Oh RATs!
How Guardio found a way to detect the nastiest of scams


Nati Tal
Efrat Tabibi
July 6, 2022
•
13
min read
Guardio has uncovered a super-sophisticated, “long-con” scam, known as RATScam (Remote Access Tools), that exploits some very dangerous loopholes in corporate-grade software. These scams are brutally parasitic, in that they’re not one off, single attacks. They are sustained campaigns, designed to bleed victims dry of savings and assets. Adding to that, our data shows that 1 out of 5 remote access tools being downloaded are part of a scam! We’ll show you how these malicious RATs work, how scammers abuse the customization and free trials of those platforms, how we discovered them and especially how we use data and behavioural analysis to differ between the good, the bad and the really ugly…
Over the past few months, Guardio has been observing the rise of a very sophisticated, next-level campaign of scammers abusing legitimate remote control software to literally get into their victims’ computers and from there directly to their wallets. Scambaiter, one of our favorite online vigilantes, turned our attention to those malicious campaigns after he himself found and documented operations that rented offices, trained agents and created work procedures... these scams are serious enterprises!
RAT scams abuse corporate-grade software (usually without paying a cent) and employ a very high level of intelligence gathering to convince and scam even the most tech-savvy of victims. Once installed on your computer, a RAT (Remote Access Tool) is persistent, mostly undetectable, and bypasses almost all regular forms of protection. And in a show of supreme chutzpah, these scammers even manipulate this capability to bypass 2FA protection and take full control of PayPal and Bank accounts.
We all know that remote control software has become the go-to tool for IT support, and is used around the world. And yet, Guardio’s data shows that at least 1 out of 5 remote control installation files downloaded in the last month is being used for malicious activity!
It’s a rough market nowadays, even for the scammers. So they need to get more sophisticated to succeed or even just to survive. Scam operations are actually purposefully trying to push up CCR (Customer Conversion Rate), as well as ROI (Return On Invest). In other words, they’re behaving like regular, legit start-ups! Yep, just like any other cyber-tech startup out there.
So let’s talk business for a second. Scammers want to make a profit. They need to stay in business and for that they go after your personal information, financial details, and, at the end of the day, your money.
The Dark Market is, sadly, thriving. A full set of information (or “fullz,” as scammers like to call it) including your SSN, address, name and DOB is worth a few bucks; your credit card details would go for around 15$; login details to your Facebook account can reach up to 45$ and your PayPal account would fetch up to $200.

Let’s try and understand why and how something as complex as a RAT operation actually exists. You can visualize almost any regular scamming operation these days with this simple funnel:

The more victims that fall into this funnel, the more profit the scammers make. Pretty obvious. But any scam that operates according to the funnel above is, of course, usually a one-time, non-sustainable operation. In other words, there aren’t going to be any willing repeat customers, and our poor scammers are always investing time and effort in finding new victims. Let’s look at a simple Facebook login scam as an example of a one-time sting:

Scammers fire tons of emails like this to any email address they can get their hands on. Now, they can’t send too many in one go, or they’ll be blocked immediately due to basic volume protection. Less than 1% of the target audience actually accesses the fake login page, and even less go ahead and type in their details. With large enough traffic, this scam can be profitable and can reap 1000’s of hacked accounts. But it’s costly and non-sustainable. Thankfully, emails like these are being blocked way more often by spam protection, and web hosts are acting to remove malicious sites uploaded by threat actors once being tipped by security sources. It’s too little and usually too late, but it’s something at least.
So that’s the old funnel, for relatively old scams we all know and still can’t seem to stop… But like all good entrepreneurs, scammers are always innovative. They know there’s money to be made, and they will invest time and effort to get to it.
So they now realize that a better way to scam is to be in full control. No more one-off, large-scale high-exposure operations. They only need to successfully hook their selected victim one time, and then they become a horribly efficient parasite. Now it’s not just one Facebook account. They can take more and more, draining accounts entirely and ultimately stealing their victims’ online as well as real-life identity. One hit — huge success. They just need to identify the right victim and employ the right methods.
So now the scammer’s funnel is much more sustainable, and even looks like some perverse form of subscription model:

Remember we threw in some business terms — ROI and CCR? Well, this is exactly that in action!
But surely, getting your hands on such powerful, stealthy software that won’t be stopped by AVs and is hosted on online high-capacity servers is super expensive? Nope. It exists, it can be used for free, and anyone can sign up for it.
Corporate-Grade RMM (Remote Monitoring and Management) software is a huge market. you probably already know and have tried some of the bigger brands, like TeamViewer, ConnectWise, AnyDesk and so on. They are used everywhere, from helping-your-parents-fix-some-pc-problems to MSPs (Managed Services Providers), Corporates and even nationwide IT — all to give genuine tech support!
And now, resourceful scammers are abusing free-tiers and SaaS free trials to get everything they need for their operations. For access to an RMM service, you just need to provide any email account, and you’re good to go. No credit card, no real proof of identity. Just go ahead and abuse 14 days of corporate-grade systems with premium service and hosting, and endless customization options for your very own RAT. All free of charge!

Once you get your small sized (< 3Mb) RAT installed on your victims' computers, you can perform magic. Some of the stuff a bad actor can get up to includes:
These are just the basics. Scammers are nothing if not inventive, and we have seen some truly horrible abuses of RAT capabilities out in the wild while analyzing these recent attack sprees.
Here at Guardio, we get millions of pieces of real-time data every day, teaching us how real people use the internet around the world. With this endless stream of data we were able to spot these malicious campaigns, and crucially, understand how threat actors work, abuse, and profit. By analyzing historical, anonymized data of numerous RAT scam attacks, past and present, we can clearly start to see patterns forming, and understand the threat actors’ operations and the tools being used. Here’s how these attacks usually go over time, as observed out in the wild:

It all begins with reconnaissance — collecting intelligence on relevant victims. Those actors are analyzing data leaks (e.g. the latest leak from MGM) or using their own malicious campaigns targeting victims with fake surveys to collect emails, names, phone numbers and tons of other data to be used later on.
As for the bait part, there are many ways to leverage the data they have on victims — the most powerful being the ability to actively block victims’ accounts (from online shopping to social media and even banks) usually by repeatedly trying to login with bad credentials. We can see this is a well-oiled, targeted operation, with carefully crafted email/SMS messages or even direct phone calls to victims. The scammer is able to optimize and raise the level of reliability to the point of no return.
Once the victim takes the bait, it’s usually game over. The scammer will do anything necessary to get the victim off the computer by finishing the cover story (giving the victim the tech support or refund they thought they needed). In some cases, we saw the gift-card redeem scam, in which the scammer pressures the victim into buying a small gift-card to confirm their credit and identity. And while the victim is off, searching for a local store to cashback the gift card, the scammers gets their hands on the prize, the unattended computer. Accounts are already logged into, no passwords are needed. And from here, well it’s a shopping frenzy. Tons of gift cards (to launder the money), wire transfer money, crypto-wallets take over, documents and files….
The last step was the most interesting, and the most unpleasant to discover during our analysis. The scammers create themselves a way back in, so that even if the victims find out and remove the RAT software at some point in the future, the scammer will be free to continue without interruption. It looks like scammers are using automated scripting (again, another feature of those RMM platforms) to quickly run a series of commands that re-configure services on the victim’s computer. The most common is altering their mailbox configuration by activating POP3 connection or just adding forward rules — meaning the scammer is able to read emails and even send emails under their victims' name! This is pure gold for massive account resets and 2FA bypass, allowing the theft of any account the victims had. Send a password reset request to PayPal, change the password and voila! The victim is now locked out of their own PayPal account. And not only that, from a PayPal perspective, this is all legit! It’s as if the victims themselves changed the password and moved money all around.
So now we know more or less how RATs are set up and run, let’s see how we can put our knowledge into action and stop these thieving so-and-so’s…
Guardio’s flagship product is a browser extension. This means Guardio keeps its users safe while they’re browsing, and can detect malicious activity and suspicious anomalies in real-time. With these capabilities, Guardio is able to recognize and stop malicious activity, like our RAT, at many checkpoints along the way. Some of these checkpoints are hard, absolute blocks, while others are heuristic, leveraging AI engines to detect anomalies and even prevent new, never-seen-before campaigns as well. As you can see below, Guardio is all over this funnel, able to intervene at almost any point:

Our initial investigation focused on incorporating DOM content sensors, along with other techniques used for segmenting sites that download RMM tools.
However, this was the easy part. Detecting malicious sites within this group is challenging because RATs are so widespread, and the use of all those remote software agents is totally legit. So simply blocking RATs is not even an option. We need to leverage our data-driven approach to hone in on the actual malicious occurrences. The optimized blocking mechanism required a cross-section of multiple data points based on the behavior of the sites and the users visiting those sites.
One of the data points we used, shown in the graph below, is the relation between the general behavior of the traffic to a site and the average number of times a single user visits this site.

On axis x, you can see the number of visits a single user typically makes to the site. We see that a regular RAT site is likely to have several visits from a single user, while a malicious version is much less likely to get multiple visits.
On axis y, the general behavior of traffic to a site is calculated using the formula:
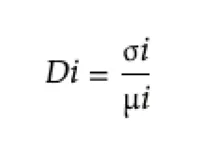
σi = Standard deviation of daily incoming traffic
μi = Mean of daily incoming traffic
The coefficient value is a representation of site activity. While Di<1 means the site is being visited in an equalized manner along the day and around the average value, and as much as Di is larger than 1, this means visits to the site are more scattered and change from the average in a dramatic way each time.
To initiate this type of attack, the scammer needs to be fully dedicated to one victim at a time, so it makes sense that at any given time, only one victim is being targeted, and there will be long and inconsistent gaps between visits (of different users) — meaning the activity coefficient will be higher.
And indeed, we can see in the scatter plot above how regular RAT sites behave (the green dots) while the training data of spotted malicious sites (red dots) are mostly clustered in the left-top part of the graph. The other green dots in the top left are actually also potential candidates for malicious RAT sites. As a result of crossing this data point with many other ones, Guardio can differentiate between legitimate and malicious sites that use RATs.
To get a taste of what we caught in our nets, here are some examples of large-scale campaigns. We can clearly see that the most powerful (and popular) platforms being abused are ConnectWise and Teamviewer.
In the case of ConnectWise, which also offers a web-portal landing page and numerous customization capabilities, we see large-scale operations with different cover stories. From refunds to technical PC support and general customer service, through to several specificly targeted brands, such as Amazon, Microsoft, GeekSquad, Norton, McAfee and many more. These sites, created quickly and easily by the scammers, are active and dynamic — changing from brand to brand as needed. And cleverly, they are “covered up” as the landing page becomes a generic site template when the scammers are not active. This is so that web crawlers won’t be alerted by those sites while not actively scamming. Yet another mechanism that shows us the level of sophistication we are up against here. You can see this here in this Amazon support RAT scam site — from a harmless landing page to a full-blown Amazon support wanna-be:

Here are some more examples of malicious sites of many kinds and usages that were found along the way and are already being blocked by Guardio:

There are hundreds of domains like this active at any moment of the day, moving and evolving on a daily basis. And we can also understand how widespread those attacks are by looking at the following heatmap of actual visits to malicious RAT sites in the last month alone:

Of course, all those sites are immediately blocked by Guardio once any connection or visit is being detected:

Guardio is now blocking those campaigns, and many others, so our customers are not able to accidently download and install a malicious remote agent. In addition, Guardio continuously monitors the activity of all the different RAT uses out there, correlating data with our heuristic detection engines from the entire landscape of attacks. This is how we’re making sure the dynamic nature of these campaigns doesn’t harm the detection rate — and helps us keep Guardio customers safe.
And always remember — get help or support only from people you trust! If you get a suspicious email or phone call offering remote support, call the real bank or company first and ask if the remote support is genuine. Very much a case of “Don’t call us, we’ll call you”.
