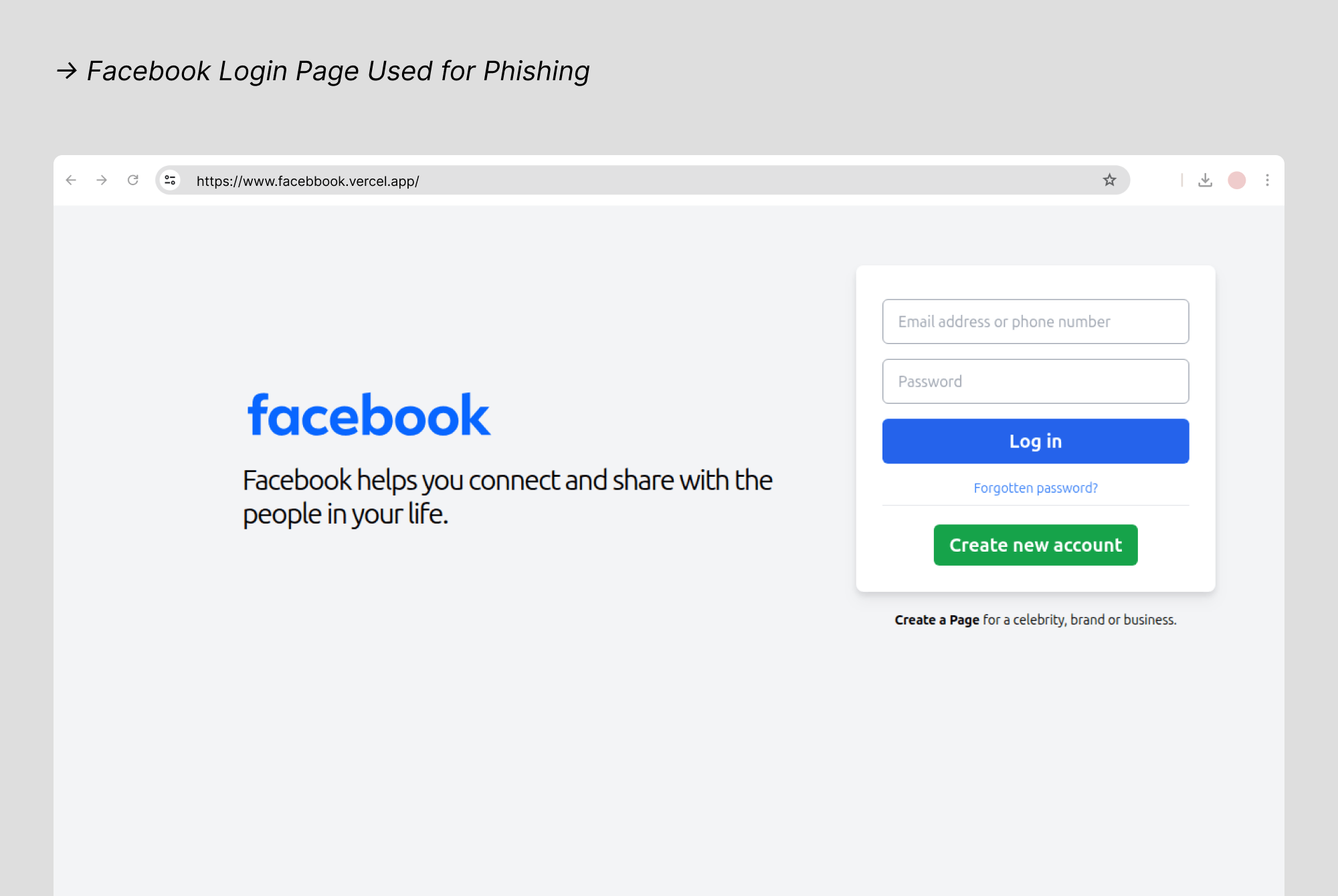
- Facebook: Still one of the most impersonated platforms, Facebook is commonly spoofed in phishing attacks that claim an account has been reported, locked, or flagged for suspicious activity. These messages often include links to fake “appeal” or “recovery” pages, prompting users to log in.
Once credentials are captured, scammers can take over the account and use it to message friends, join groups, or post misleading content. Many scams continue through Messenger or Facebook Marketplace, where trust plays a key role. Because Facebook is deeply personal for many users, fear of losing access leads people to act fast, exactly what attackers rely on.
Scam Trends on the Rise in Q2
DMV and Toll Fee Scams
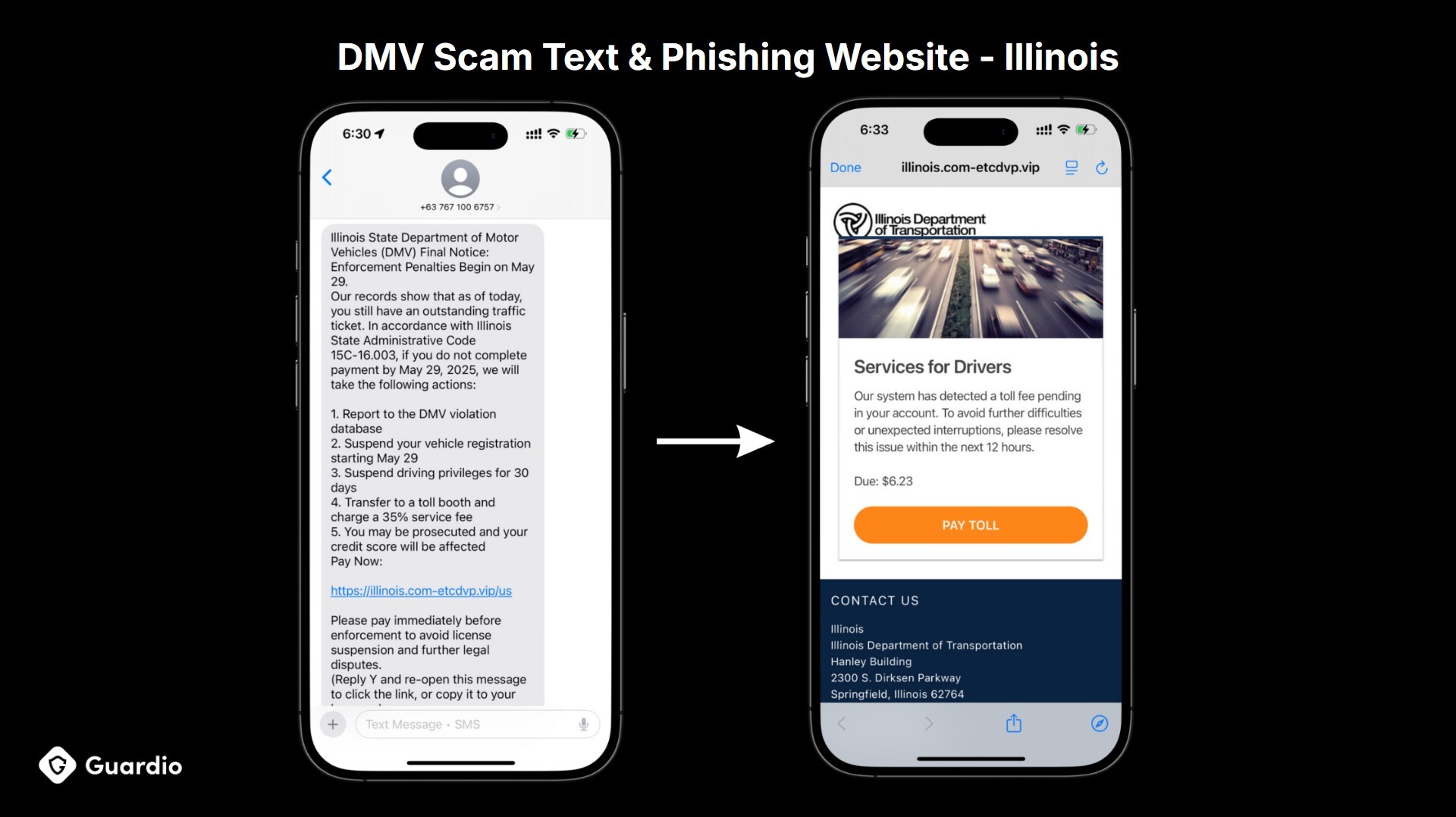
Toll and DMV scams exploded this quarter. Guardio tracked a 773% increase in scam texts impersonating toll services across the U.S., with nearly every state being individually targeted. Scammers used AI to quickly generate localized versions of these messages, adjusting names, links, and language to match each state’s official toll agency or DMV.
These scams feel routine and plausible. If you’ve ever driven through a toll and weren’t sure if you were charged, the message hits just the right nerve. Victims are urged to pay immediately, and the links lead to phishing sites designed to look nearly identical to real government portals.
Even the FBI issued a public warning, advising people to delete these messages on sight. The sophistication of the fake websites and the hyper-local personalization make this one of the most convincing phishing formats seen this year.
Tariff Relief Scams
Another trend is the rise of tariff or government subsidy scams. These messages promise financial relief or rebates in exchange for a “processing fee.” Often disguised as official notices, these scams take advantage of economic uncertainty. They aim to create just enough hope and urgency to get people to enter payment details or personal information.
Guardio identified dozens of phishing domains mimicking government and financial assistance programs tied to trade or tariff-related aid.
The 16 Billion Password Leak
A massive leak uncovered this quarter included over 16 billion stolen credentials. The source? Not one big new breach, but rather an accumulation of data from infostealer malware and years of credential theft.
This isn’t about one company being hacked. It’s about malware that silently collects your login info, passwords, and other personal data while you browse. Once stolen, this data gets shared, sold, and reused across the cybercrime world.
Even if you weren’t directly affected, this is a good reminder to take action. If your passwords haven’t changed in a while, they may already be floating around underground. Reusing passwords across accounts only makes things worse.
What You Can Do
Phishing scams are evolving fast, but staying ahead is possible. Here’s what security experts recommend:
- Be cautious with urgent messages. Don’t click links in texts or emails without verifying the sender.
- Check the source. When in doubt, visit the official site directly instead of using links from messages.
- Use strong, unique passwords. Consider a password manager to make this easier.
- Turn on multi-factor authentication. This adds an extra layer of security even if your password gets stolen.
Install a protective tool like Guardio. It can help detect phishing attempts, block malicious websites, and keep your personal info safe.
Final Thoughts
Phishing is no longer limited to sketchy emails. It now includes convincing texts, realistic websites, and scams that feel like everyday tasks. Whether it's a toll fee reminder, a fake Steam code, or a security alert from Microsoft, scammers are getting better at pretending to be the brands you trust.
The good news? You can stay ahead by staying alert. Recognize the signs, protect your accounts, and take action when something feels off.
If you're curious whether your info was exposed in recent breaches or want to learn more about phishing trends, Guardio can help.
Stay safe out there.
.png)
{{component-cta-custom}}








