Is Opera Browser Safe? Key Risks, Features & Best Practices

Key Takeaways
- Opera is Generally Safe But Not the Most Private: It’s fine for everyday browsing, but its privacy settings, data collection, and slower updates make it less ideal for handling sensitive info.
- Its Built-in VPN Isn’t Really a VPN: Opera’s VPN is actually a proxy and doesn’t fully protect your data or hide your identity like a real VPN would.
- Security Updates Come Late: Opera lags behind Chrome in patching known vulnerabilities, which could leave you exposed for days or even weeks.
- Malicious Extensions Are a Real Risk: Since Opera uses Chrome extensions, harmful add-ons can sneak in if you’re not careful about what you install.
- Guardio Adds an Extra Safety Net: Guardio offers proactive, cross-device protection against phishing, malicious sites, and harmful extensions. While it can be added to Opera via the Chrome Web Store, it’s not officially supported there. For full protection and best performance, Guardio is best experienced on Chrome and other fully supported browsers.
Opera has always stood out with its slick interface, free VPN, and built-in ad blocker. But when it comes to safety, the answer is mixed. Opera is generally safe for casual browsing, offering decent protection through its Chromium base, tracker blocking, and phishing warnings.
However, it falls short in privacy and update speed compared to browsers like Chrome or Firefox. Its free VPN isn’t a true VPN but a proxy, and delayed security patches can leave brief windows of vulnerability.
In short, Opera is secure enough for everyday use, but not ideal if you handle sensitive data or value complete privacy. Let’s explore Opera’s privacy posture, built-in protections, and the hidden risks users should be aware of.
{{component-cta-custom}}
Is Opera Browser Safe?
Opera is moderately safe for everyday browsing, offering a decent balance between performance, convenience, and built-in security. It provides ad and tracker blocking out of the box, and its Chromium foundation ensures compatibility with most modern web standards. However, Opera’s privacy protections and patch cadence lag slightly behind industry leaders like Chrome and Firefox.
While it’s generally fine for personal use like streaming, casual shopping, or news reading, Opera may not be ideal for users who deal with confidential data, work logins, or financial dashboards. Its free VPN, though appealing, doesn’t provide the same encryption and anonymity as dedicated VPN services.
That said, Opera’s lightweight design and feature-rich layout make it a good secondary browser when configured securely.
Opera vs Chrome vs Firefox
Here’s how Opera stacks up against Chrome and Firefox in terms of security, privacy, and extension reliability:
| Feature / Browser | Opera | Chrome | Firefox |
|---|---|---|---|
| Security Base | Chromium engine | Chromium engine | Gecko engine |
| Update Frequency | Delayed after Chromium patches | Immediate (Google-led) | Frequent, independent |
| Built-in VPN | Yes (proxy-based) | No | No |
| Tracker/Ad Blocker | Yes | Limited | Yes |
| Extension Safety | Medium (from Chrome Web Store) | High (Google oversight) | High (manual review) |
| Privacy Policy Transparency | Moderate | Low | High |
| Guardio Support | Partial (via Chrome Web Store) | Full | Partial (limited) |
Opera is a capable browser for casual users who want convenience and speed, as long as they remain cautious with extensions and keep auto-updates enabled.
Why Opera’s Security and Privacy Matter
Modern browsers aren’t just for web surfing. From logging into work dashboards to managing bank accounts, everything you do online flows through your browser. That’s why even small privacy gaps or outdated patches can have major consequences.
Opera, despite its sleek design and useful built-in tools, can become a weak link if its default settings remain unchanged or if users trust its VPN too much. Because it’s built on Chromium but maintained separately, it doesn’t always get the same security updates or vulnerability patches as Chrome.
Weak Settings Enable Session Hijacking and Token Theft
Opera’s convenience features, like syncing sessions across devices and staying logged in can backfire, if not properly secured. If you keep multiple sessions open or reuse login tokens between devices, attackers can exploit these tokens through malicious extensions, network sniffing, or injected scripts to hijack active sessions.
Unlike Chrome, Opera doesn’t frequently expire tokens or enforce strict re-authentication, increasing the risk of unauthorized access to workspaces or social accounts.
Compromised Browsing Exposes Autofill, Sync, and Payment Data
Once an attacker gains a foothold, whether via a malicious extension, phishing site, or a zero-day vulnerability, Opera’s integrated storage can become a goldmine. Because Opera stores autofill data, synced passwords, and even saved card details locally or in the cloud, a single compromise may expose sensitive credentials or financial data.
Recently, Guardio Labs discovered a critical zero-day vulnerability in Opera browsers that allowed remote attackers to execute files on a user’s computer and could lead to complete system takeover. This risk escalates if “Auto-sign-in” or “One-click login” is turned on globally, letting attackers harvest stored data without triggering fresh authentication prompts.
🚨 Zero-Day Vulnerability in Opera Browsers:
Guardio (@GuardioSecurity) January 15, 2024
Guardio Labs discovered a major vulnerability in Opera Browser, allowing attackers to execute files on users’ computers leading to a complete system takeover! https://t.co/LuC4OmxPkK
What Chromium CVEs and Patch Cadence Mean for Opera Users
Opera’s security relies on the Chromium engine, which is continuously updated by Google. However, Opera’s integration and release cycle are not in sync with Chrome’s. When a new Chromium vulnerability (CVE) is patched by Google, it can take days or weeks before that same fix lands in Opera.
During this lag, hackers who monitor CVE disclosures can weaponize known vulnerabilities and target browsers that haven’t yet updated. These are known as n-day exploit attacks, which are publicly known but have unpatched flaws.
Thanks to the @Opera_Security team for their rapid and collaborative response in addressing this vulnerability! https://t.co/z3GWOgthzp
Guardio (@GuardioSecurity) January 16, 2024
Guardio’s research helped expose and mitigate the issue before widespread exploitation, underscoring the importance of timely patching and proactive browser protection.
Opera Browser Security Overview
Opera comes packed with handy security features out of the box, but it’s important to understand both its strengths and limitations to stay protected.
- Built-In Ad and Tracker Blocking: Blocks common ads and trackers by default, improving speed and reducing exposure, though advanced fingerprinting can still bypass it.
- Free VPN Features and Limitations: Encrypts only browser traffic and isn’t zero-log; Opera may retain limited usage data for diagnostics.
- Security Updates and Patch Management: Updates regularly but lags behind Chromium patches, leaving a small window for vulnerabilities.
- Phishing and Malware Protection: Uses browser security tools
- Extension Safety and Potential Risks: Chrome extensions can gain broad permissions; only install trusted sources and review access carefully.
Is Opera a Privacy-Friendly Browser?
Opera markets itself as a browser with privacy in mind, especially highlighting its built-in VPN and tracker-blocking features.
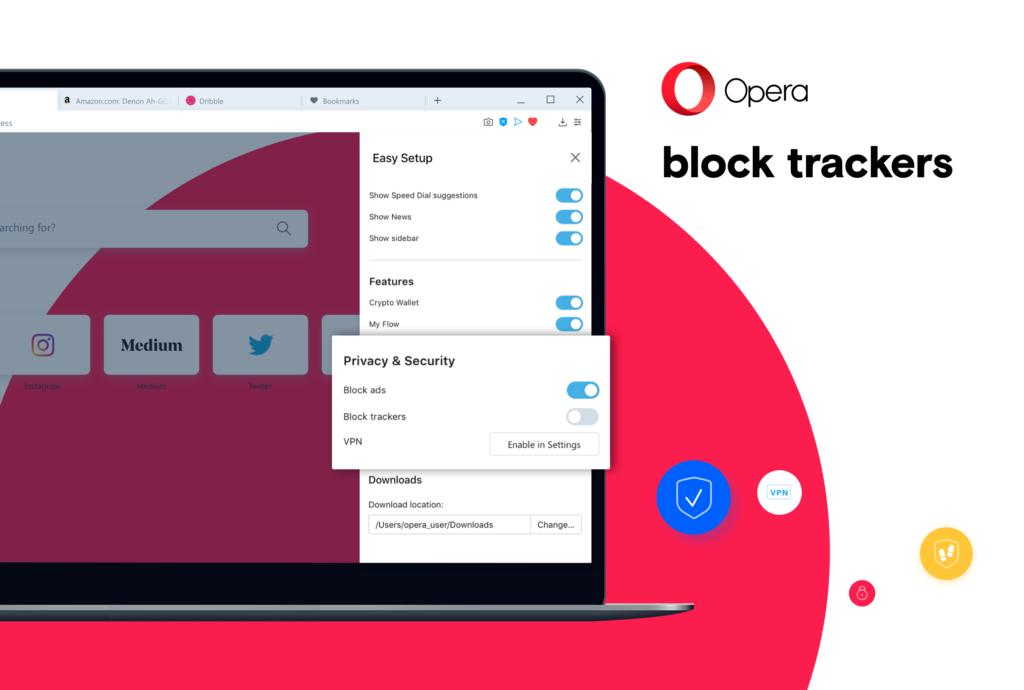
While it does offer some privacy protections, a closer look reveals limitations in data handling, logging practices, and past controversies that every user should consider before trusting Opera with sensitive browsing.
Logging and Data Collection Policies
Opera collects certain types of data by default. This includes:
- Usage statistics and crash reports to improve browser performance.
- Browsing habits and search queries in anonymized form for analytics and product improvements.
- VPN connection metadata, even though Opera advertises a “free VPN,” it’s more of a proxy, and some usage logs may still be retained.
Unlike browsers like Firefox, which emphasize minimal telemetry and zero-knowledge logging, Opera’s data collection is moderate but not zero. This means that while casual browsing is reasonably safe, privacy-conscious users may still want to limit sync features or consider additional privacy tools.
Handling of User Data
Opera stores some personal data, particularly when you use features like:
- Opera account sync (bookmarks, passwords, and autofill data)
- Saved credit cards and payment info
- Browsing preferences and extension settings
While Opera encrypts some of this data in transit, it is not fully end-to-end encrypted like Firefox Sync. That means, theoretically, if Opera servers or an attacker gain access to the sync system, some personal data could be exposed. Users should treat Opera as more convenient than fully private, and avoid syncing sensitive credentials if maximum privacy is needed.
Past Privacy Concerns and Reports
Opera has faced multiple privacy discussions and concerns in the past. For instance, the 2016 Acquisition by a Chinese consortium raised eyebrows about potential cross-border data routing and occasional data sharing with third-party analytics services for improving features, which drew criticism from privacy advocates.
While no major breaches have been publicly disclosed, these points indicate that Opera is not designed for users who need strict anonymity or want full control over every piece of data leaving their device.
Opera VPN: Safe or It’s a Marketing Gimmick?
Opera’s “VPN” is technically a secure proxy, not a true VPN. It routes browser traffic through Opera servers but doesn’t encrypt DNS or app traffic. It’s suitable for bypassing regional restrictions, not for anonymity or securing public Wi-Fi connections.
Opera Safety: Risks and Warning Signs
While Opera is convenient and feature-rich, it’s not immune to security risks. Malicious extensions, fake VPNs, or compromised settings can quietly compromise your browsing experience, steal sensitive data, or even hijack system resources. Recognizing the warning signs early can help you stay one step ahead of attackers and protect your personal and financial information.
- Malicious Extensions and Plugins: Fake or cloned add-ons from the Chrome Web Store may steal tokens or inject ads.
- Fake VPN and Proxy Risks: Third-party Opera “enhancers” often redirect through data-harvesting proxies.
- Phishing and Redirects: Compromised search settings can lead to fake login portals.
- Malware or Suspicious Activity: Unexpected CPU spikes or background connections can signal a hijack.
- Performance Anomalies: Frequent tab crashes or home page resets are signs of malicious extensions.
How to Tell If Opera is Compromised
Even with built-in protection, Opera can fall prey to silent takeovers where malicious scripts, extensions, or hijacked policies quietly alter your browsing behavior. Recognizing early signs of compromise helps you prevent data theft, phishing exposure, or unwanted background tracking. Here’s what to look for:
Homepage/Search Hijacks
If your start page or default search engine suddenly changes without permission, it’s a red flag. Many hijackers replace search settings with fake engines that log queries, inject ads, or redirect to phishing sites.
Unwanted Notifications and Redirects
Frequent popups, fake “system alerts,” or redirects to giveaway or “update” pages usually signal injected scripts or rogue extensions.
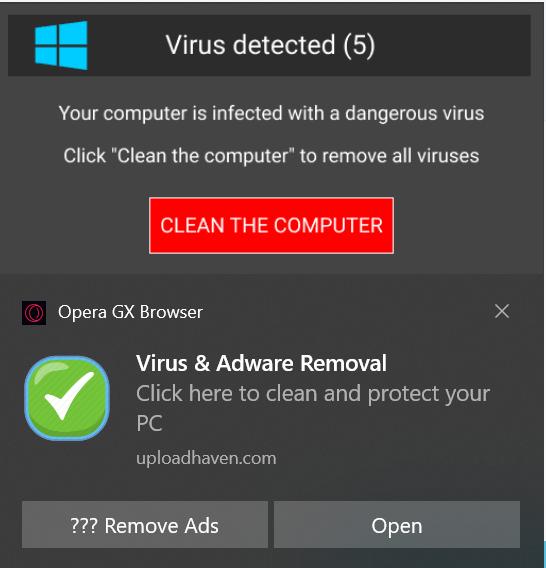
These pages often attempt to harvest login tokens or lure users into downloading malware.
Unknown Extensions, Profiles, or Policies
Visit installed extensions and if you spot unfamiliar add-ons, force-installed settings, or new profiles, your browser may be compromised. Remove anything suspicious immediately and reset your configuration.
{{component-tips}}
Best Practices for Safe Browsing with Opera
Following best practices can help you maximize privacy, minimize exposure to malware, and keep sensitive data safe. From adjusting settings to monitoring extensions, these strategies ensure you get the most secure browsing experience without sacrificing speed or functionality.
| Action | Why It Matters |
|---|---|
| Adjust Privacy Settings | Disable data collection, autofill, and unnecessary sync options. |
| Use Trusted Extensions Only | Stick to verified Chrome Web Store sources; avoid unknown scripts. |
| Clear Browsing Data Regularly | Removes old cookies and cached tokens that could be stolen. |
| Enable Anti-Phishing and Anti-Malware Tools | Adds another defense layer against fake sites and payloads. |
| Use Comprehensive Protection Tools | Use a trusted security platform like Guardio for proactive detection of phishing, malicious extensions, and leaked credentials. For full protection, Guardio is best experienced on Chrome. |
How Guardio Strengthens Opera Browser Security
While Opera offers built-in privacy tools, it still benefits from an added layer of proactive protection. Guardio provides real-time, cross-device defense against phishing pages, malicious extensions, and data leaks, helping users stay protected even when browser safeguards fall short.
And while Guardio can be added to Opera via the Chrome Web Store, it is not an officially supported browser. For the best protection, full functionality, and seamless synchronization across devices, Guardio is optimized for Chrome and other fully supported browsers. Here’s how Guardio enhances your overall security posture:
- Real-Time Threat Prevention: Detects and blocks phishing attempts, malicious redirects, and credential-stealing pages before they load.
- Extension and App Risk Control: Identifies and neutralizes harmful extensions or unauthorized integrations that can alter settings or capture sensitive data.
- Data Breach Monitoring and Alerts: Notifies you instantly when your email or credentials appear in exposed databases.
- Proactive Defense Beyond Built-In Tools: Offers deeper, continuous scanning and contextual risk analysis that go beyond Opera’s native protections.
- Cross-Device Safety: Guardio’s mobile app (for Android and iOS) and Chrome experience deliver unified visibility and real-time alerts, ensuring security whether you’re browsing, logging in, or shopping online.
Conclusion
Opera is a feature-rich browser with decent built-in security, but its privacy model and delayed patching make it a mid-tier choice for safety. For users handling sensitive data, it’s better to rely on browsers with faster updates and tighter ecosystem controls.
Tools like Guardio can bridge Opera’s security gaps, especially when used on fully supported platforms like Chrome, helping you browse with confidence, block harmful sites, and stay protected from real-time threats.
{{component-cta-custom}}
FAQs
How can non-tech users make Opera safer right away?
Opera is usable out of the box, but a few quick tweaks can seriously upgrade your safety.
- Turn off auto-sign-in and sync to limit token theft and session hijacks.
- Use a throwaway profile for sketchy sites, downloads, or extensions.
- Avoid Opera’s VPN for privacy tasks—it’s just a proxy, not full encryption.
- Clear cookies and tokens weekly to wipe session footprints.
Get help adjusting these settings in Guardio’s browser protection glossary.
How can I tell if an Opera extension is malicious?
Suspicious extensions often hide in plain sight. Trust your instincts—and your tools.
- Check extension reviews and permissions before installation.
- Use Guardio to scan for risky extensions, even those installed in the past.
- Watch for sudden homepage or search engine changes—a common red flag.
- Audit your browser regularly for new or unrecognized plug-ins.
Learn how Guardio handles extension threats.
Can fake VPNs in Opera trick me into sharing data?
Yes, many third-party VPN add-ons and even Opera's built-in proxy expose more than they protect.
- Avoid browser VPNs that don’t encrypt all traffic, especially DNS.
- Beware of VPN extensions with few reviews or vague privacy policies.
- Never input credentials while using an unknown VPN—you could be handing them to scammers.
- Use real VPN software for public Wi-Fi, not browser gimmicks.
Read Guardio’s take on VPN scams and risks.
Is Guardio fully compatible with Opera?
Not fully. While Guardio can be installed via the Chrome Web Store, it works best elsewhere.
- Expect limited functionality on Opera, including real-time alerts and dashboard syncing.
- For full protection, install Guardio on Chrome where performance is optimized.
- Use Guardio’s mobile app for security across all devices and browsers.
- Avoid depending on Opera’s native tools alone—they don’t catch everything.
Check the list of supported browsers to get the best results.
What does Guardio do that Opera’s built-in security can’t?
Opera blocks ads and trackers, but Guardio adds real-time, AI-driven defense.
- Detects phishing pages before they load, not just known bad URLs.
- Neutralizes harmful extensions immediately, not after damage is done.
- Alerts you to data leaks or stolen credentials, even if Opera misses them.
- Works across devices, protecting your browser, email, and even texts.
Explore the full Guardio security feature set.
What is the fastest safe first step for Is Opera Browser Safe? Key Risks, Features & Best Practices?
Start by verifying the source using official channels (official website/app) rather than clicking message links. Then follow step-by-step checks.








